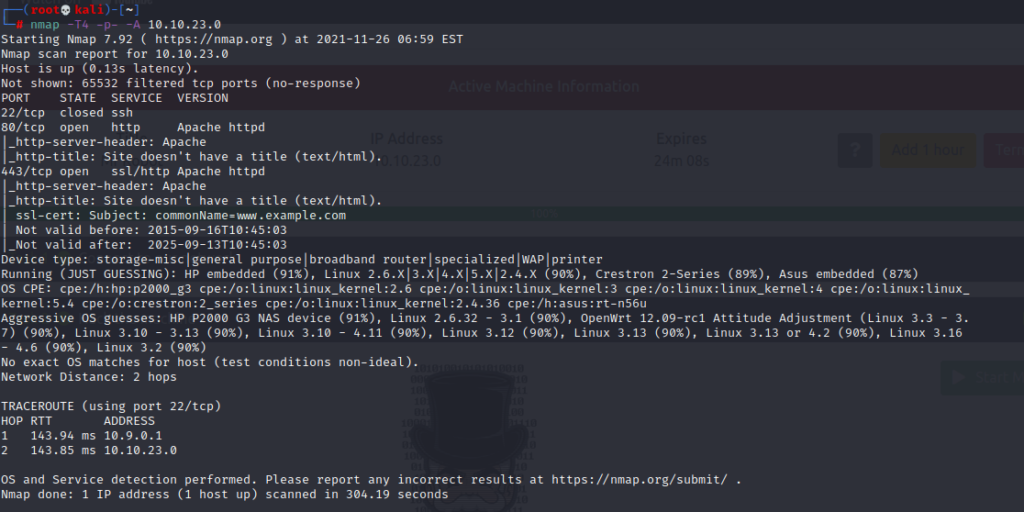
Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Descrição

Subterfuge (Man-in-the-Middle Attack Framework) - Hacking Articles

Xiangyu Qi - CatalyzeX
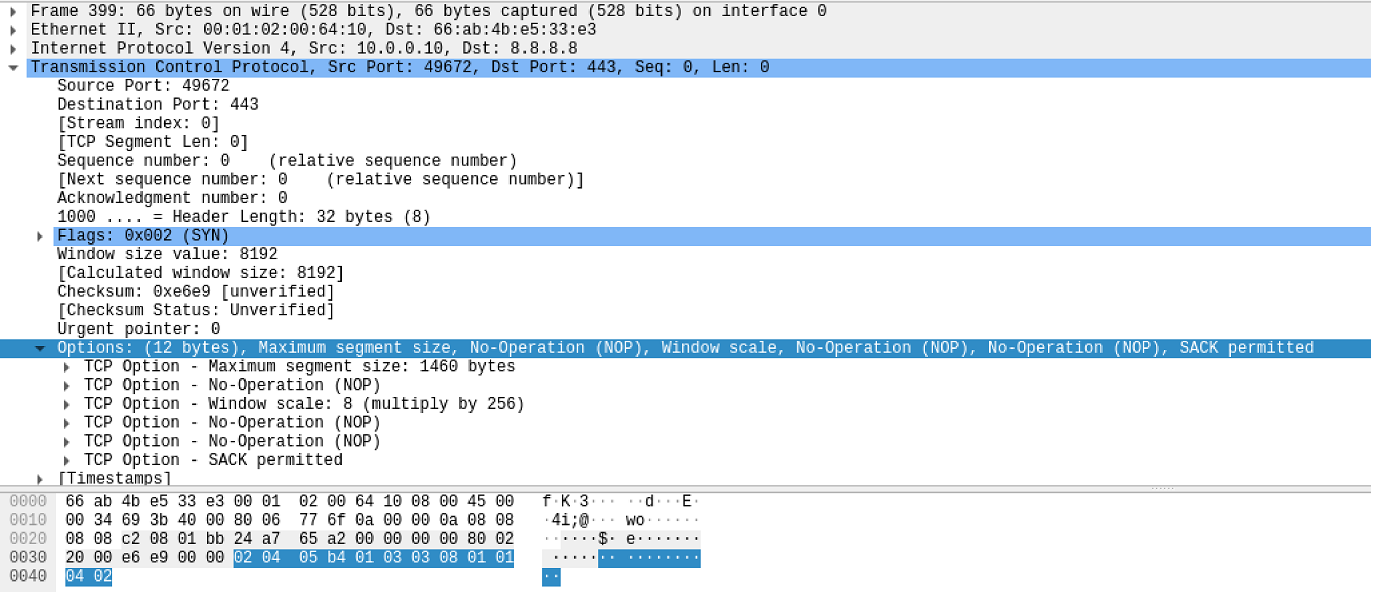
Kung fu enumeration. Data collection in attacked systems – HackMag
Find out if you have what it takes to keep the bad guys out of your network. This real-world resource contains 20+ hacking challenges for you to

Hacker's Challenge : Test Your Incident Response Skills Using 20 Scenarios

HACKMAGEDDON – Information Security Timelines and Statistics

Hamby's Tiger & Crane Kung Fu - Vol-7 12 Bridge Hands (Steel
AppSec Ezines Url ( from
AppSec Ezines Url ( from

HACKMAGEDDON – Information Security Timelines and Statistics
de
por adulto (o preço varia de acordo com o tamanho do grupo)