Delay-CJ: A novel cryptojacking covert attack method based on
Por um escritor misterioso
Descrição
Cryptojacking is a type of resource embezzlement attack, wherein an attacker secretly executes the cryptocurrency mining program in the target host to…
CPU behavior while the sohu.com page is being loaded

US7779121B2 - Method and apparatus for detecting click fraud - Google Patents

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect
WR.1943-5452.0001265/asset/cb7a57af-5a2c-4ed9-8f84-a45c7a67946c/assets/images/large/figure4.jpg)
Review of Modeling Methodologies for Managing Water Distribution Security, Journal of Water Resources Planning and Management

Comparison of CPU usage of browser without and with browser mining

Coinhive dashboard showing the earnings of a domain parking service
WR.1943-5452.0001265/asset/0ce00df7-f33a-4ee9-a8f5-1a9b4ed1e673/assets/images/large/figure3.jpg)
Review of Modeling Methodologies for Managing Water Distribution Security, Journal of Water Resources Planning and Management
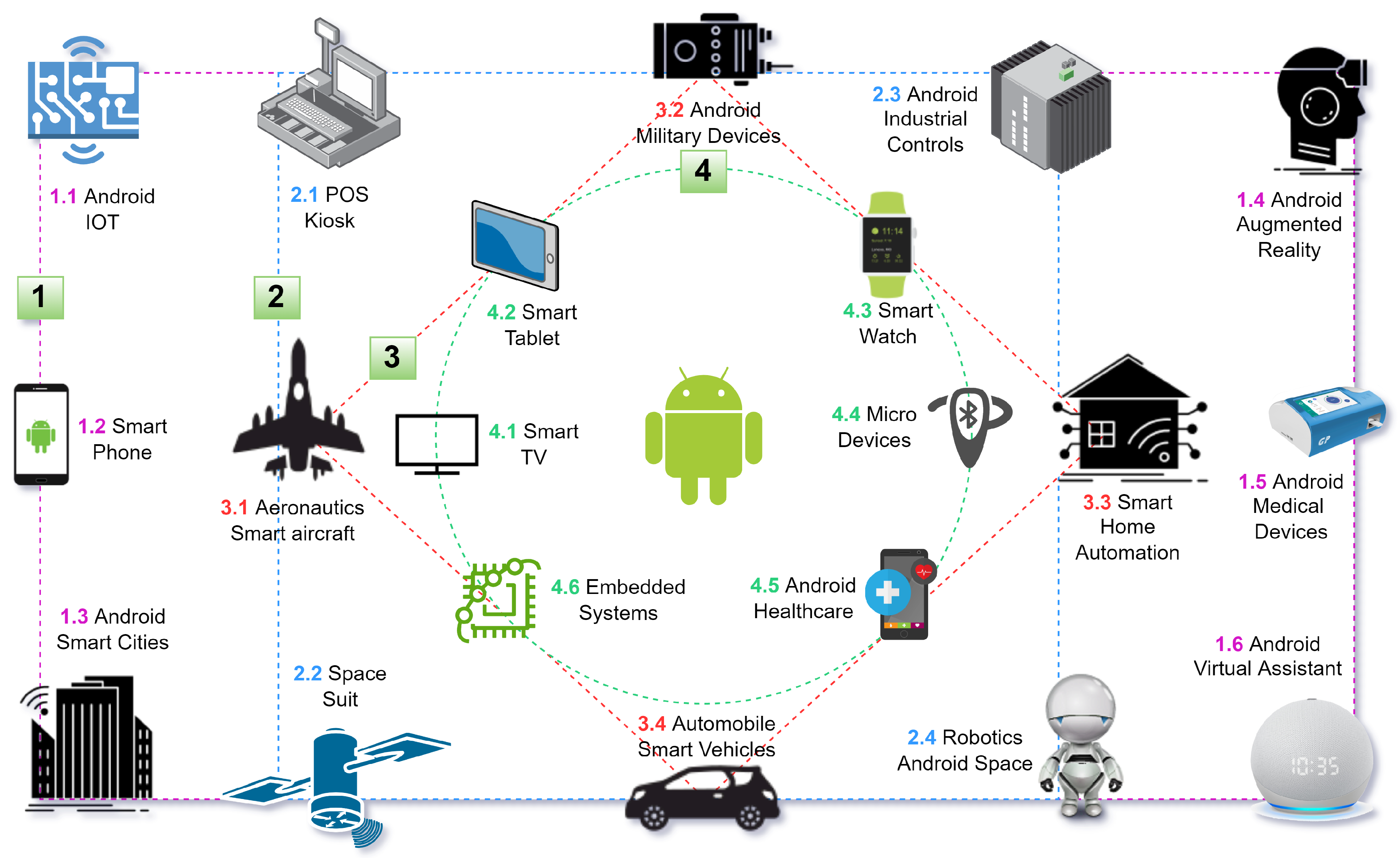
Technologies, Free Full-Text

Delay-CJ: A novel cryptojacking covert attack method based on delayed strategy and its detection - ScienceDirect

CyberWire Daily - Podcast

SVM stratified 10-fold cross validation

PDF] CoinPolice: Detecting Hidden Cryptojacking Attacks with Neural Networks
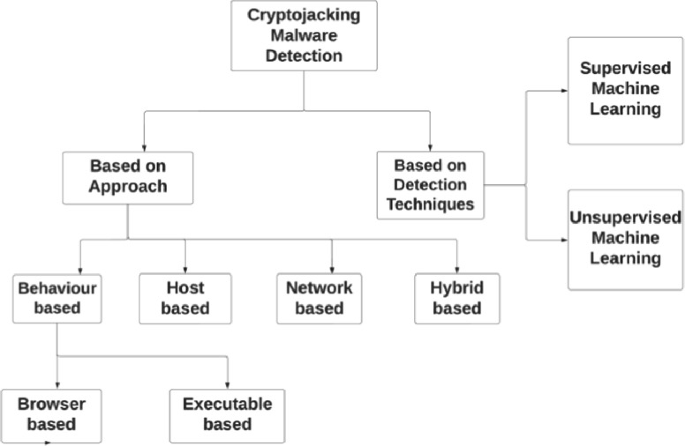
Variants of Crypto-Jacking Attacks and Their Detection Techniques

The Anomali Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)







