Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Toll fraud malware: How an Android application can drain your
SharkBot: a “new” generation Android banking Trojan being
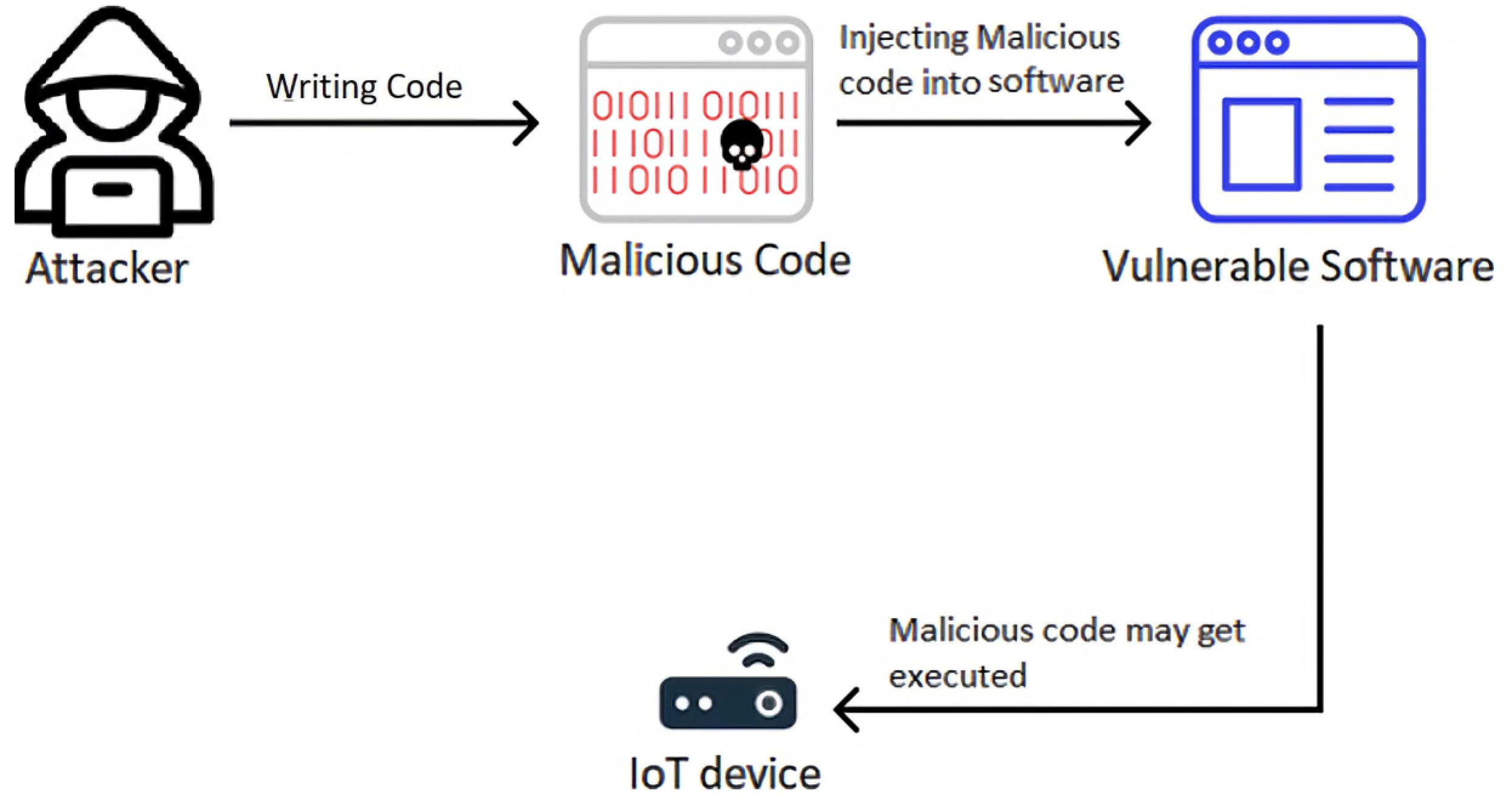
Sensors, Free Full-Text

Google Play threat market: overview of dark web offers

From GitHub to Account Takeover: Misconfigured Actions Place GCP

Quash EDR/XDR Exploits With These Countermeasures

Dynamic analysis and tampering
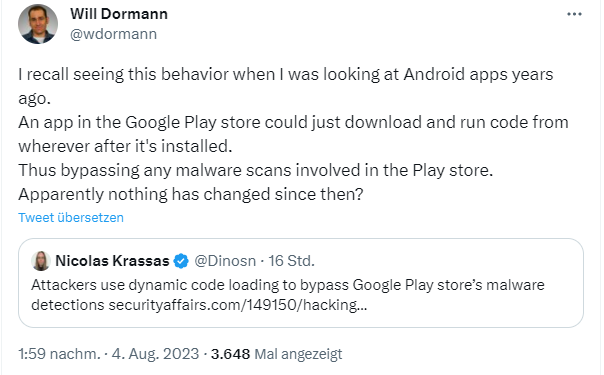
Bypass malware detection in Google Play Store with Dynamic Code

How cybercriminals evade mobile app store security measures

Android Applications Pentesting - HackTricks
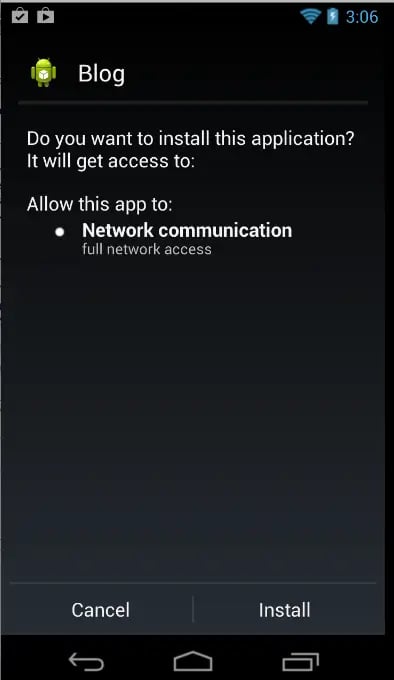
Bypassing The Android Permission Model

Cybersecurity News: June 19-25 Day 2021
Technologies, Free Full-Text
de
por adulto (o preço varia de acordo com o tamanho do grupo)