Pawn Storm Abuses OAuth In Social Engineering Attacks
Por um escritor misterioso
Descrição
This blog post discusses how Pawn Storm abused Open Authentication (OAuth) in advanced social engineering schemes. High profile users of free webmail were targeted by campaigns between 2015 and 2016.

Google warns of APT28 attack attempts against 14,000 Gmail users

Protecting Yourself from Social Engineering Attacks: Understanding the Tactics Used by Threat Actors
Pawn Storm's Lack of Sophistication as a Strategy

The 13 Most Common Types of Social Engineering Attacks + How to Defend Against Them
Pawn Storm's Lack of Sophistication as a Strategy

How to Protect Against Social Engineering Attacks?
Social Engineering Attacks - Manipulating Your Thoughts To Fall In Trap
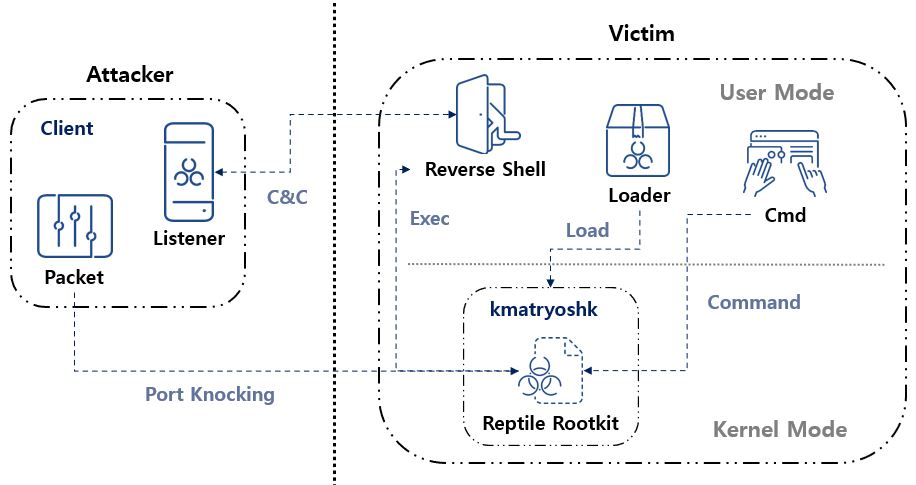
rootkit Archives - Security Affairs

What is a Social Engineering Attack?

Hackers Abusing OAuth Token to Take Over Millions of Accounts
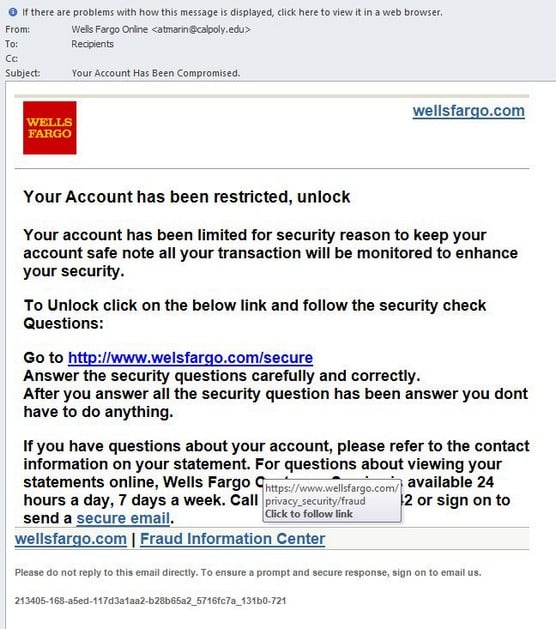
Types of Social Engineering Attacks - dummies

Mandiant identifies 3 hacktivist groups working in support of Russia

Social Engineering Attacks: Definition, Examples, Prevention
de
por adulto (o preço varia de acordo com o tamanho do grupo)







