Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Descrição
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't

Thinking Strategically about Email Security in 2021 and Beyond - Guardian Digital .

4 Ways Hackers Bypass Fingerprint and Reputation Defense

4 best email security tools you need in your stack

Two New Platforms Found Offering Cybercrime-as-a-Service to 'Wannabe Hackers

Effective Strategies for Protecting Against BEC

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks

What is Phishing Email: Examples, Types, Techniques & more
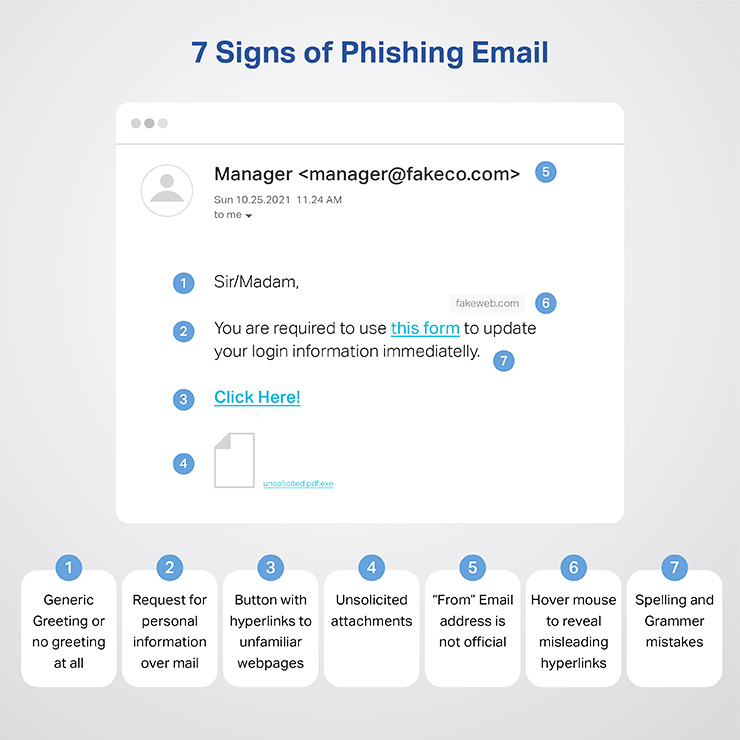
What is Phishing Email: Examples, Types, Techniques & more
20 Eye-Opening Cybercrime Statistics

Understanding Phishing Emails: Why They Slip Through Spam Filters

How to Measure Your Team's Email Security Savviness

Four ways cybercriminals can hack passwords
de
por adulto (o preço varia de acordo com o tamanho do grupo)