How hackers use idle scans in port scan attacks
Por um escritor misterioso
Descrição
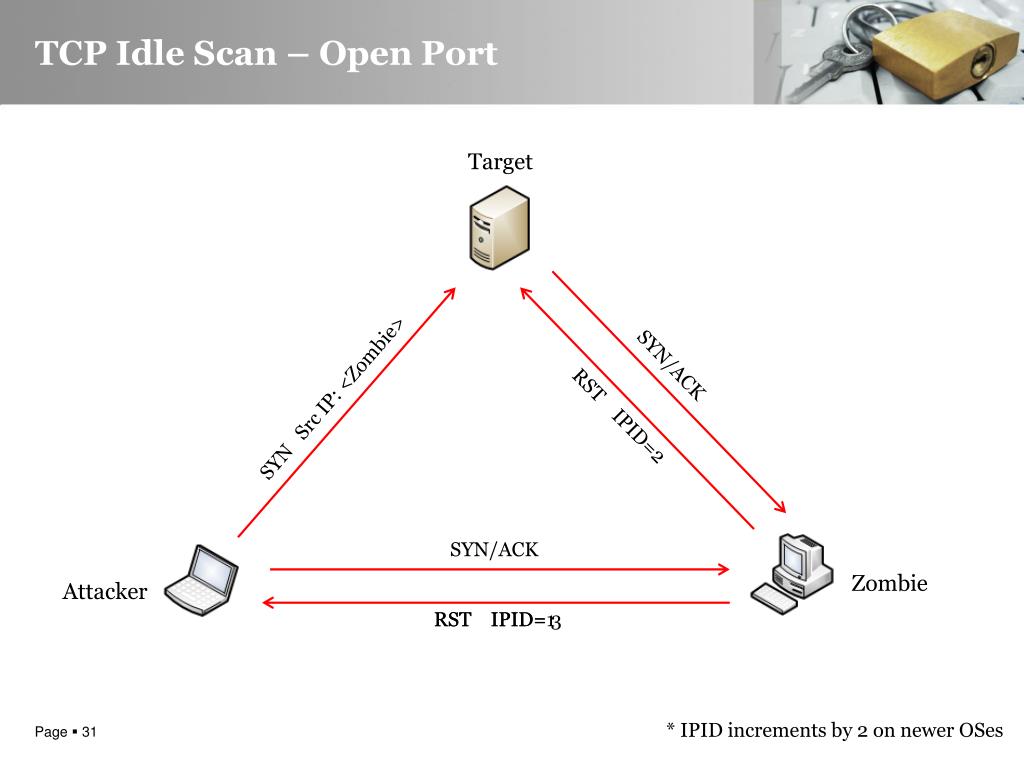
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
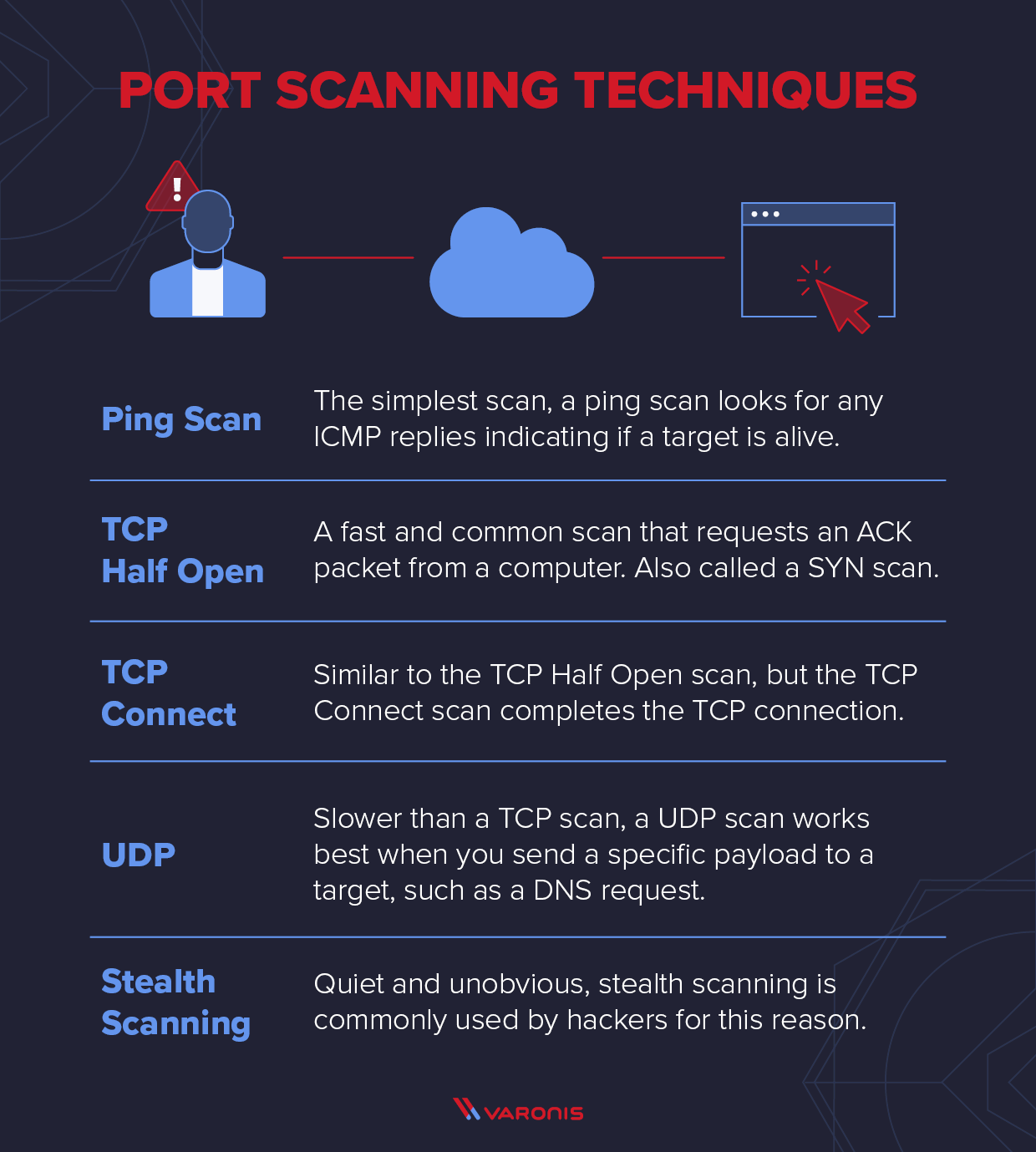
What is a Port Scanner and How Does it Work?
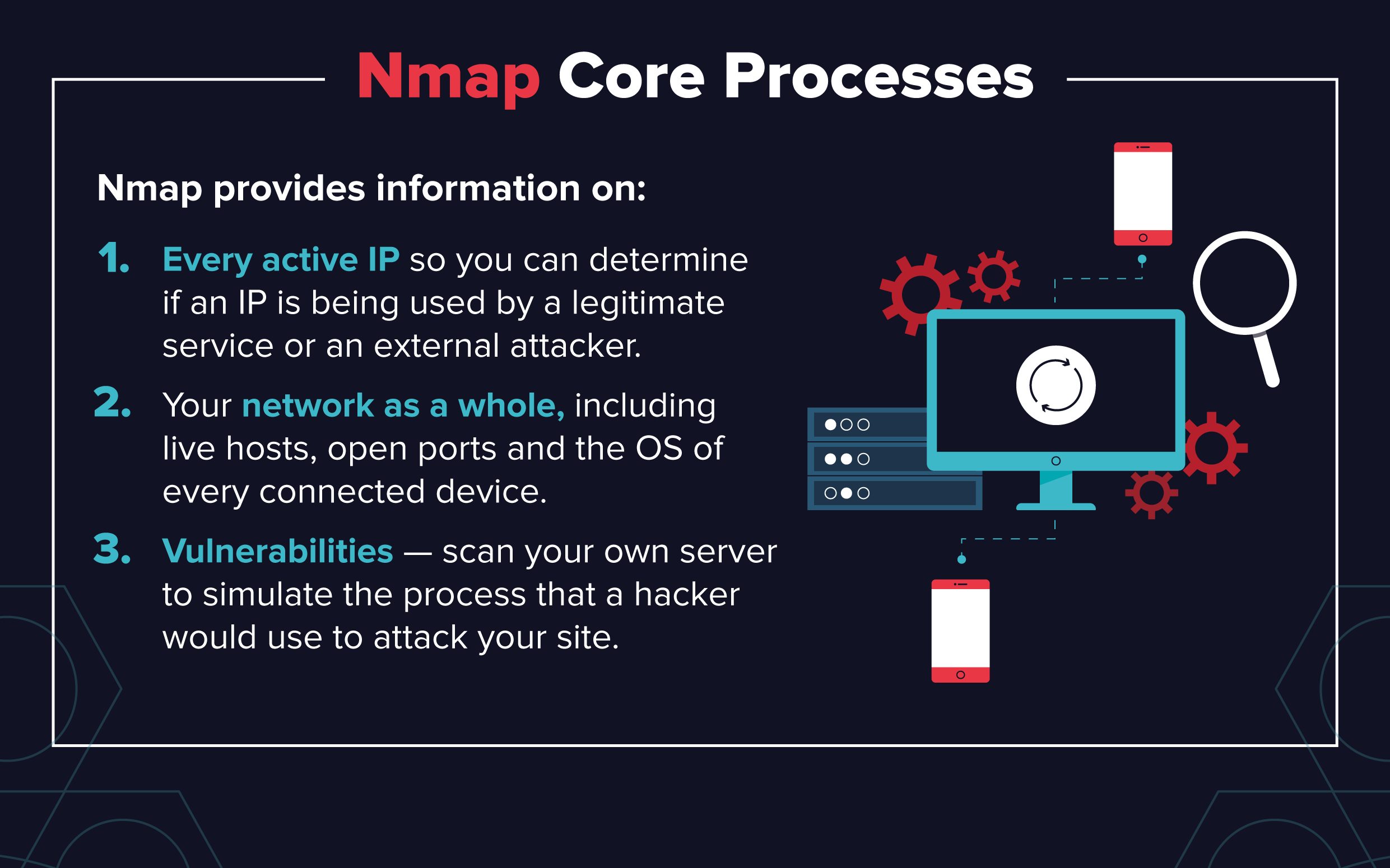
Essential Nmap Commands for System Admins - Penetration Testing Tools, ML and Linux Tutorials

How hackers use idle scans in port scan attacks
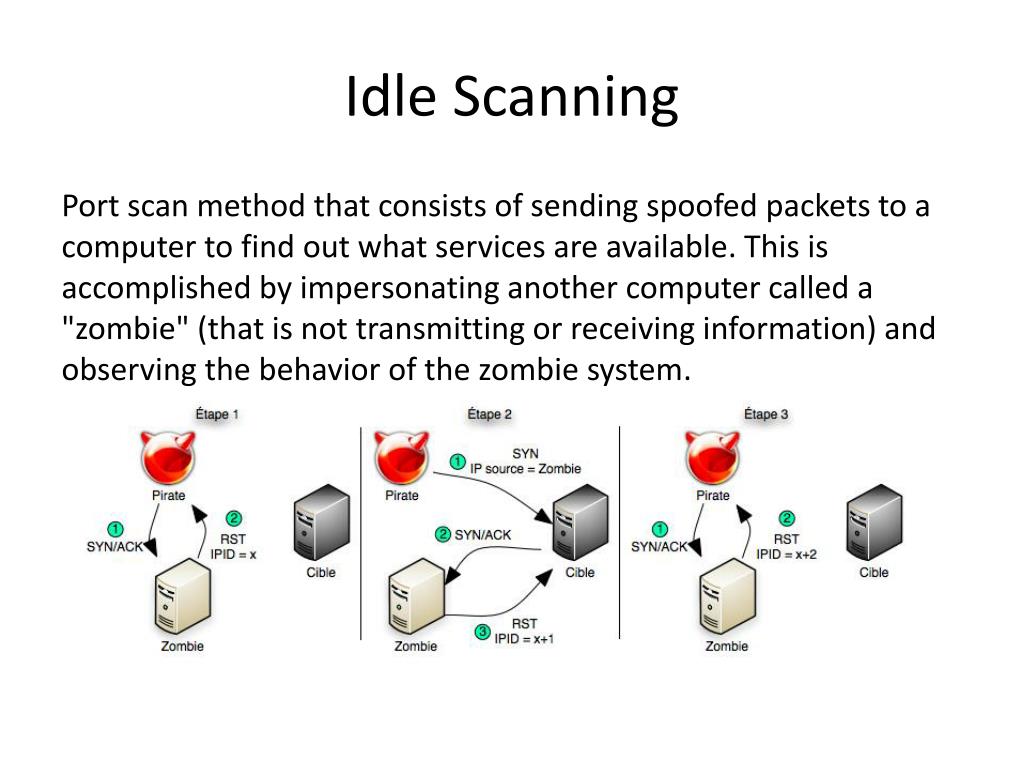
PPT - Port Scanning PowerPoint Presentation, free download - ID:1577632

NMap 101: Fun With Firewalls! HakTip 102
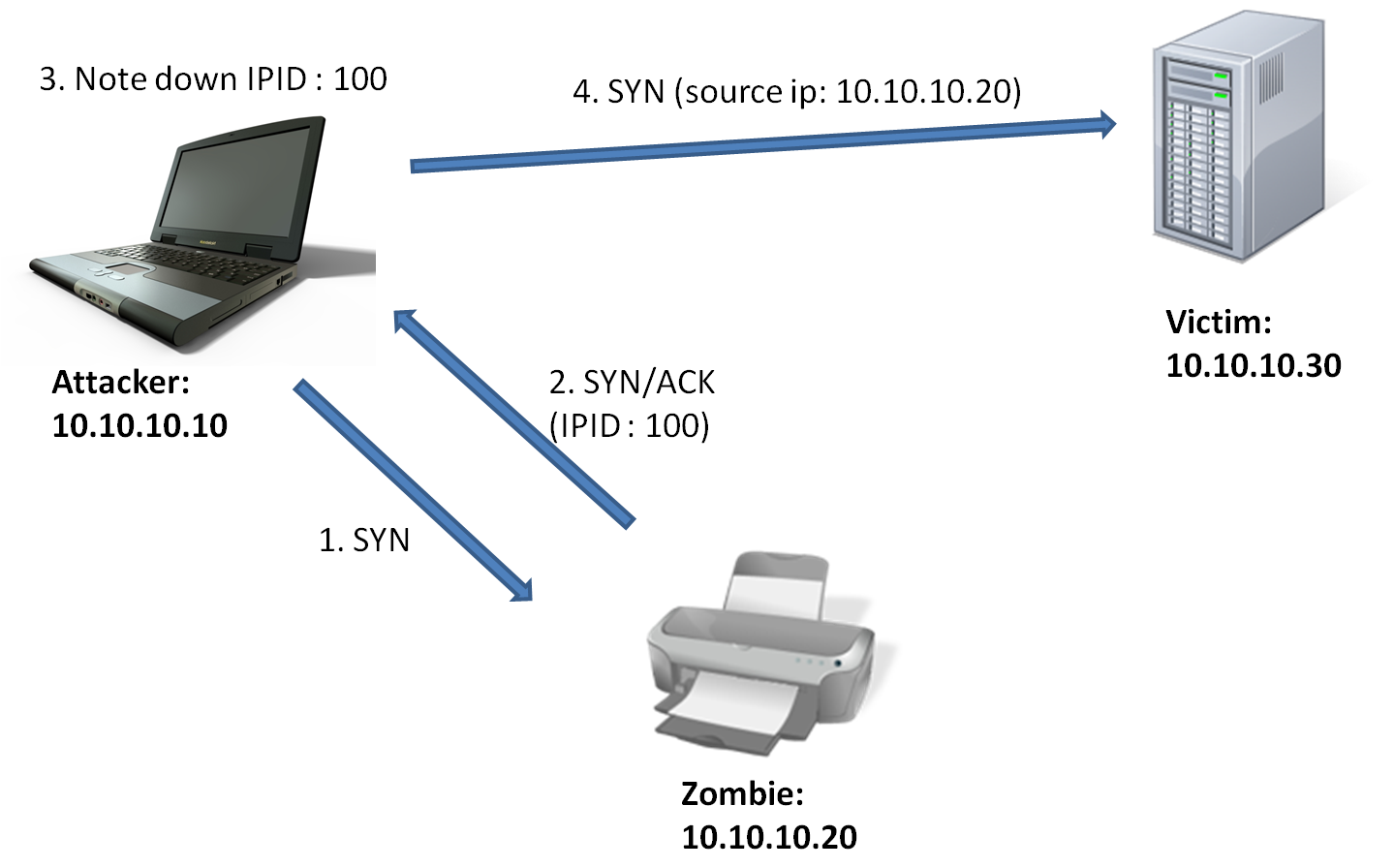
Vipul Chaskar's Blog: How does idle scan work?

What is a Port Scanner and How Does it Work?
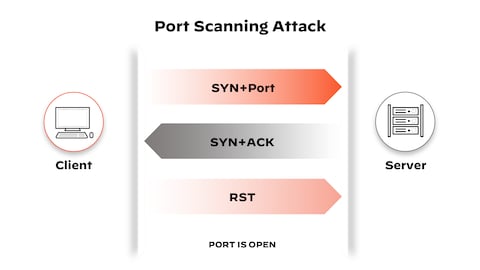
What is a Port Scan? - Palo Alto Networks
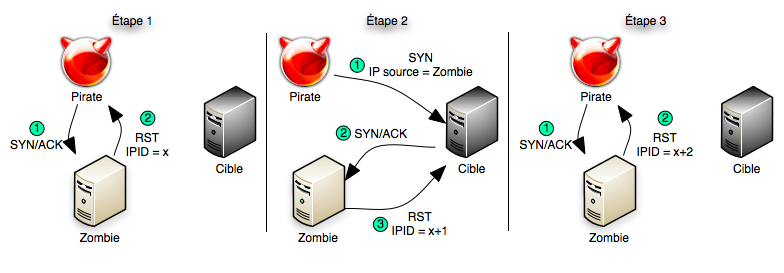
Idle scan - Wikipedia
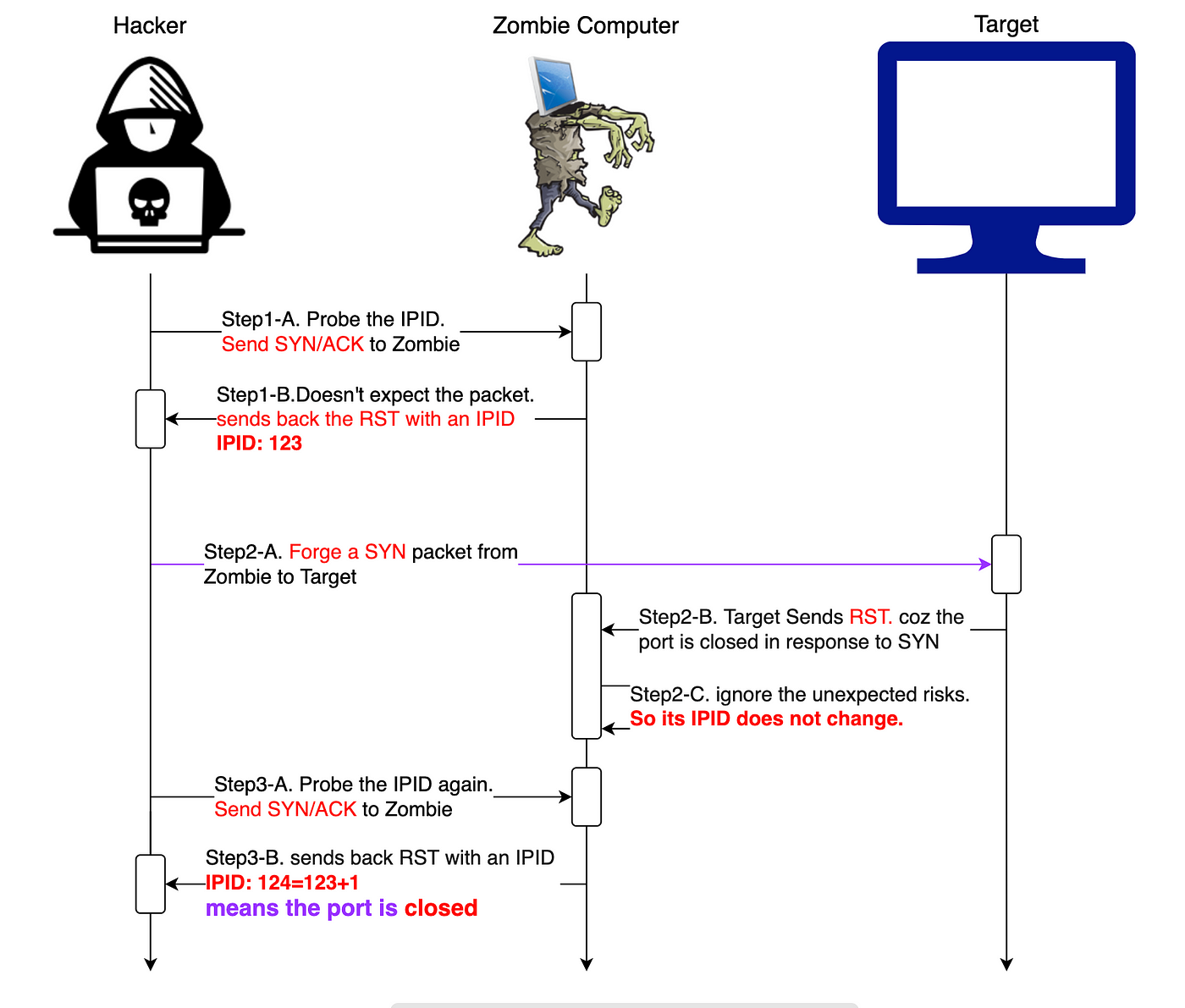
Zombie/Idle scan working principle, by NGU

PPT - Port Scanning PowerPoint Presentation, free download - ID:4633948

Nmap cheat sheet: From discovery to exploits, part 2: Advance port scanning with Nmap and custom idle scan

The Ultimate Guide to Port Scanning using Nmap
PPT - Advanced Idle Scanning PowerPoint Presentation, free download - ID:5241398
de
por adulto (o preço varia de acordo com o tamanho do grupo)