window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Descrição
Xiaoran Wang ([email protected]) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
GitHub - payloadbox/xss-payload-list: 🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List
GitHub - payloadbox/xss-payload-list: 🎯 Cross Site Scripting ( XSS ) Vulnerability Payload List
Installing support for WebDAV to access documents in Documents storage in Control Center or from File Explorer – NiceLabel Help Center

java - Invalid port. Exiting..Exception in thread main org.openqa.selenium.WebDriverException: Driver server process died prematurely ChromeDriver Selenium - Stack Overflow
Offensive-Payloads/Cross-Site-Scripting-XSS-Payloads.txt at main · InfoSecWarrior/Offensive-Payloads · GitHub
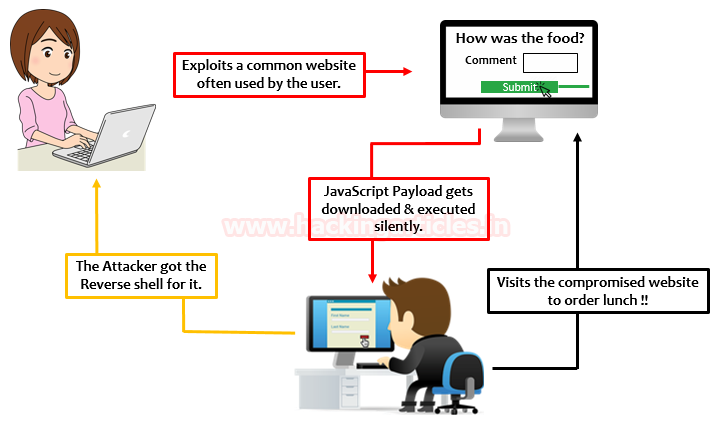
Cross-Site Scripting Exploitation - Hacking Articles
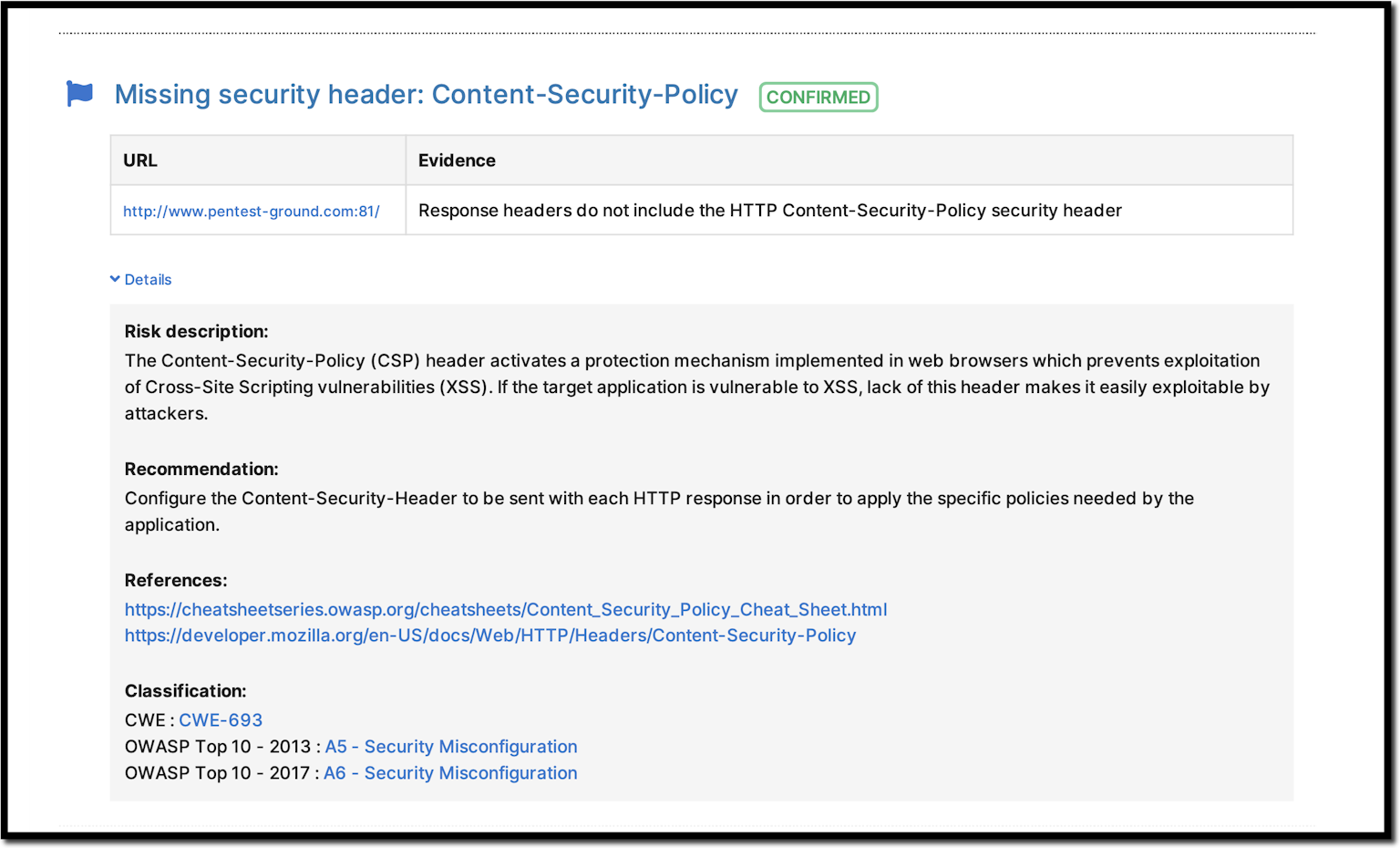
10 Practical scenarios for XSS attacks
writeups/bug.md at main · tess-ss/writeups · GitHub

JNDI-Related Vulnerability Discovered in H2 Database Console

Web Security Academy Lab solution: ” Reflected XSS into HTML context with most tags and attributes blocked”, by Nidal Mahmud

Office 365 Hacked Using Google Open-Redirect Vulnerability
de
por adulto (o preço varia de acordo com o tamanho do grupo)

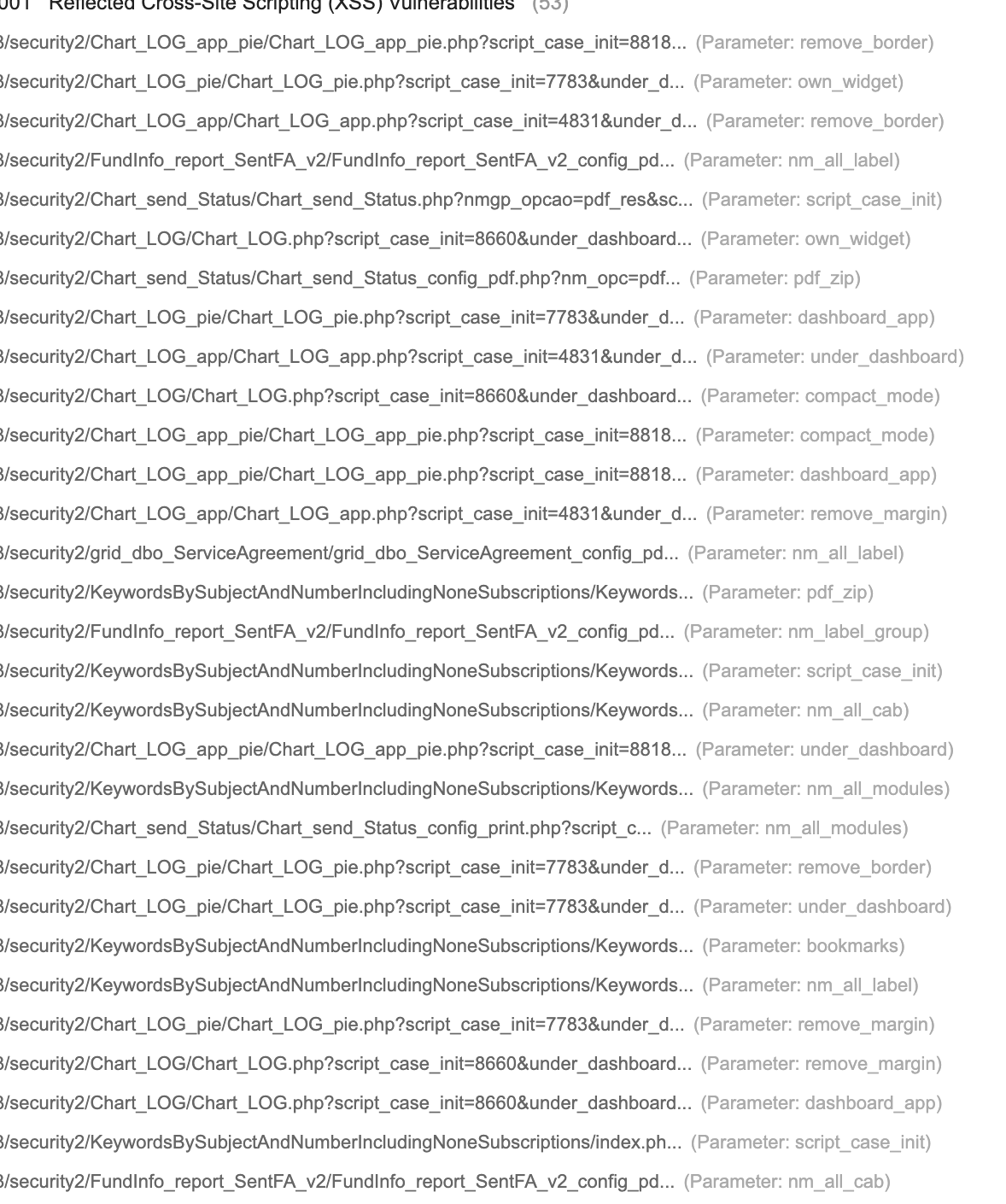




format(webp))