System, error, attack, malware, failure, unauthorized, hacker icon
Por um escritor misterioso
Descrição
Download this system, error, attack, malware, failure, unauthorized, hacker icon in filled outline style. Available in PNG and SVG formats.

Cybersecurity - A Beginner's Guide - StorMagic

2023 Cyber Security Statistics: The Ultimate List Of Stats, Data

IoT security attacks: A timeline of the internet of things' darkest hours

How Hackers Get Into Your Computer (And How To Stop Them)

Firmware Attacks: What They Are & How I Can Protect Myself
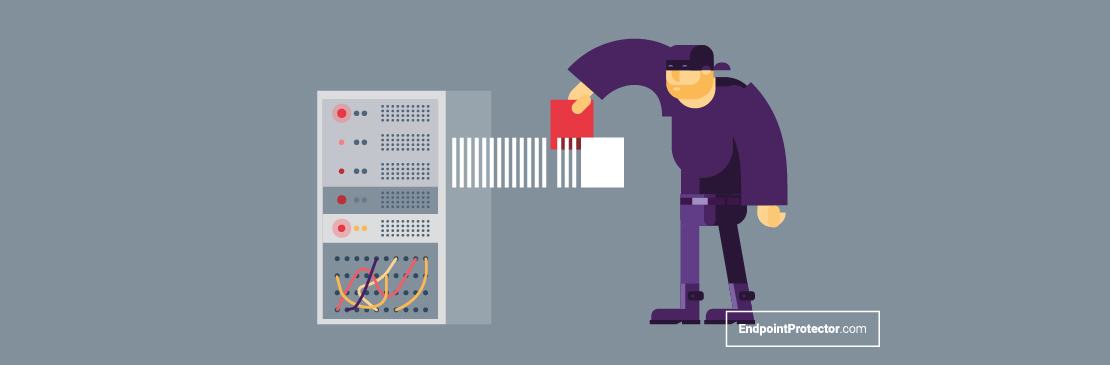
Top 5 Internal Data Security Threats and How to Deal with Them

A massive campaign delivered a proxy server application to 400,000
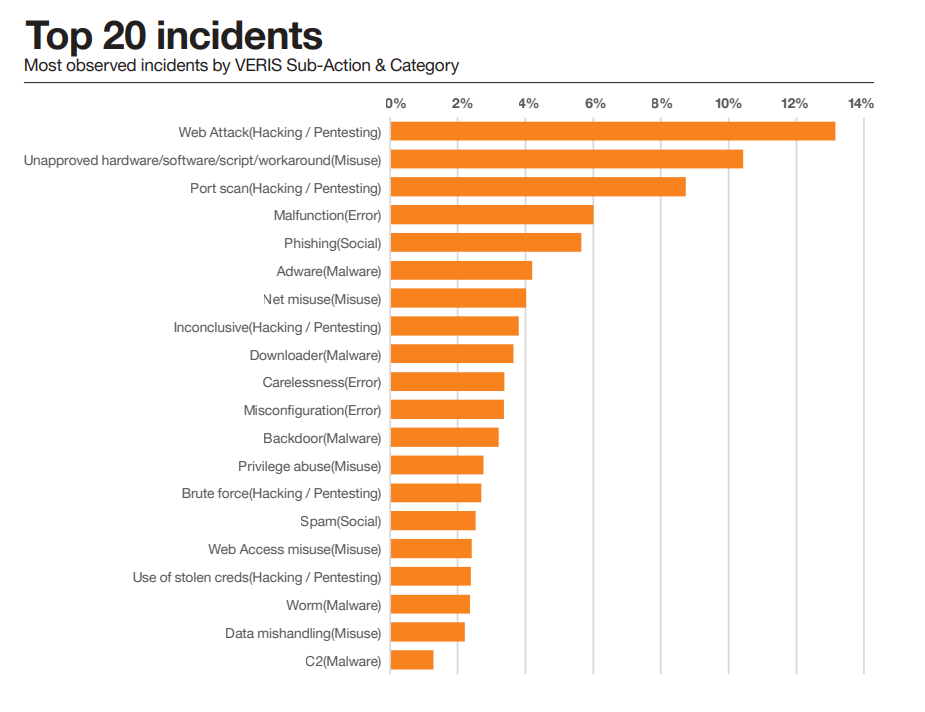
Security Misconfigurations Caused 35% of All Time Cyber Incidents

98,785 Vulnerable Images, Stock Photos, 3D objects, & Vectors

8 of the Most Common Ways Hackers Steal Passwords - Dashlane

Exploring Common Types of Security Incidents - Scrut Automation

Major Cyber Attacks in Review: November 2023 - SOCRadar
Computer, crash, error, failure, problem, screen, system icon
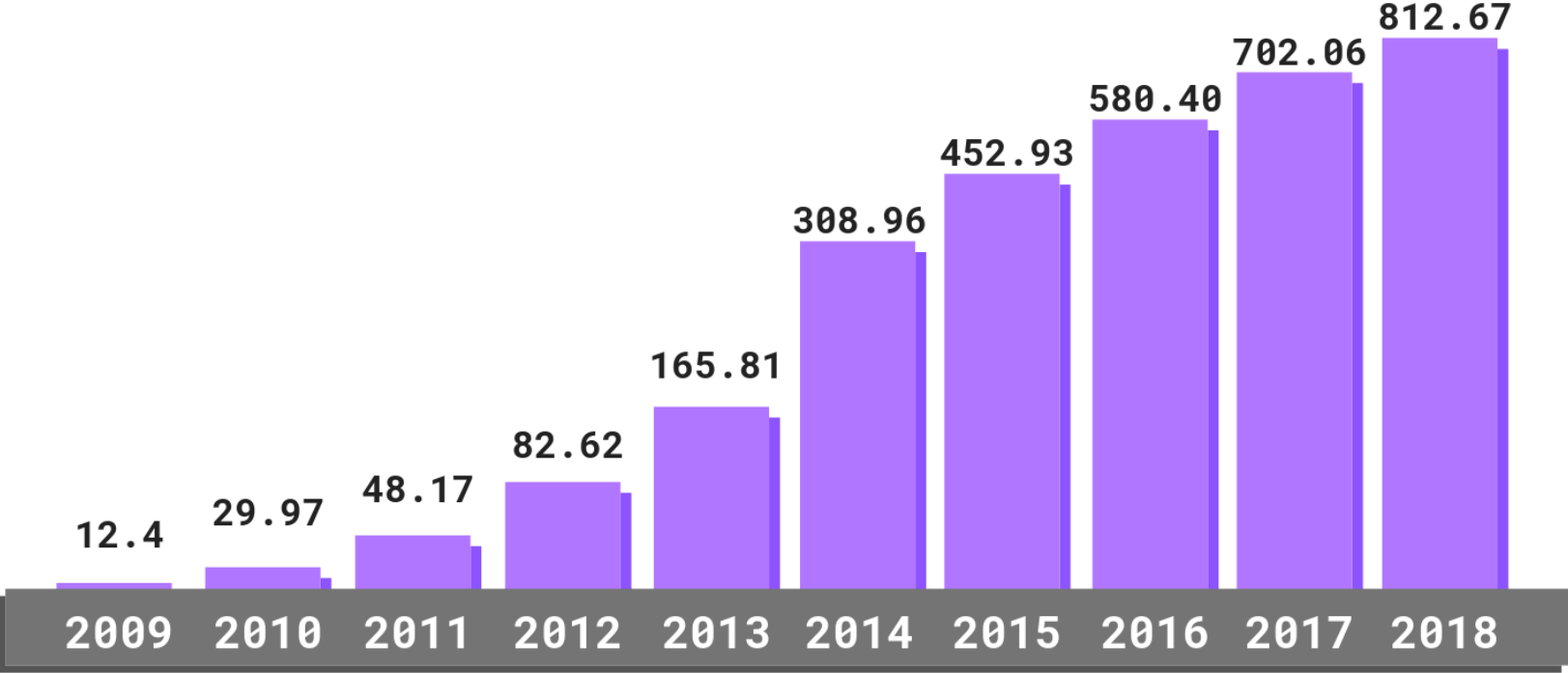
2023 Cyber Security Statistics: The Ultimate List Of Stats, Data
de
por adulto (o preço varia de acordo com o tamanho do grupo)


.png)



