The Hidden Threat to Your SecOps: Tampered Log Data
Por um escritor misterioso
Descrição
Log data plays a critical role in SecOps by providing insights into systems. This makes log data a popular target for cybercriminals.
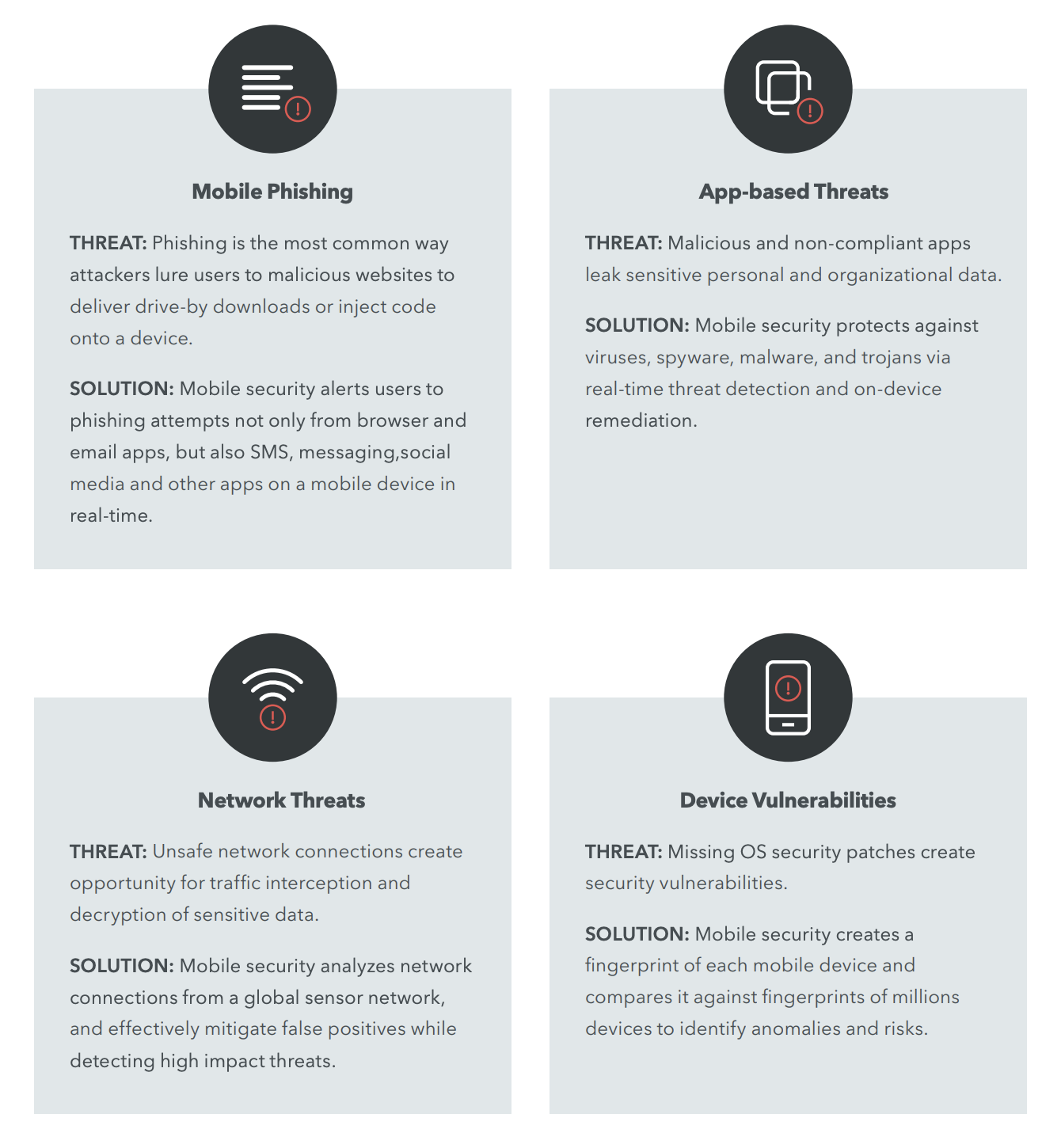
How VMware can Secure Mobile Endpoints with Threat Defense (MTD)
.png)
Lessons that a CISO learns in 2022
What Is Cyber Threat Hunting?

The Anomali Blog
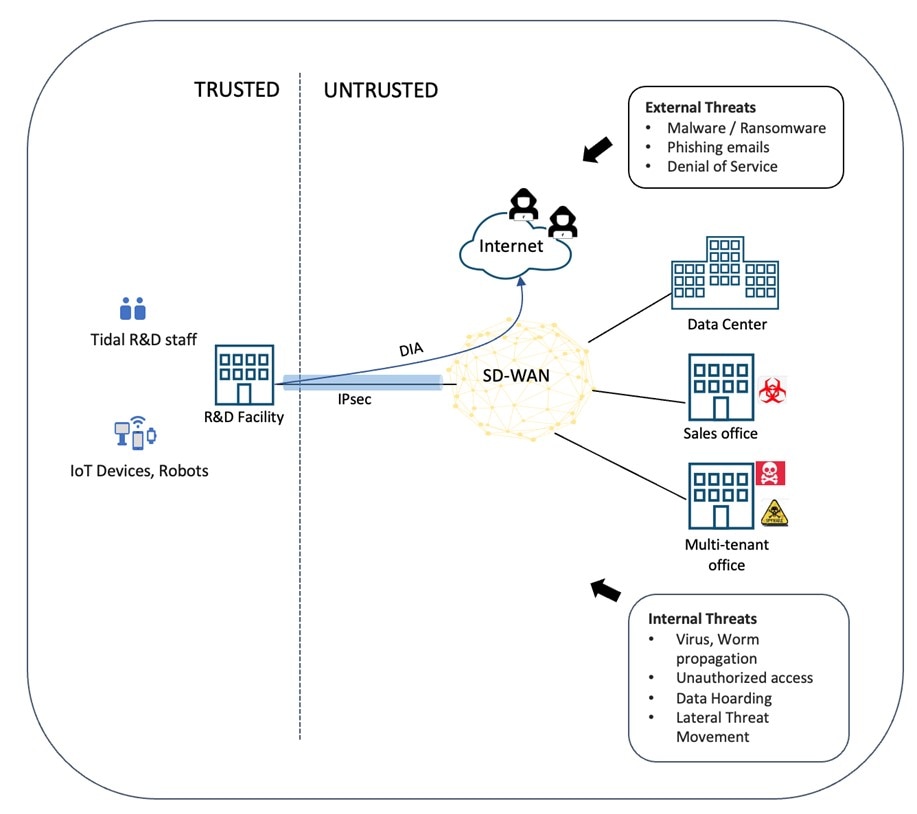
Design Zone for Branch/WAN - Cisco SD-WAN Security Sensitive Branch Design Case Study - Cisco

Detect – SEC-LABS R&D
Mastering OSINT Automation with Workflows: The Essential Guide
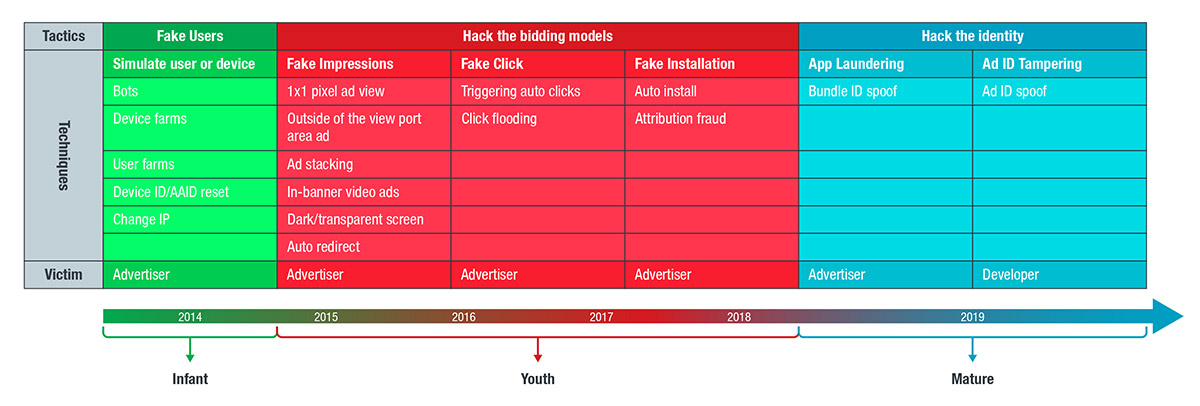
Review, Refocus, and Recalibrate: The 2019 Mobile Threat Landscape - Security Roundup

SEC-LABS R&D – Protect, Detect and Respond
How to configure Microsoft Defender for Endpoint
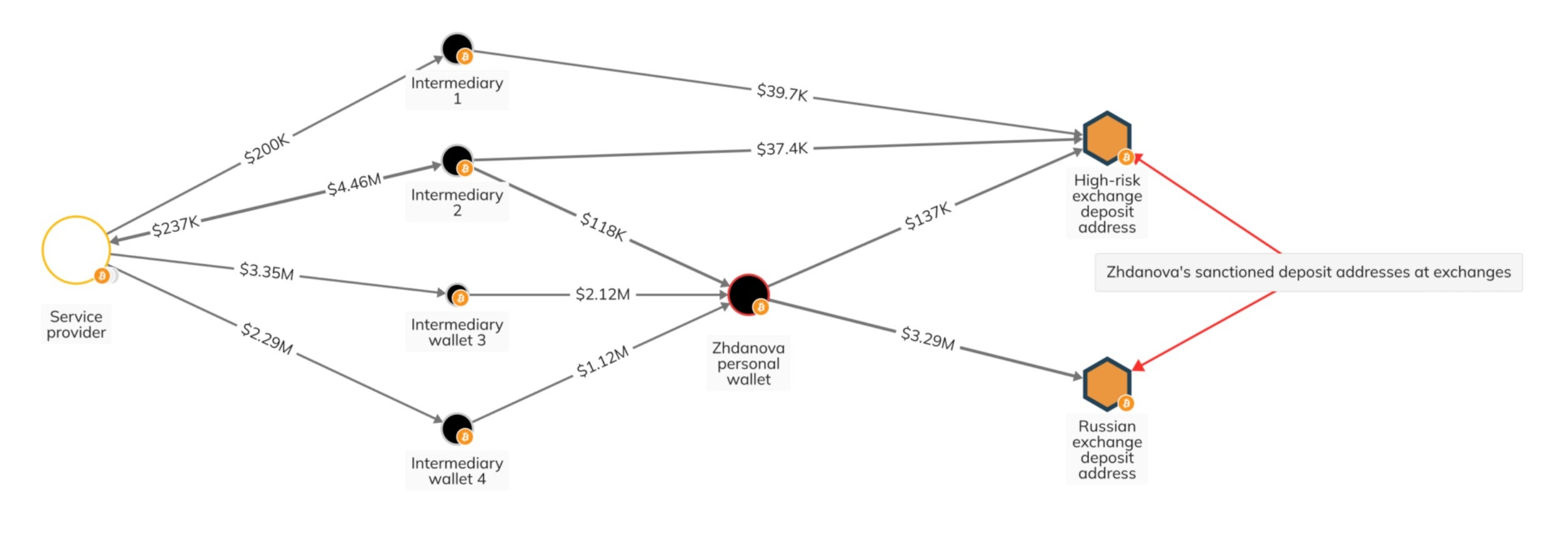
The Good, the Bad and the Ugly in Cybersecurity - Week 45 - SentinelOne

Terraform Security: Top Risks and 5 Security Best Practices
The Hidden Threat to Your SecOps: Tampered Log Data
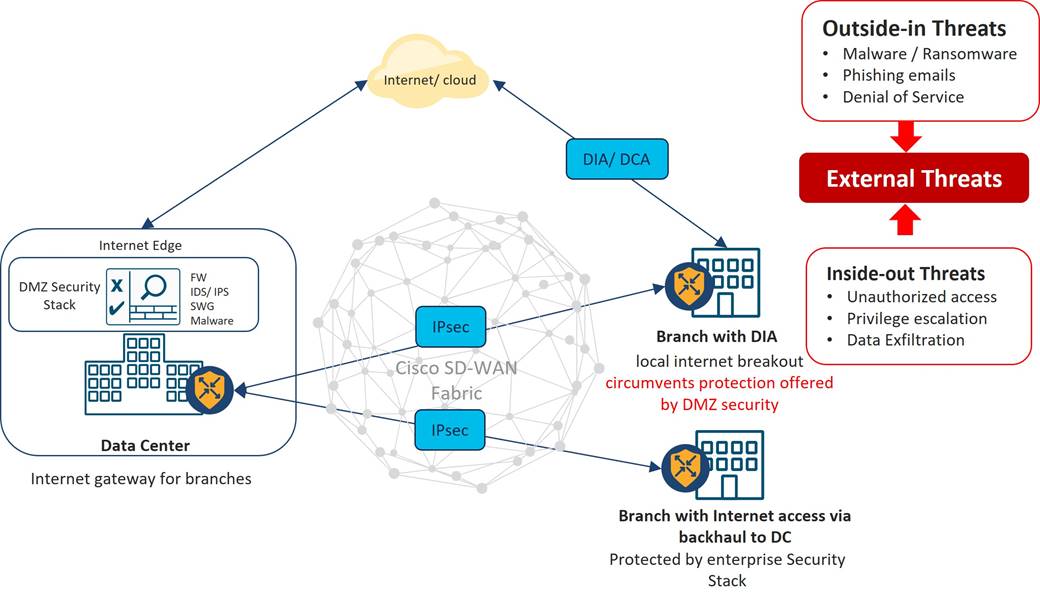
Design Zone for Branch/WAN - Cisco SD-WAN Security Sensitive Branch Design Case Study - Cisco

Cybersecurity Fundamentals - Attack Surfaces and Vulnerabilities - Orange Matter
de
por adulto (o preço varia de acordo com o tamanho do grupo)