Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

Windows Servers Security: How to Look for Suspicious Activities

Malware Analysis Use Cases with ANY.RUN Sandbox - Security
Malware Analysis - What is, Benefits & Types (Easily Explained)
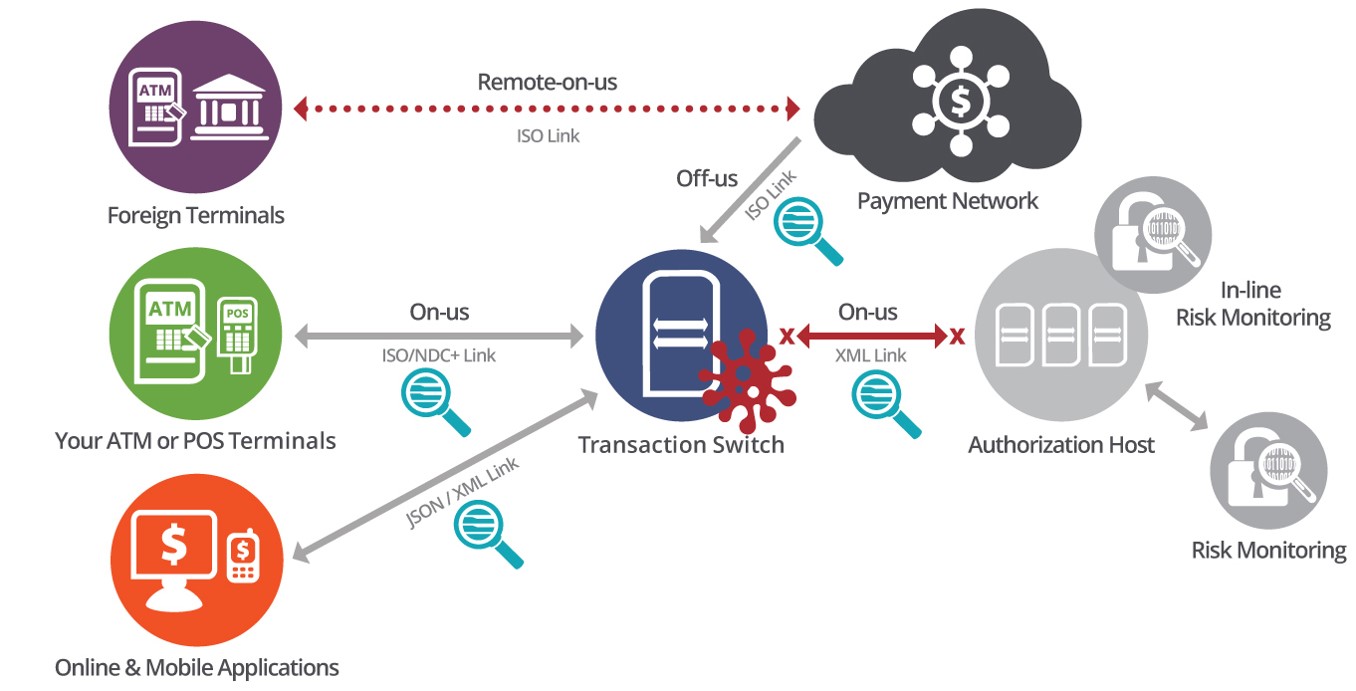
Malware Detection: One transaction at a time, INETCO Blog

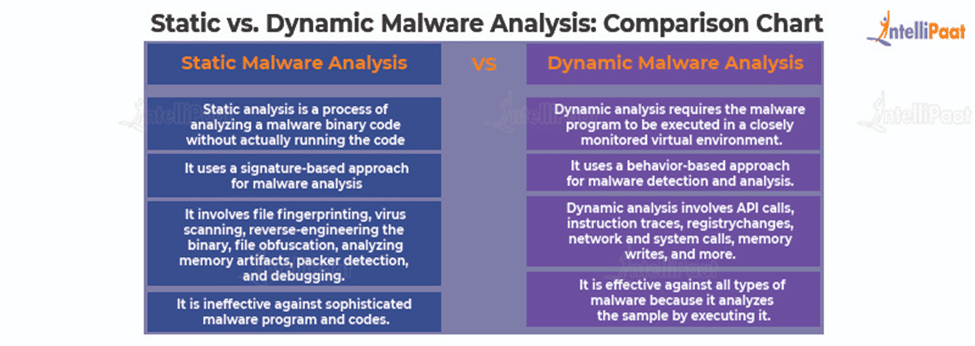
Malware Analysis: Static vs. Dynamic and 4 Critical Best Practices

How to Detect New Threats via Suspicious Activities

US Cyber Command, DHS-CISA release Russian malware samples tied to
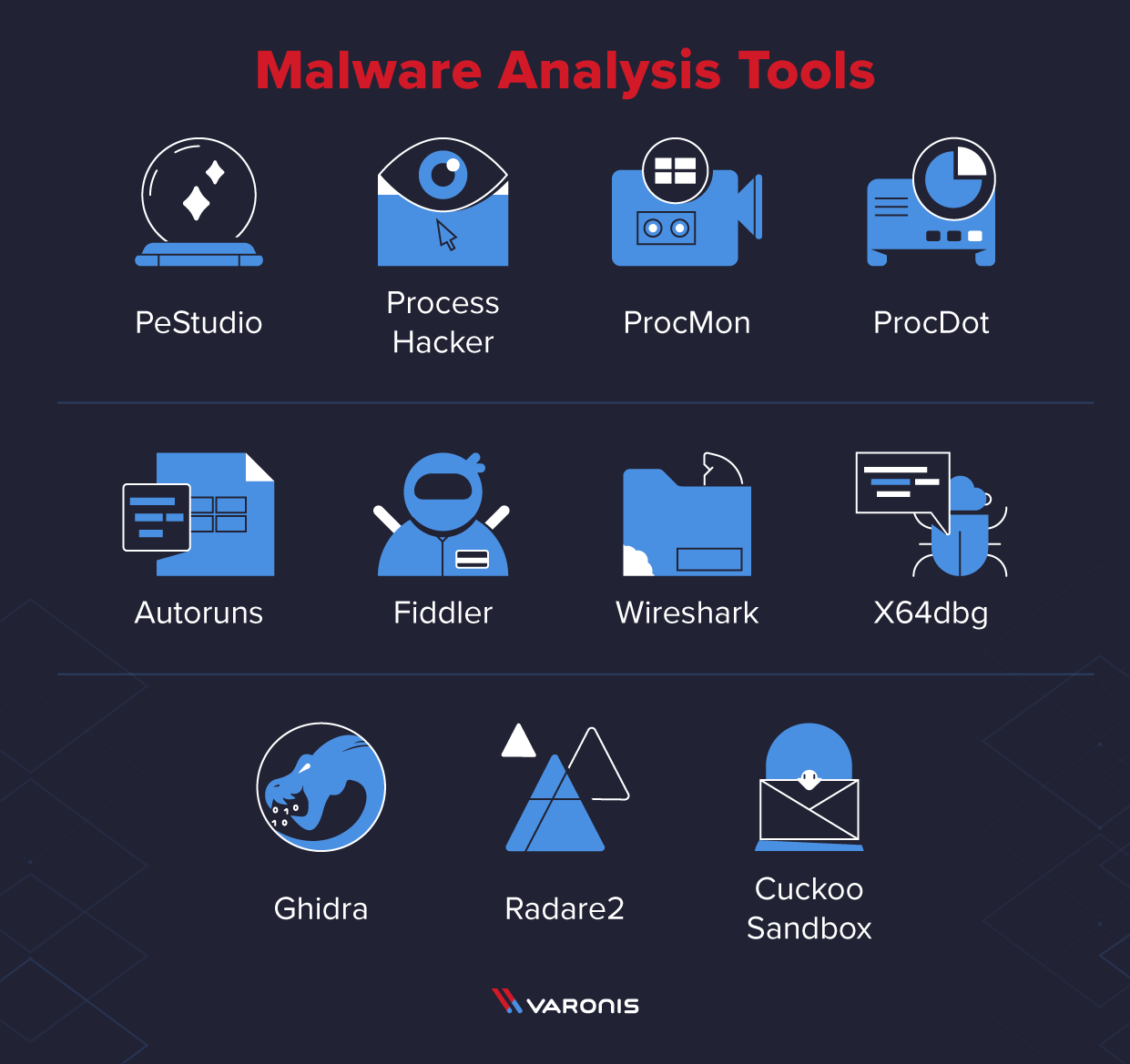
11 Best Malware Analysis Tools and Their Features

Intro to Malware Analysis: What It Is & How It Works - InfoSec
Top static malware analysis techniques for beginners

The Top 20 Malware Analysis Tools for 2024
How to Get Free Malware Samples and Reports - 's

Malware Analysis and Reverse Engineering, by Ensar Seker
Malware analysis cable.exe Suspicious activity
de
por adulto (o preço varia de acordo com o tamanho do grupo)