Piggybacking Attack in the Context of Cybersecurity
Por um escritor misterioso
Descrição
Piggybacking is a cybersecurity risk that can lead to unauthorized access exploiting legitimate users. Prevent it now!
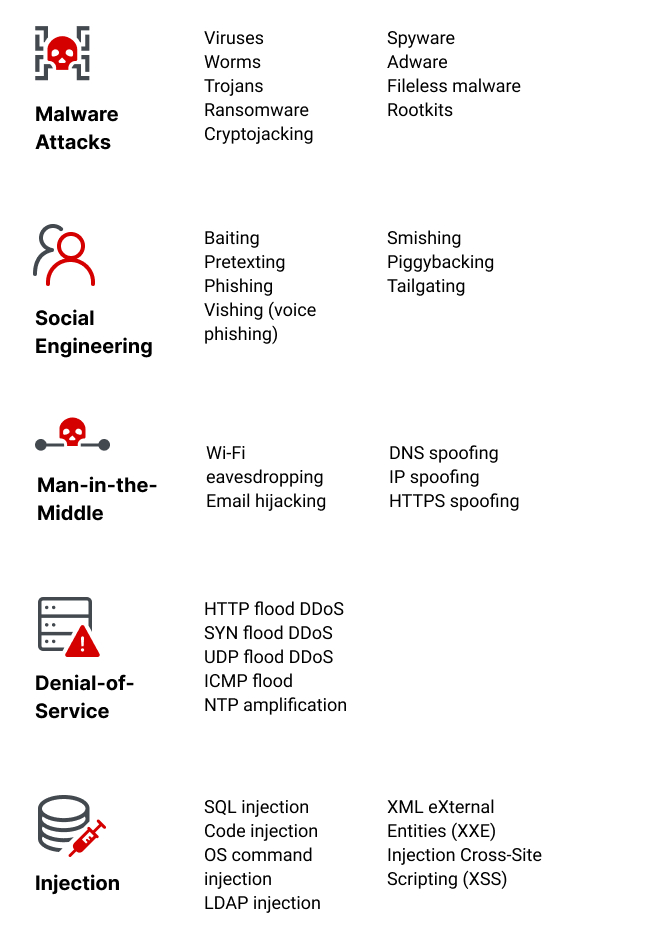
Cybersecurity Threats, Types & Sources

Supplementary Report: Cyber Resilience and Financial Organizations - Carnegie Endowment for International Peace
How to Prevent Tailgating Attacks: The Five-Minute Guide
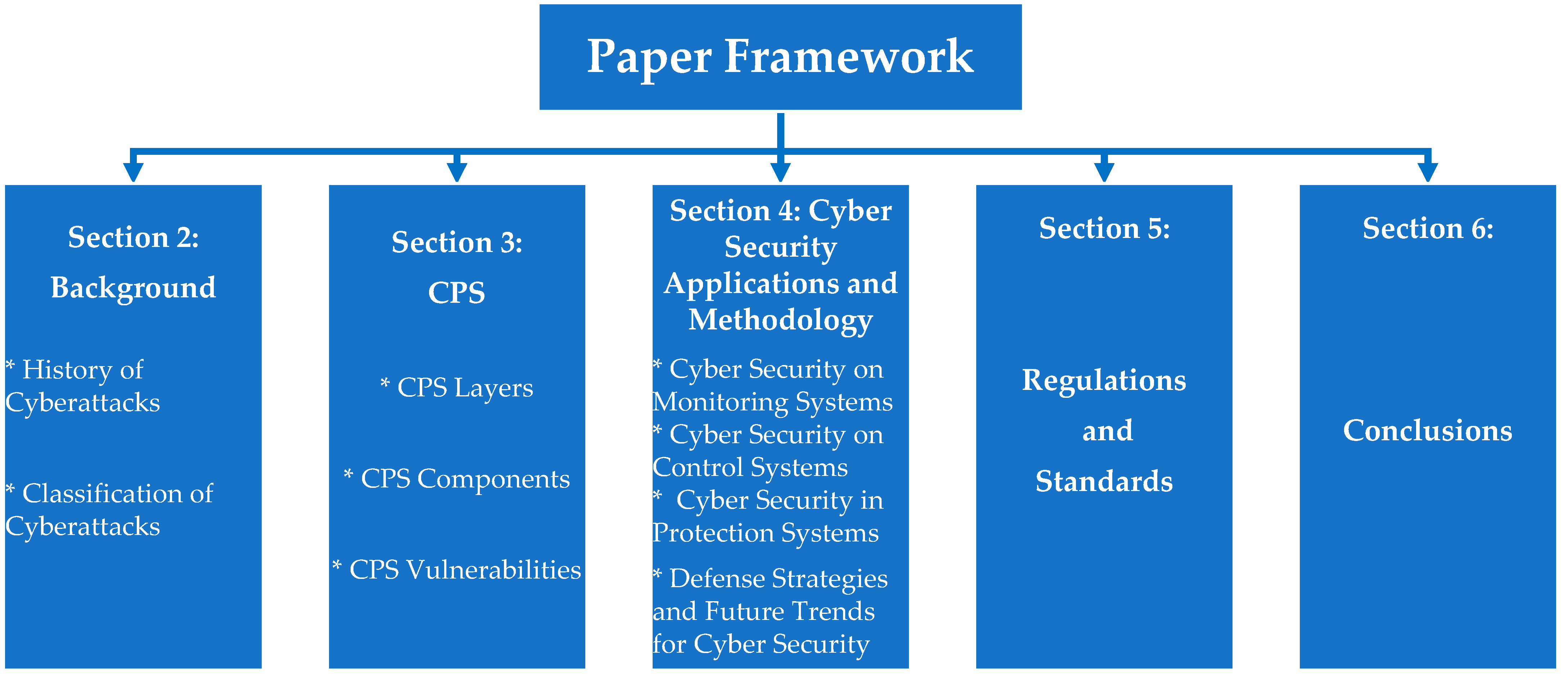
Energies, Free Full-Text

What is Tailgating Attack
The History Of Cybercrime And Cybersecurity, 1940-2020

A Brief History of Cybersecurity

Cyber security of railway cyber-physical system (CPS) – A risk management methodology - ScienceDirect

What Is Social Engineering? - Definition, Types & More

Frontiers Handling User-Oriented Cyber-Attacks: STRIM, a User-Based Security Training Model
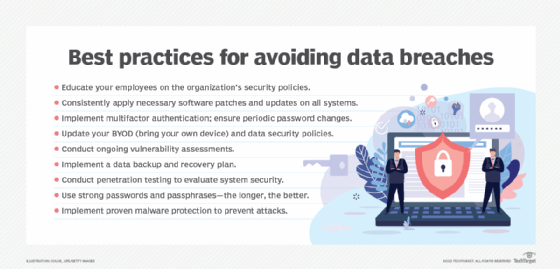
What is tailgating (piggybacking) and how to prevent it?
de
por adulto (o preço varia de acordo com o tamanho do grupo)







