Do Not Cross The 'RedLine' Stealer: Detections and Analysis
Por um escritor misterioso
Descrição
The Splunk Threat Research Team provides a deep dive analysis of the RedLine Stealer threat and shares valuable insights to help enable blue teamers to defend against and detect this malware variant.
Trellix Global Defenders: Invasion of the Information Snatchers - Protecting against RedLine Infostealer

Advice For Catching a RedLine Stealer, by John F, Oct, 2023
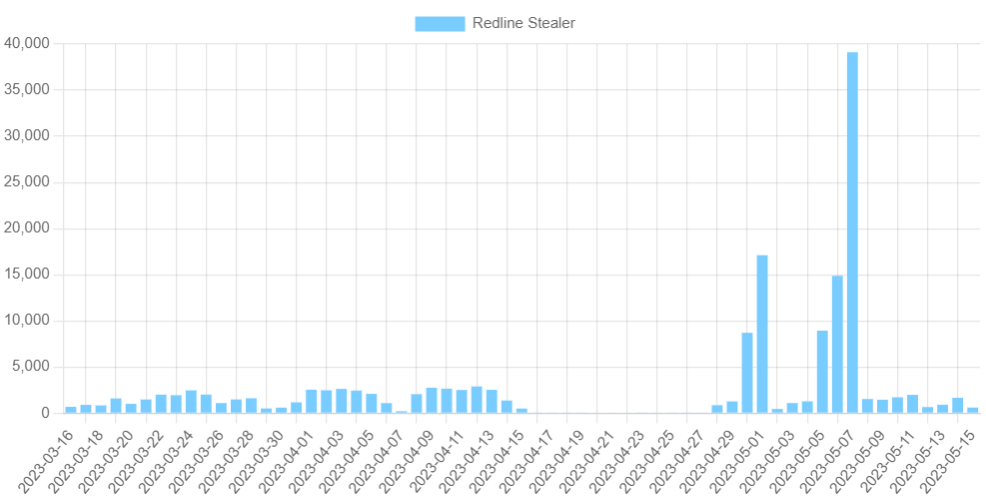
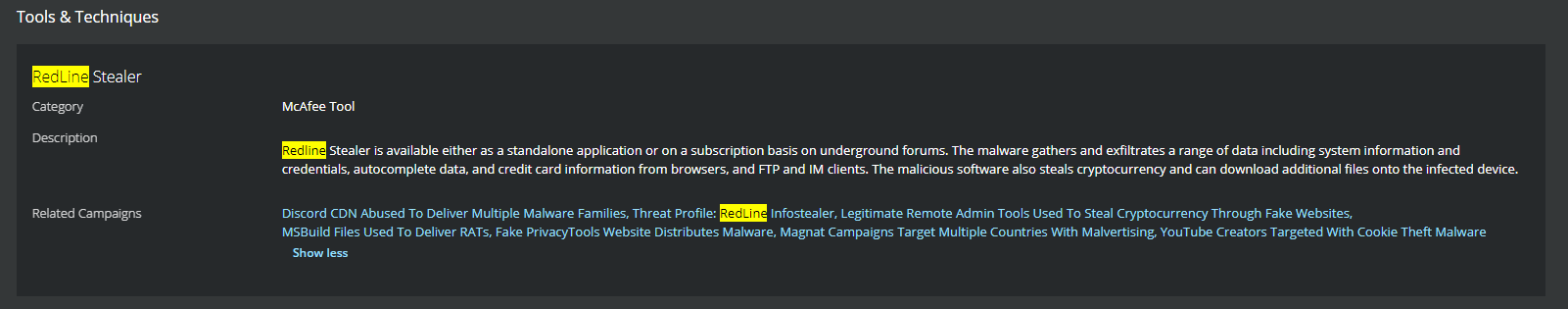
RedLine Stealer Issues 100,000 Samples - What is Happening? –
RedLine Stealer Malware - Password Stealer Virus
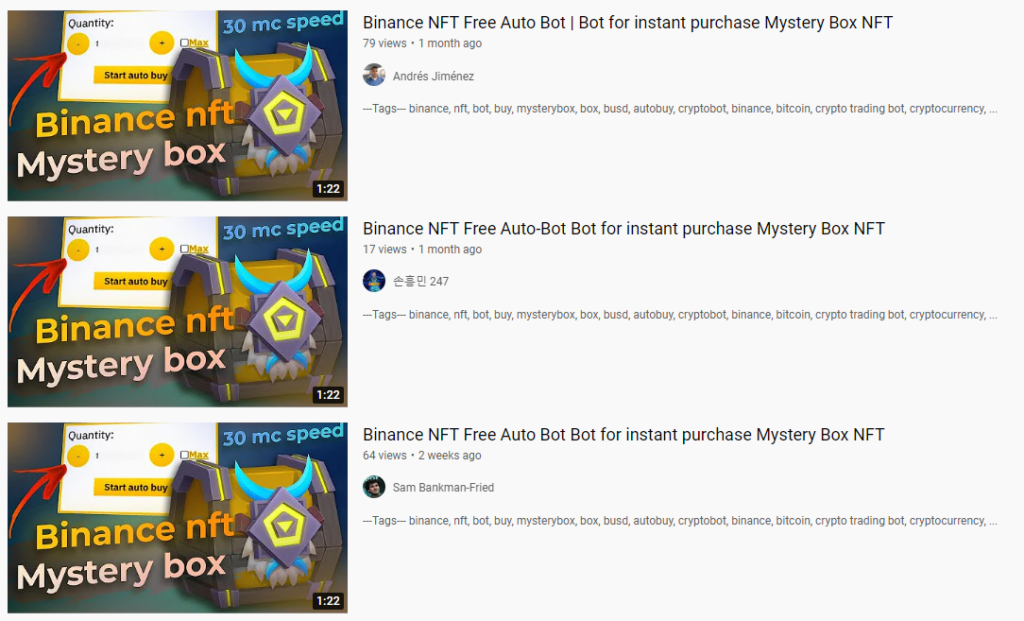
RedLine Stealer Campaign Using Binance Mystery Box Videos to Spread GitHub-Hosted Payload - Netskope

Michael H. on LinkedIn: Do Not Cross The 'RedLine' Stealer: Detections and Analysis

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

eSentire eSentire Threat Intelligence Malware Analysis: Redline…

Advice For Catching a RedLine Stealer, by John F, Oct, 2023

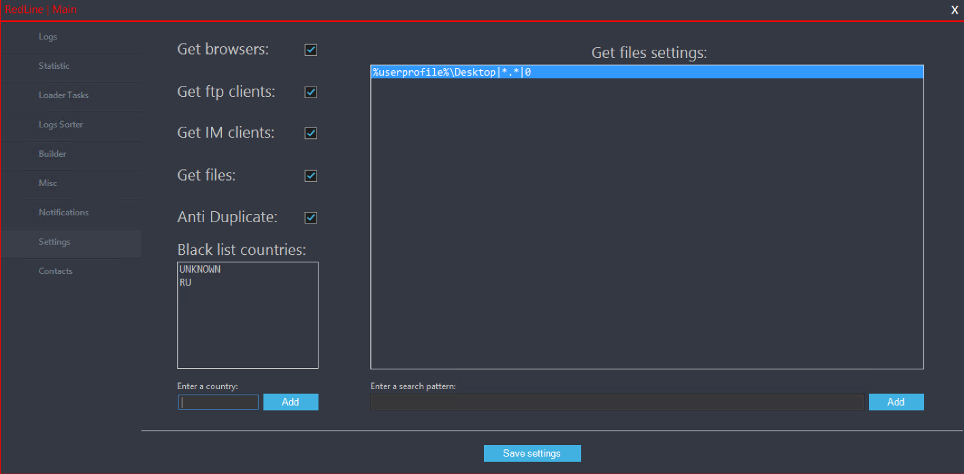
A Detailed Analysis of the RedLine Stealer

To Fill or AutoFill, Your Passwords are just a RedLine away from being stolen

eSentire eSentire Threat Intelligence Malware Analysis: Redline…

Do Not Cross The 'RedLine' Stealer: Detections and Analysis

RedLine Stealer malware responsible for stealing majority of the credentials

A thief in red: Compliance and the RedLine information stealer
de
por adulto (o preço varia de acordo com o tamanho do grupo)