SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Descrição
As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

SILKLOADER という検出回避に優れたマルウェア:中国/ロシアの犯罪エコシステムが連携? – IoT OT Security News

Hackers start using double DLL sideloading to evade detection

Lynx-CERT

Evading AV Software « Null Byte :: WonderHowTo
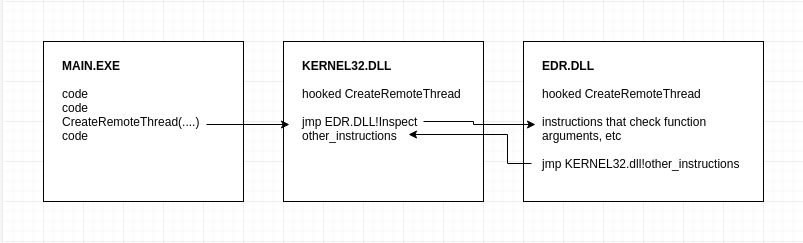
AV/EDR Evasion, Malware Development P-3
Telerik Government breach, Critical Outlook bug, LockBit threatens SpaceX
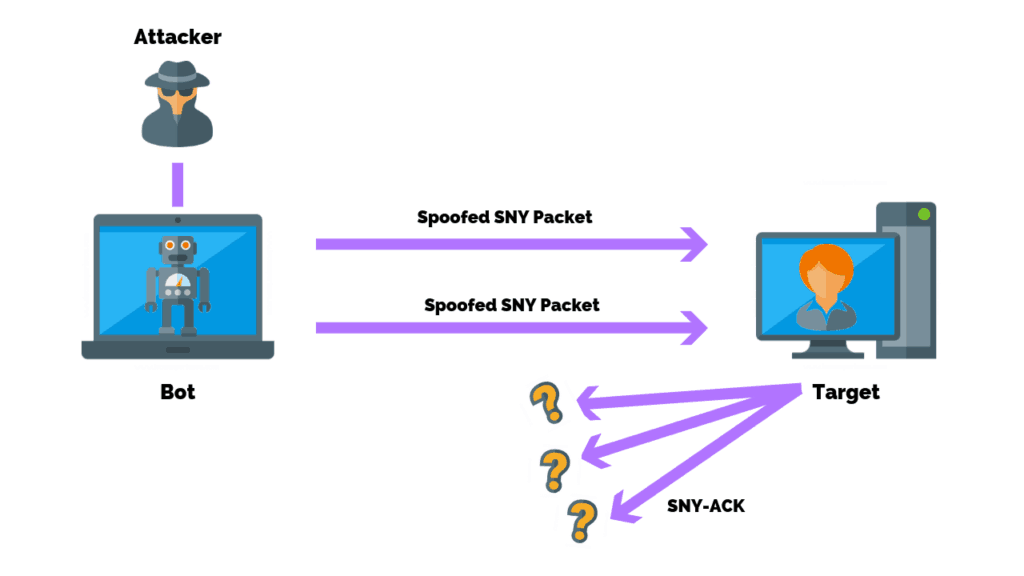
How To Prevent Network Attacks

Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

SILKLOADER: How Hackers Evade Detection
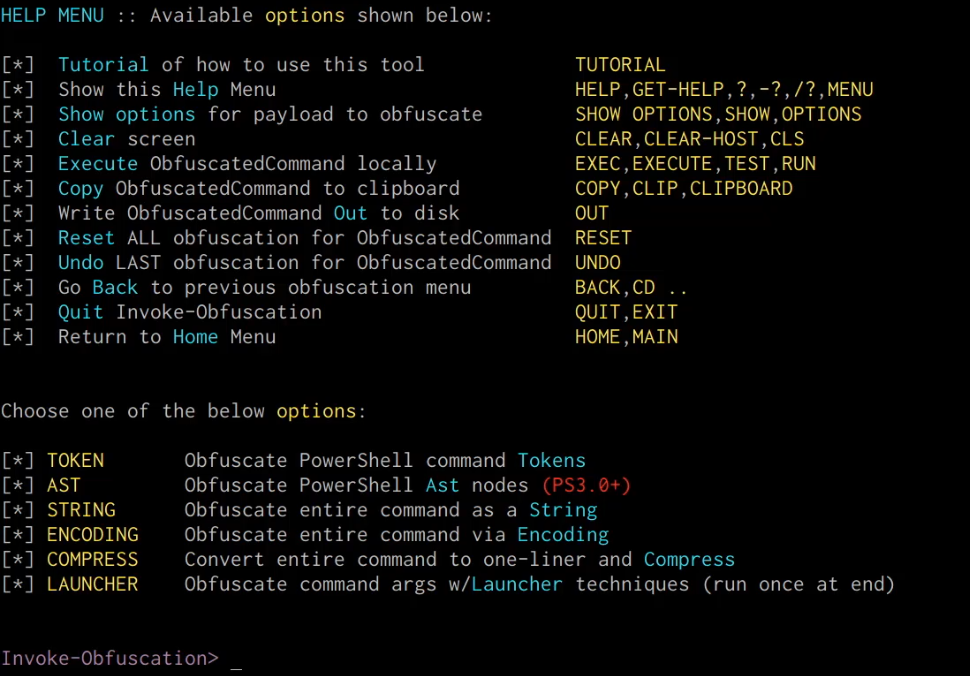
Windows Red Team Defense Evasion Techniques - HackerSploit Blog

1-15 March 2023 Cyber Attacks Timeline – HACKMAGEDDON

Lynx-CERT

Endpoint Protection - Symantec Enterprise

Hackers start using double DLL sideloading to evade detection
de
por adulto (o preço varia de acordo com o tamanho do grupo)