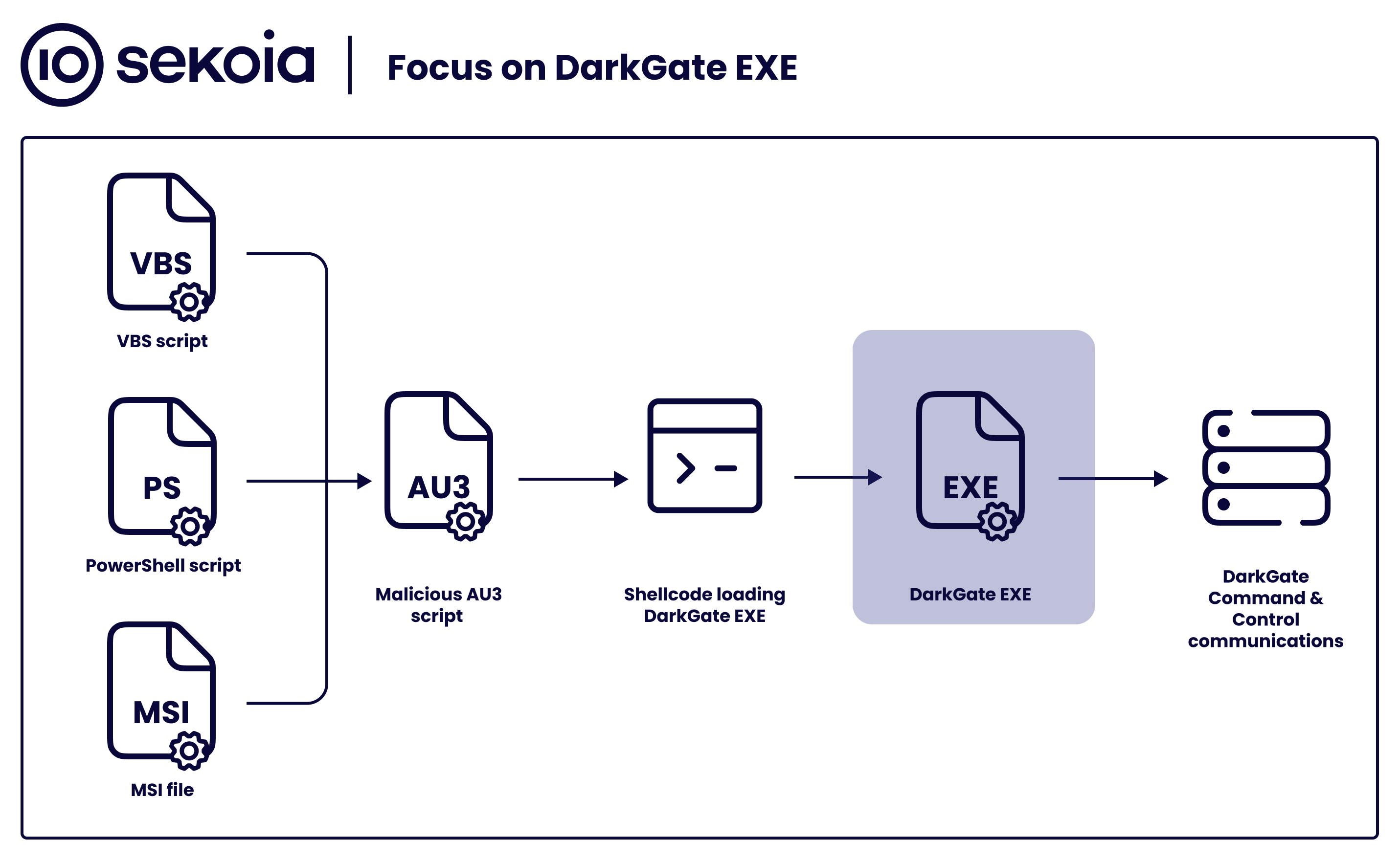
Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Descrição
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation
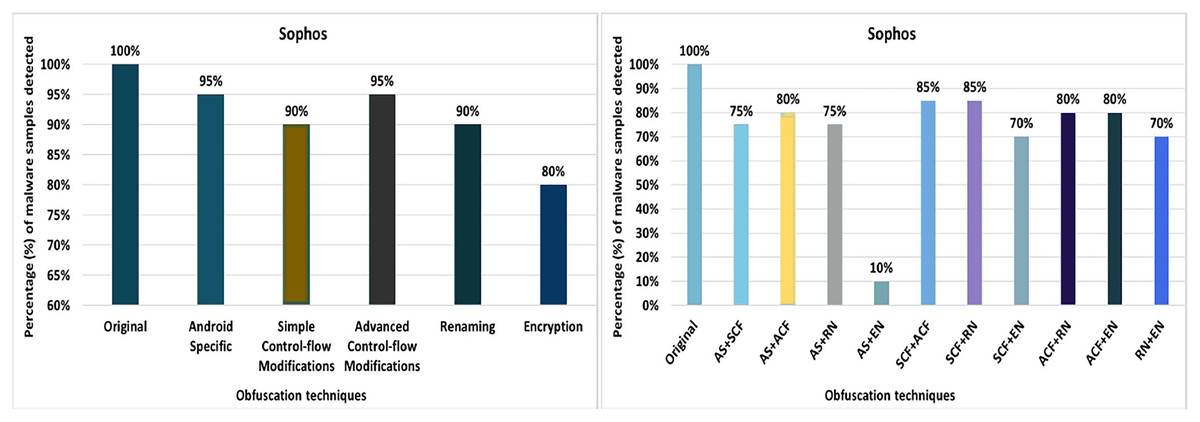
On the evaluation of android malware detectors against code
A Deep Dive into 70 Layers of Obfuscated Info-Stealer Malware

PDF] Obfuscapk: An open-source black-box obfuscation tool for

CB16] Invoke-Obfuscation: PowerShell obFUsk8tion Techniques & How
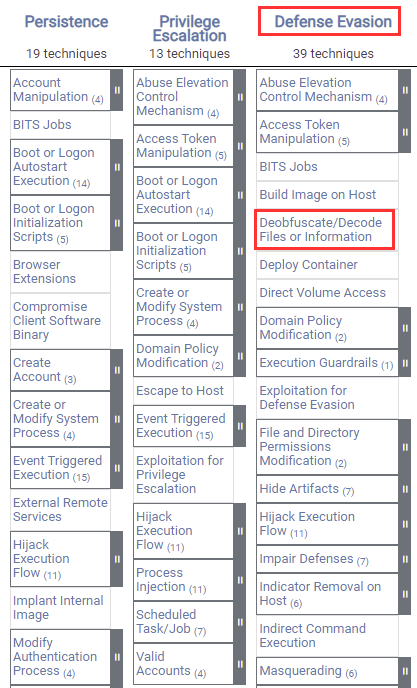
Windows Red Team Defense Evasion Techniques

Balada Injector still at large – new domains discovered

macOS Payloads 7 Prevalent and Emerging Obfuscation Techniques

How hackers are using Google ads network to steal users' data

How Hackers Use Binary Padding to Outsmart Sandboxes

PDF) A Malware Obfuscation AI Technique to Evade Antivirus

Several Android Malware Apps Use Secret APK Compression to Avoid

Flax Typhoon Hackers Employ Advanced Tactics, Leveraging LOLBins

How Can We Turn a Hacker's Toolkit Against Them? The Evolution of

BGP Hijacking: How Hackers Circumvent Internet Routing Security

Evading Detection: A Beginner's Guide to Obfuscation - 2022
de
por adulto (o preço varia de acordo com o tamanho do grupo)