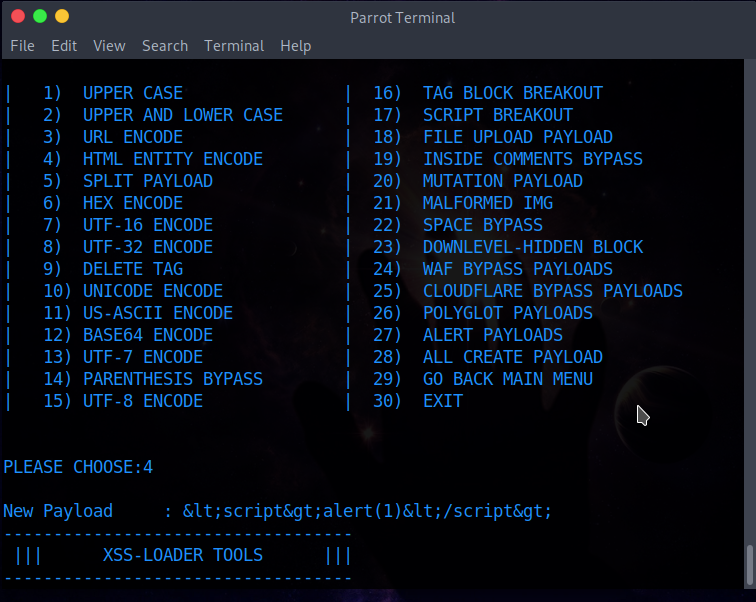
XSS Filters: Beating Length Limits Using Shortened Payloads
Por um escritor misterioso
Descrição
XSS Filters: Beating Length Limits Using Shortened Payloads The most obvious method when attempting to beat a filter that truncates your input to a fixed
js-xss/benchmark/file.html at master · leizongmin/js-xss · GitHub
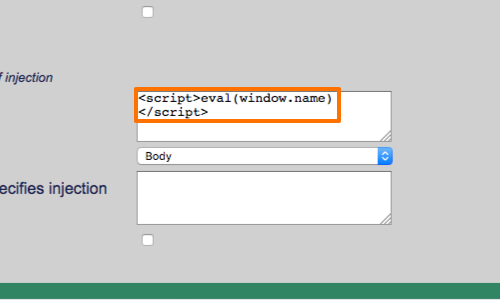
XSS Filters: Beating Length Limits Using Shortened Payloads - PortSwigger
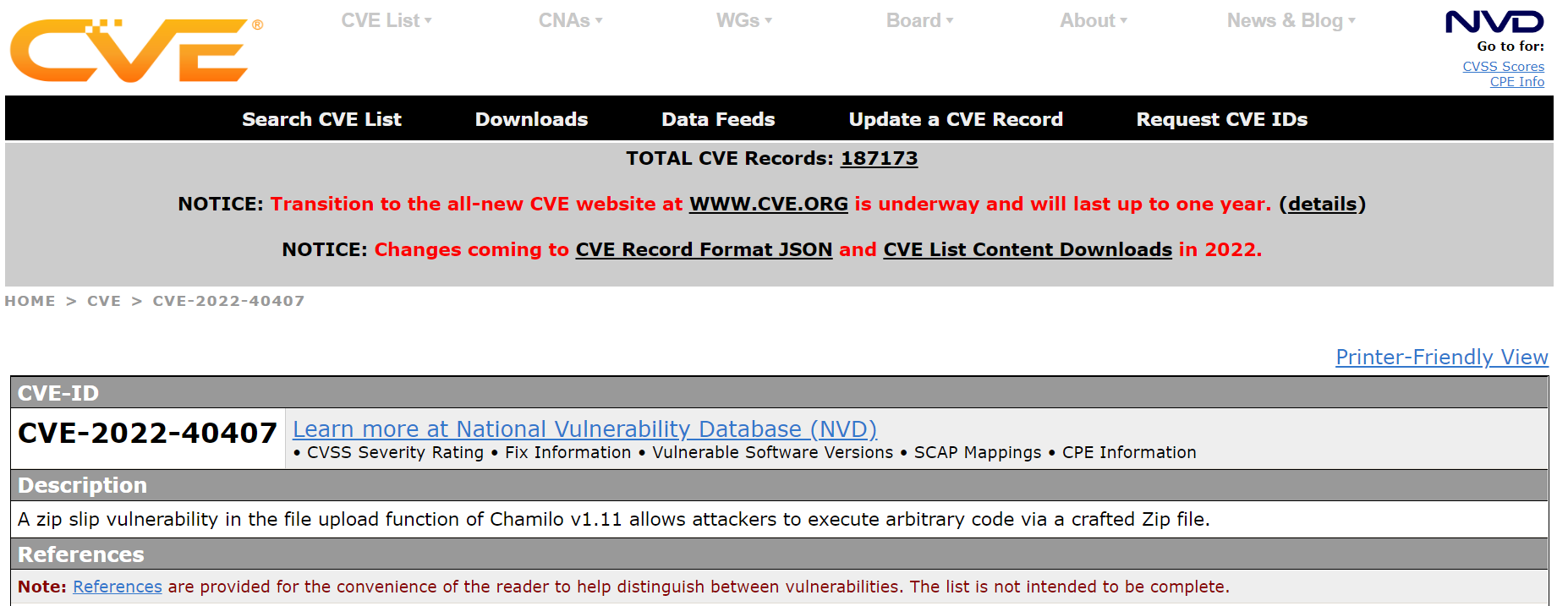
Security – simpleisbest.co.uk
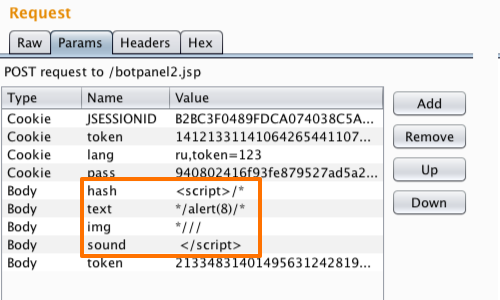
XSS Filters: Beating Length Limits Using Spanned Payloads - PortSwigger
What are some ways of protecting against cross-site scripting (XSS) injection through cookies? - Quora

ZTWeb: Cross site scripting detection based on zero trust - ScienceDirect
PDF) Precise XSS detection and mitigation with Client-side Templates
Auth0 Changelog
What is stored cross-site scripting? - Quora

Ch 12 Attacking Users - XSS

PDF) Code Injection Vulnerabilities in Web Applications - Exemplified at Cross-site Scripting
de
por adulto (o preço varia de acordo com o tamanho do grupo)