Hack Attacks Testing How to Conduct Your - Back to Home
Por um escritor misterioso
Descrição
Hack Attacks Testing How to Conduct Your - Back to Home

10 Most Common Types of Cyber Attacks Today - CrowdStrike
Discord Virus explained: How to Remove it?
What is Penetration Testing and How Does It Work?
Vulnerability in Cyber Security - A Step-by-Step Guide for Beginners
Highlight, take notes, and search in the book In this edition, page numbers are just like the physical edition

Cybersecurity Attacks – Red Team Strategies: A practical guide to building a penetration testing program having homefield advantage
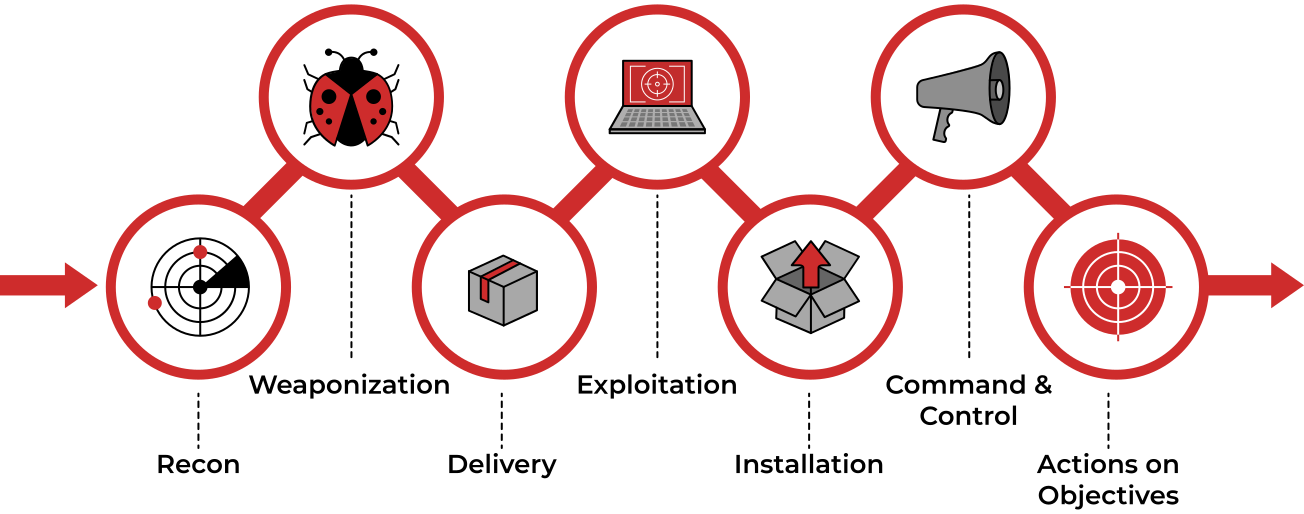
TryHackMe Cyber Kill Chain Room. The Cyber Kill Chain framework is…, by Haircutfish
What Is Penetration Testing?

6 Things You Need to Do to Prevent Getting Hacked

15 Surprisingly Hackable Things at Work

Recognizing the seven stages of a cyber-attack - DNV
de
por adulto (o preço varia de acordo com o tamanho do grupo)