Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

The Evolution of Cyber Threats
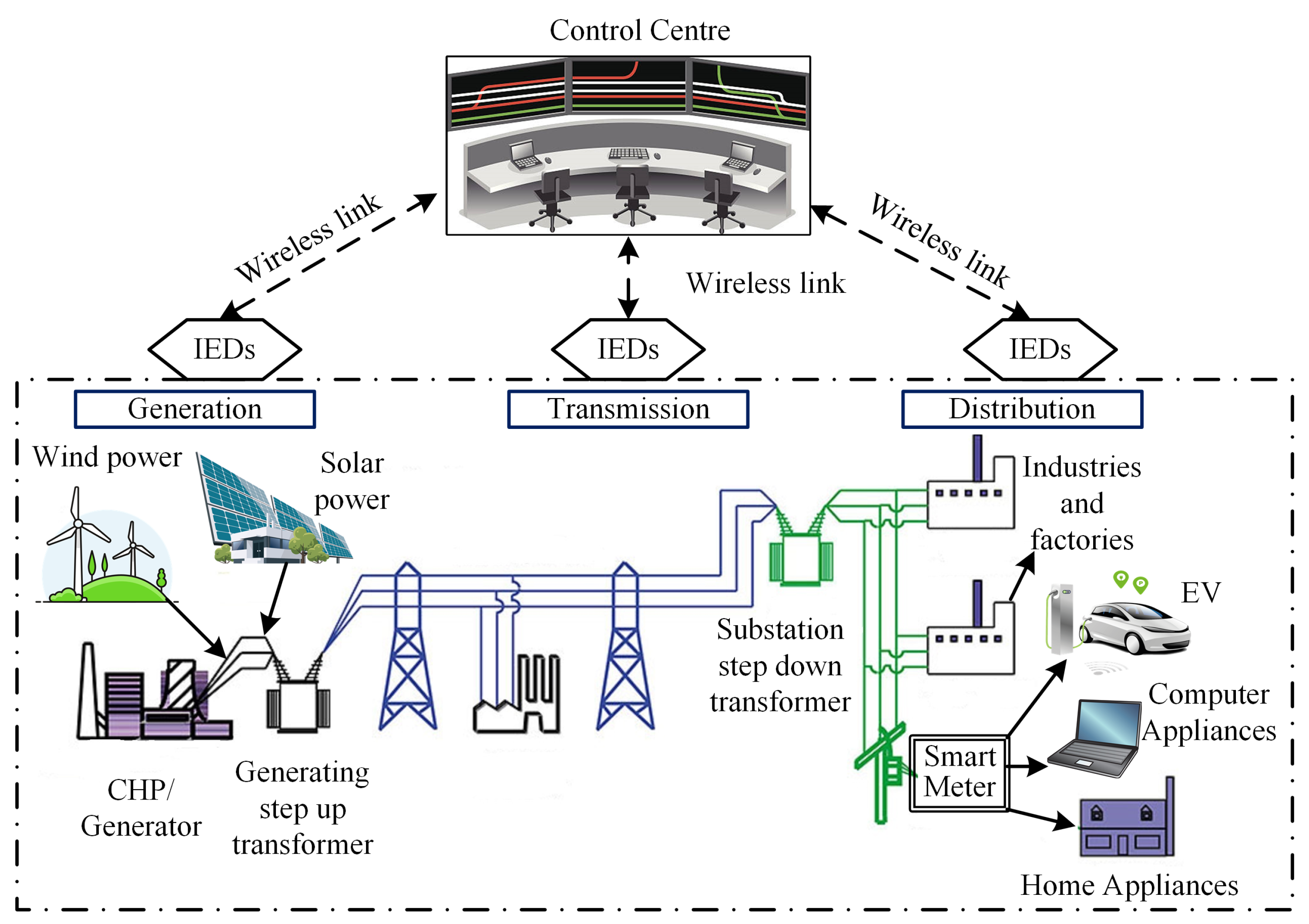
Electronics, Free Full-Text

Computer security - Wikipedia

Enterprise data breach: causes, challenges, prevention, and future

Privilege Escalation Attack and Defense Explained

Memory-based attacks increase as attackers dodge cloud defenses
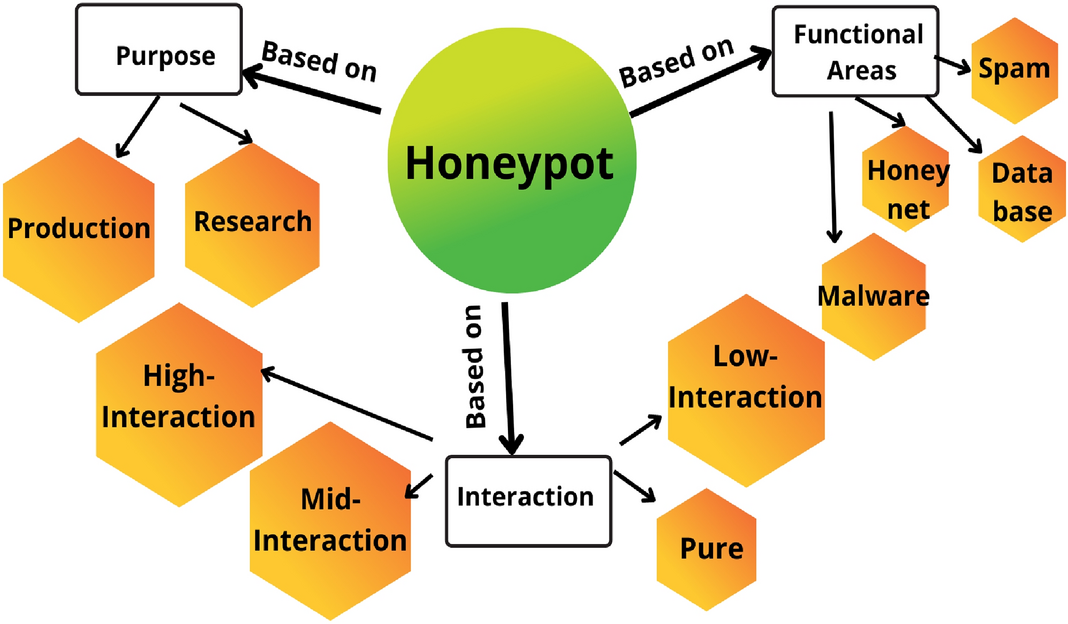
Containerized cloud-based honeypot deception for tracking
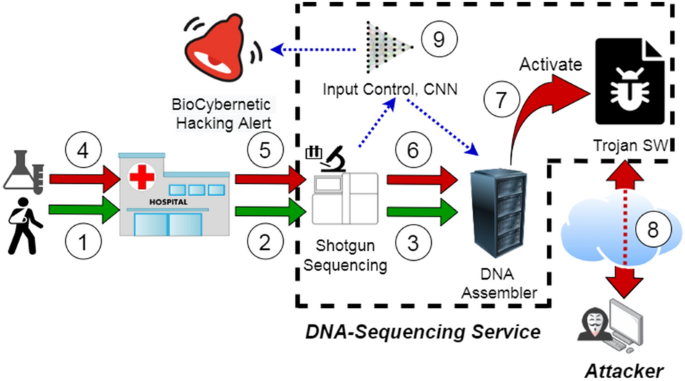
Using deep learning to detect digitally encoded DNA trigger for

How Hackers Rob Banks, 2018-05-21

The Growing Threat of Fileless Attacks: Insights on Cybersecurity

CrowdStrike Uses Similarity Search to Detect Script-Based Malware

Major surge in memory-based attacks as hackers evade traditional

Runtime Attacks In-Memory Require a Different Response

What is Malware? - Types, Examples, and Prevention
de
por adulto (o preço varia de acordo com o tamanho do grupo)