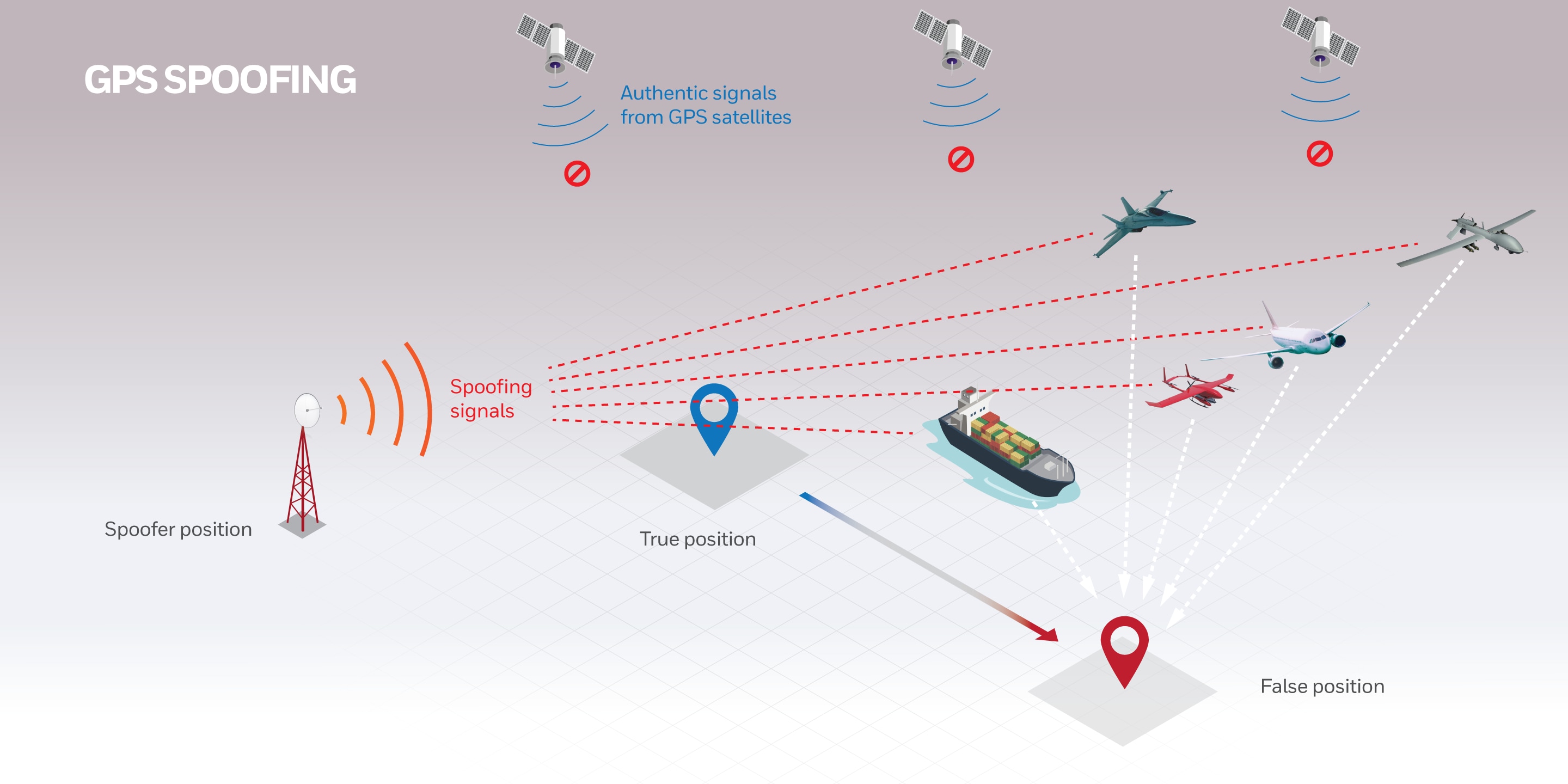
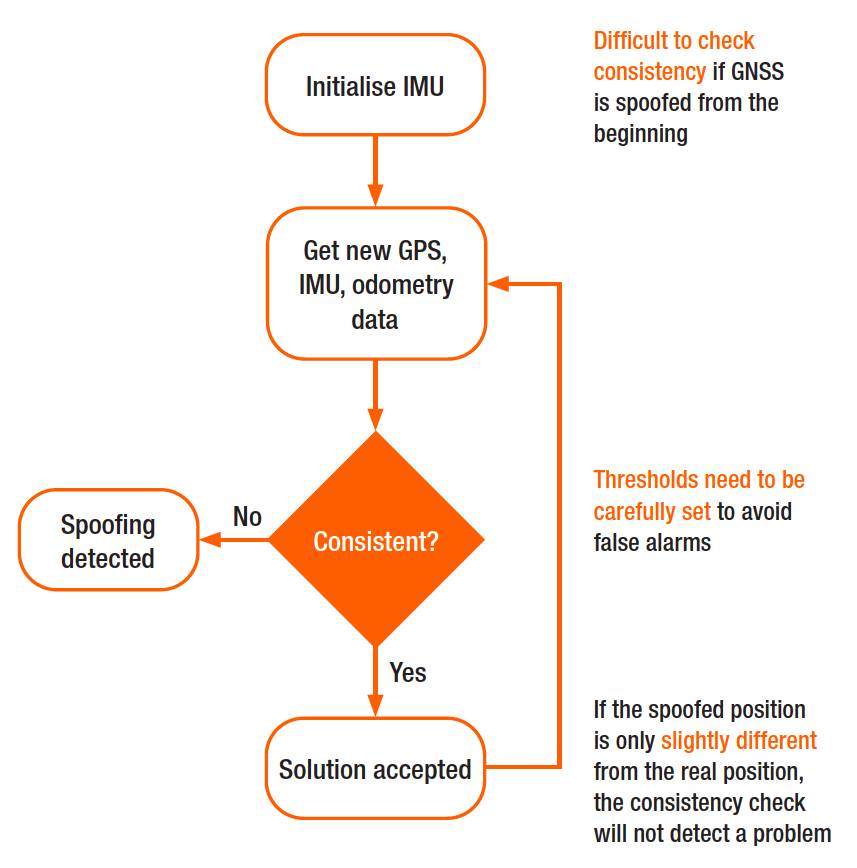
GootBot - Gootloader's new approach to post-exploitation
Por um escritor misterioso
Descrição
IBM X-Force discovered a new variant of Gootloader — the "GootBot" implant. Learn more about this and how to combat it.

Gootloader” expands its payload delivery options – Sophos News
IBM X-Force Discovers Gootloader Malware Variant- GootBot
GootBot: A Stealthy Game Changer in Malware - PureVPN Blog

Apple Crimeware Massive Rust Infostealer Campaign Aiming for macOS Sonoma Ahead of Public Release : r/worldTechnology

cisa podcasts

How human behavior research informs security strategies: Kai Roer explains., CyberCureME - Cyber Security Marketplace posted on the topic

eSentire GootLoader Expands its Payloads Infecting a Law Firm with…

X-Force (XForce@) / X

cisa podcasts
GootBot - Gootloader's new approach to post-exploitation
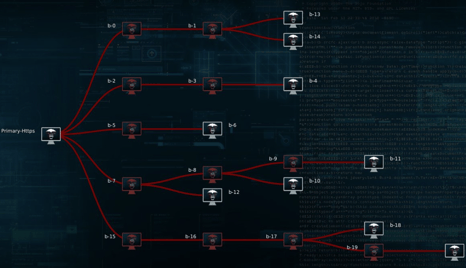
The Rise of Post-Exploitation Attack Frameworks

Pre-authenticated RCE in VMware vRealize Network Insight : r/worldTechnology
de
por adulto (o preço varia de acordo com o tamanho do grupo)