Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download
Por um escritor misterioso
Descrição
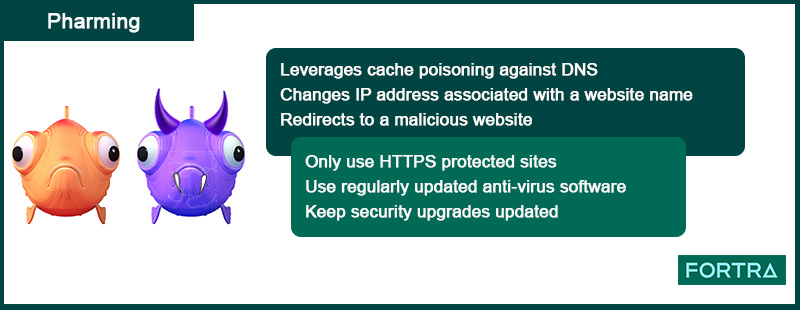
Phishing utilizing social engineering Induces the recipient to reveal desired personal information Bank account SSN Address Etc. Sometimes entices the recipient to go to a malicious web site
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
6 Common Phishing Attacks and How to Protect Against Them

DNS Advanced Attacks and Analysis
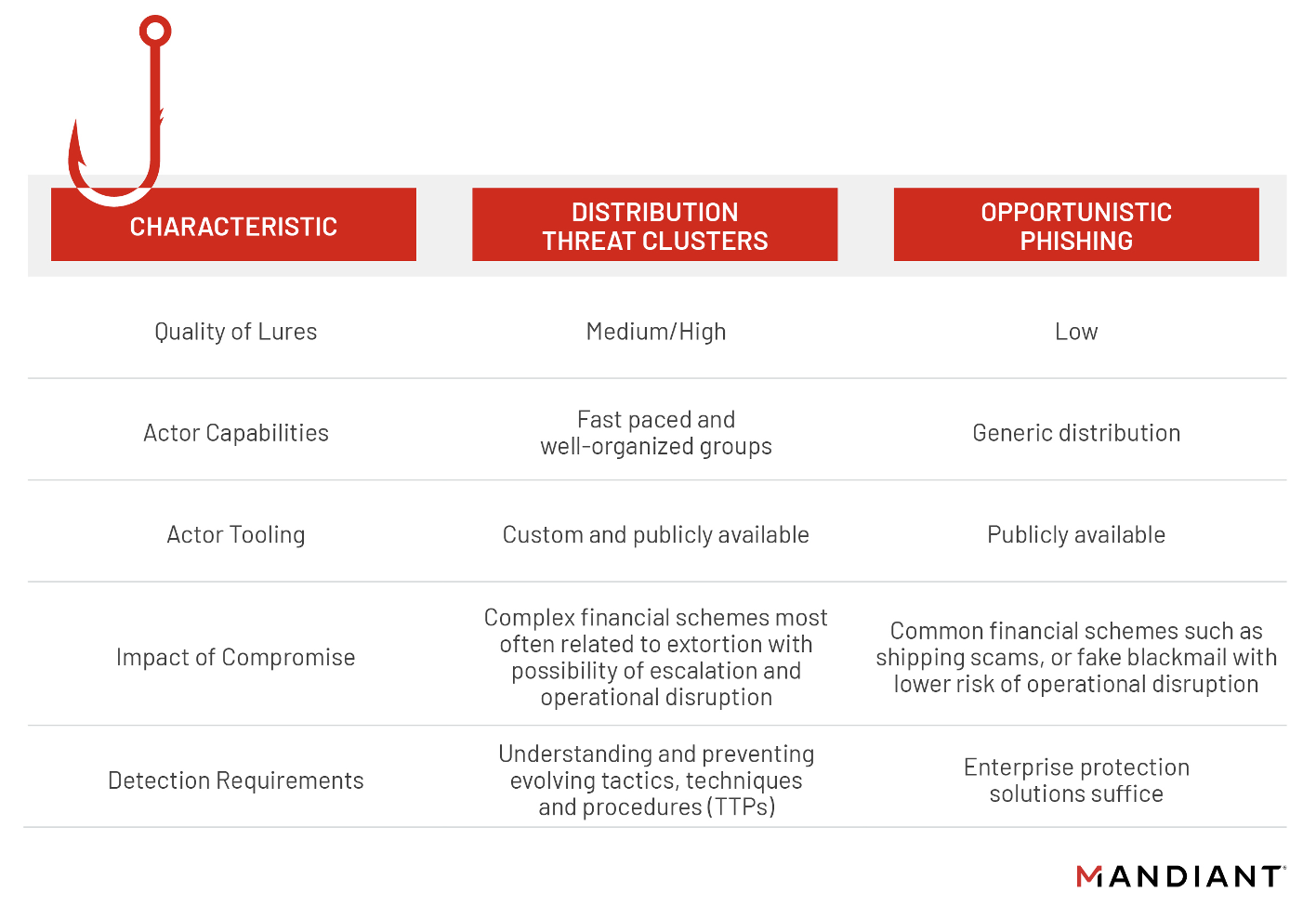
Gone Phishing: Hunting for Malicious Industrial-Themed Emails to

Web Filtering Blog
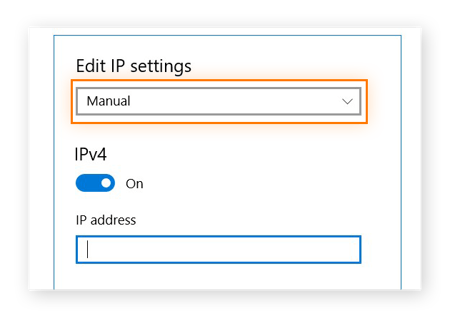
Static vs. Dynamic IP Addresses: What's the Difference?
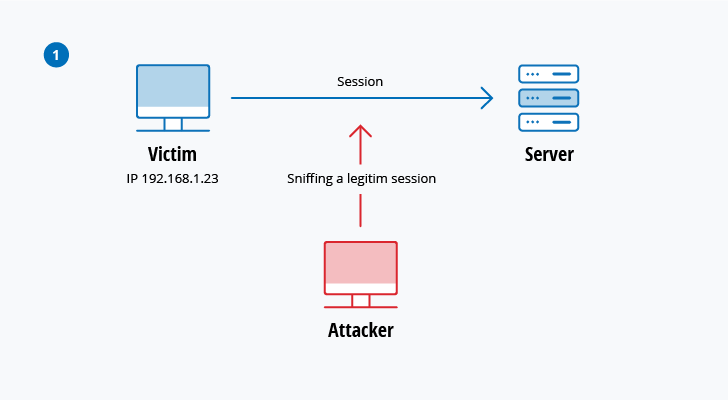
The 12 Most Common Types of Cybersecurity Attacks Today
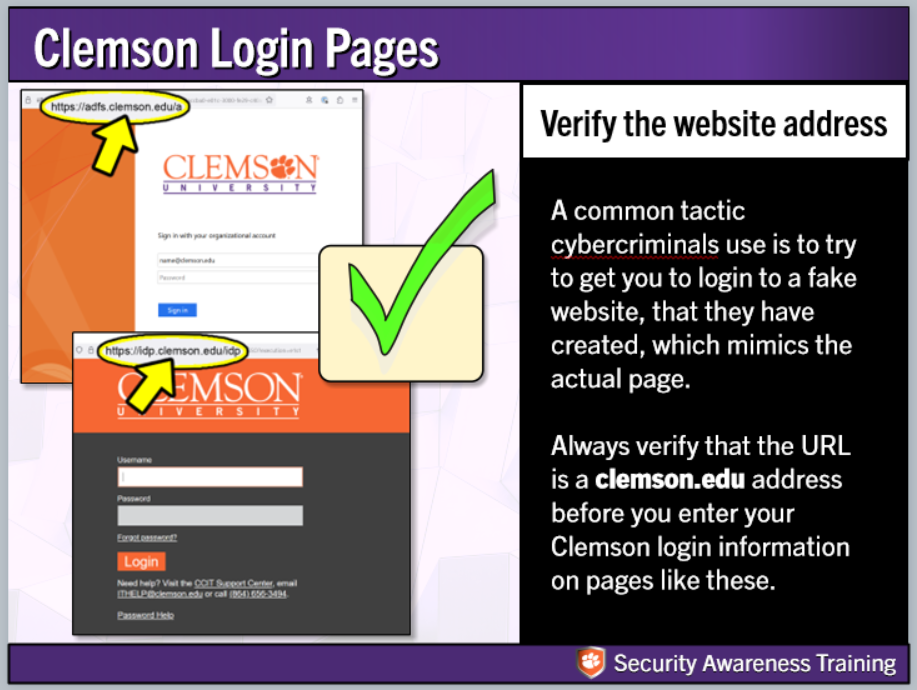
Cybersecurity Alerts

Electronics, Free Full-Text

6 Common Phishing Attacks and How to Protect Against Them

Phishing URL Detection with ML. Phishing is a form of fraud in
de
por adulto (o preço varia de acordo com o tamanho do grupo)