Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Descrição

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

Disarming visualization-based approaches in malware detection systems - ScienceDirect
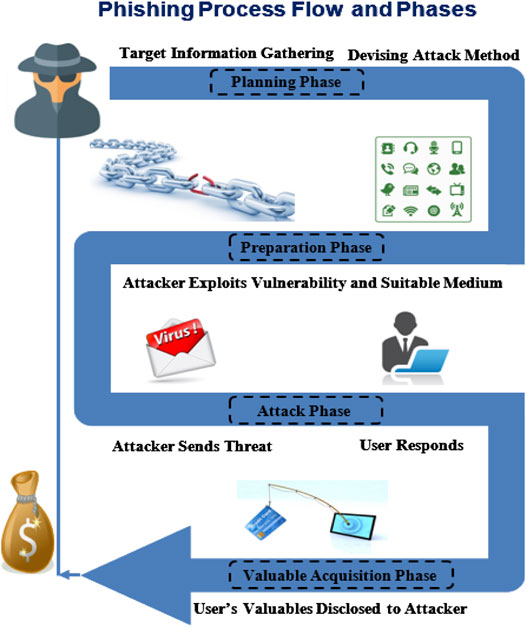
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

Evolution toward intelligent communications: Impact of deep learning applications on the future of 6G technology - Abd Elaziz - WIREs Data Mining and Knowledge Discovery - Wiley Online Library
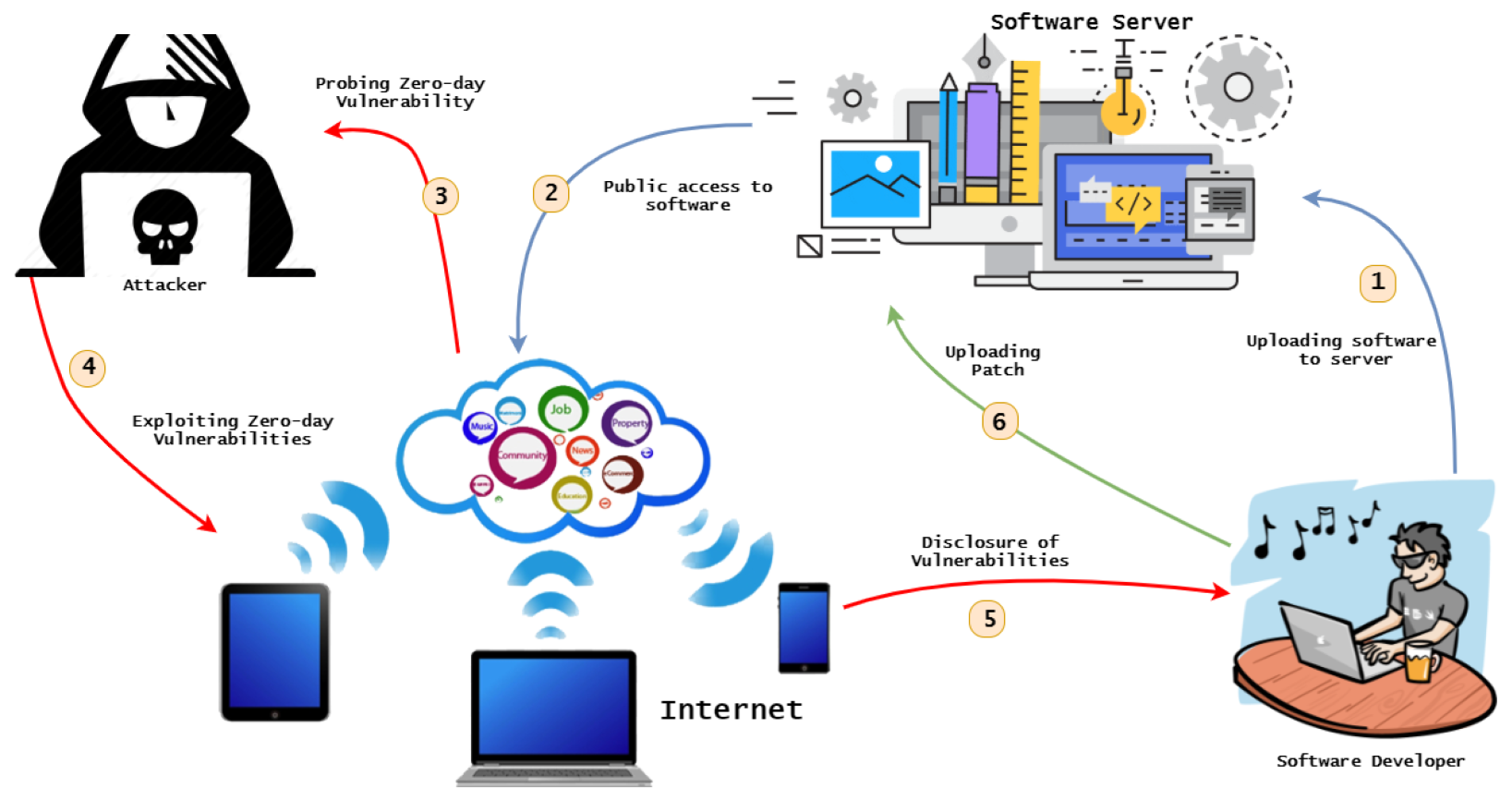
Electronics, Free Full-Text

PDF) BejaGNN: Behavior-based Java Malware Detection via Graph Neural Network
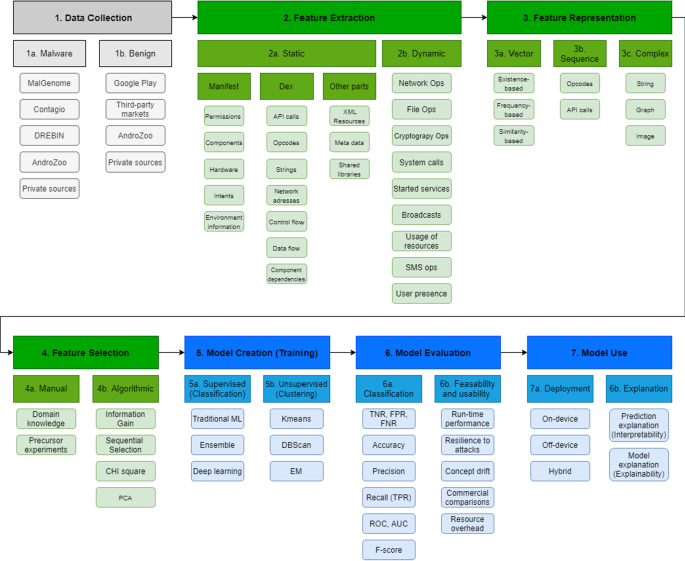
On building machine learning pipelines for Android malware detection: a procedural survey of practices, challenges and opportunities, Cybersecurity

Exploring Prompt Injection Attacks, NCC Group Research Blog

IICE-2022 Another 300x250-01 - Infonomics Society
de
por adulto (o preço varia de acordo com o tamanho do grupo)