Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

7 Benefits Of Dynamic Malware Analysis
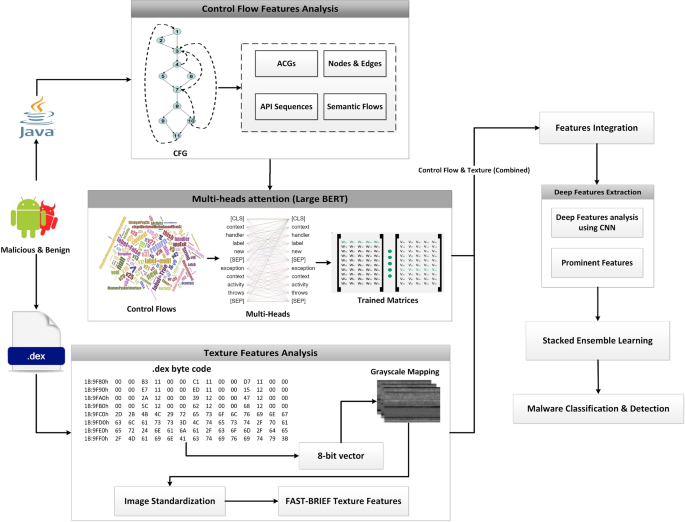
A malware detection system using a hybrid approach of multi-heads
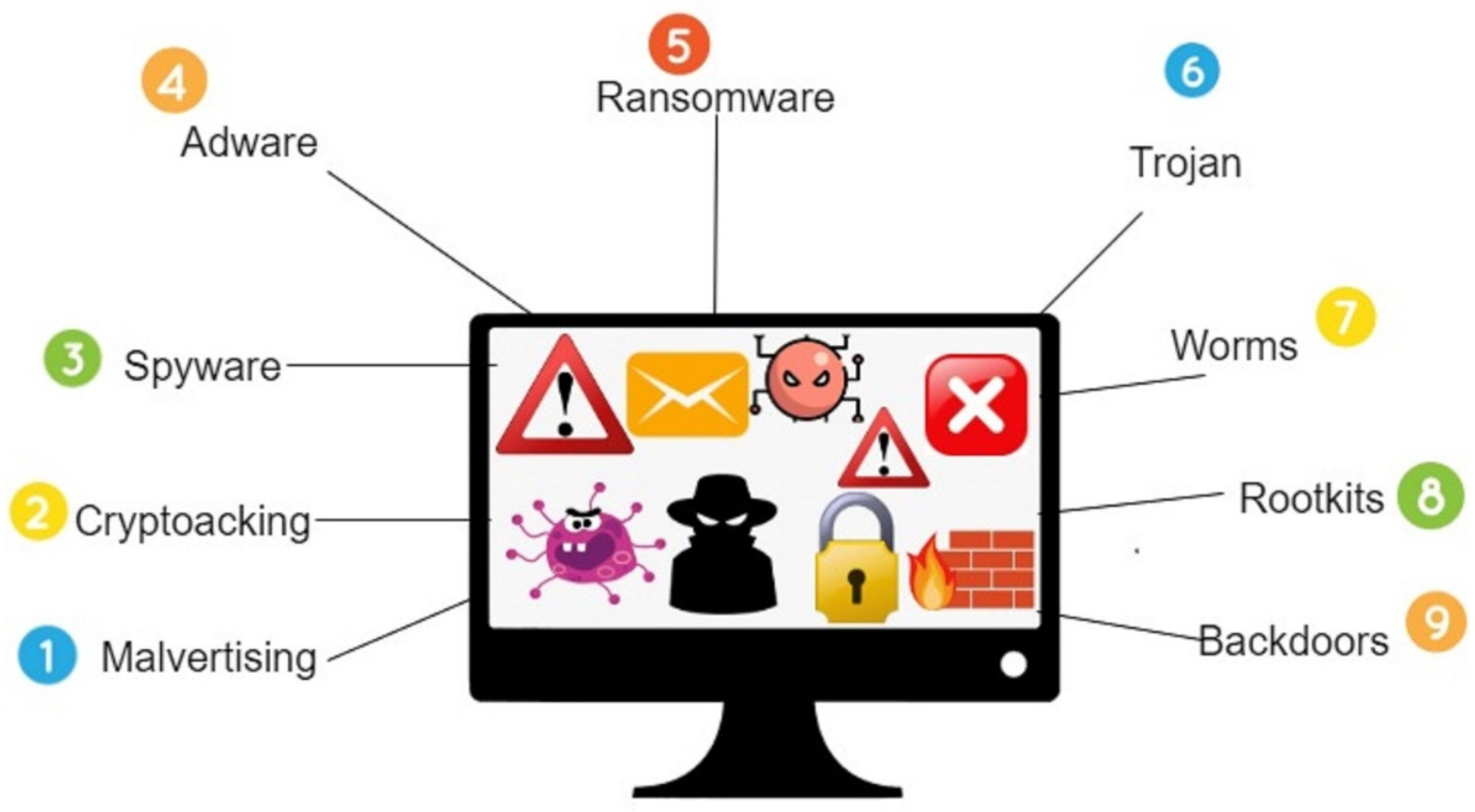
Symmetry, Free Full-Text
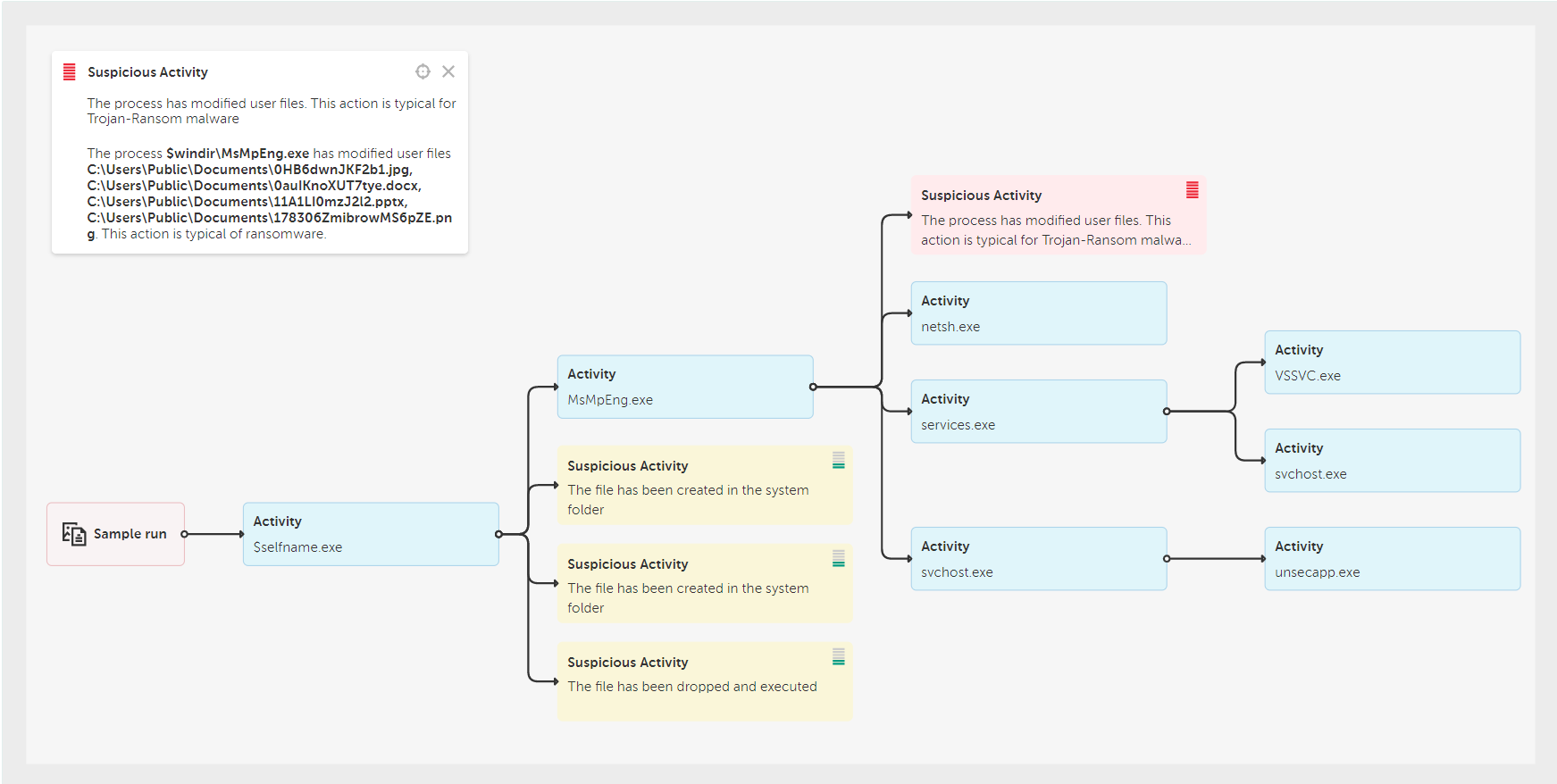
REvil ransomware attack against MSPs and its clients around the

Security Orchestration Use Case: Automating Malware Analysis
What is Malware Analysis? - SOC Prime
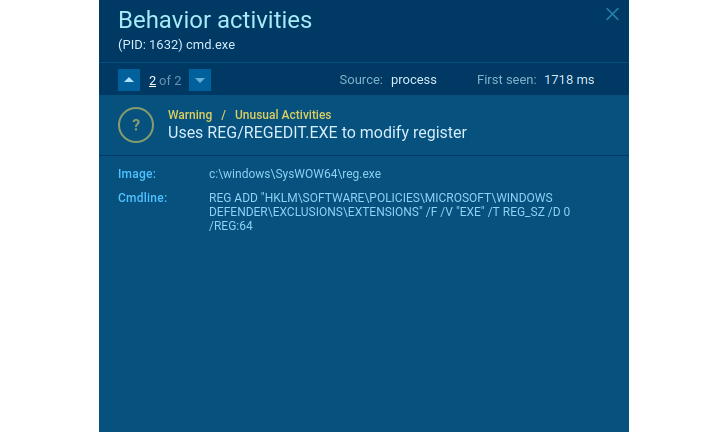
How to Detect New Threats via Suspicious Activities

Malware Detection & Top Techniques Today
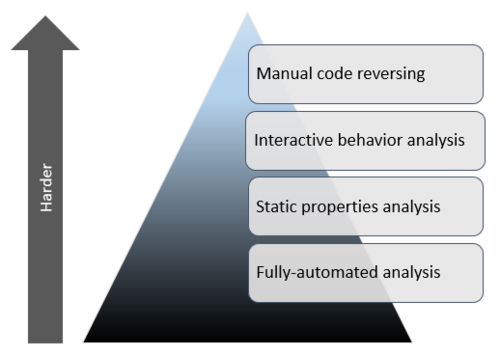
Mastering 4 Stages of Malware Analysis
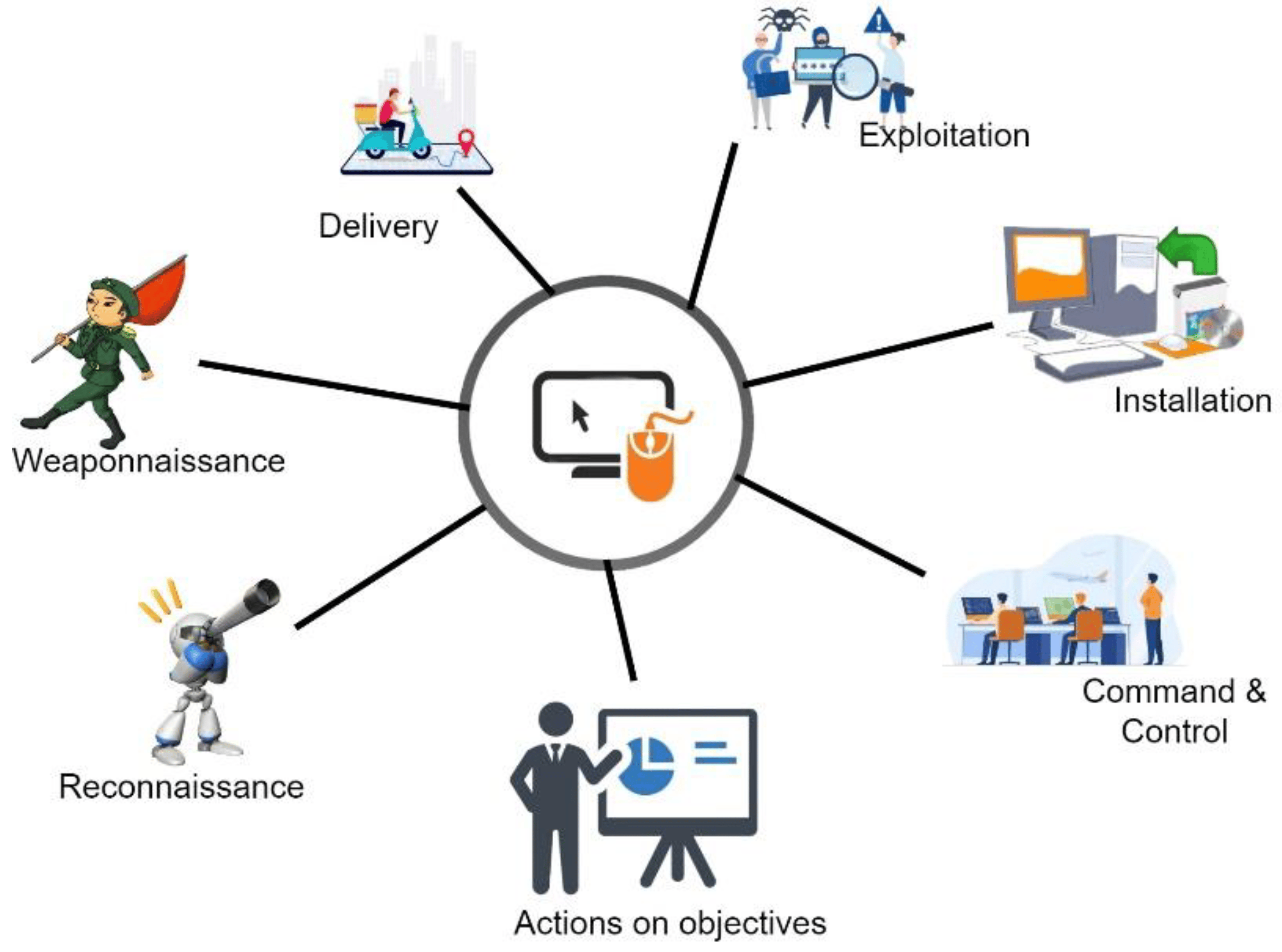
Symmetry, Free Full-Text
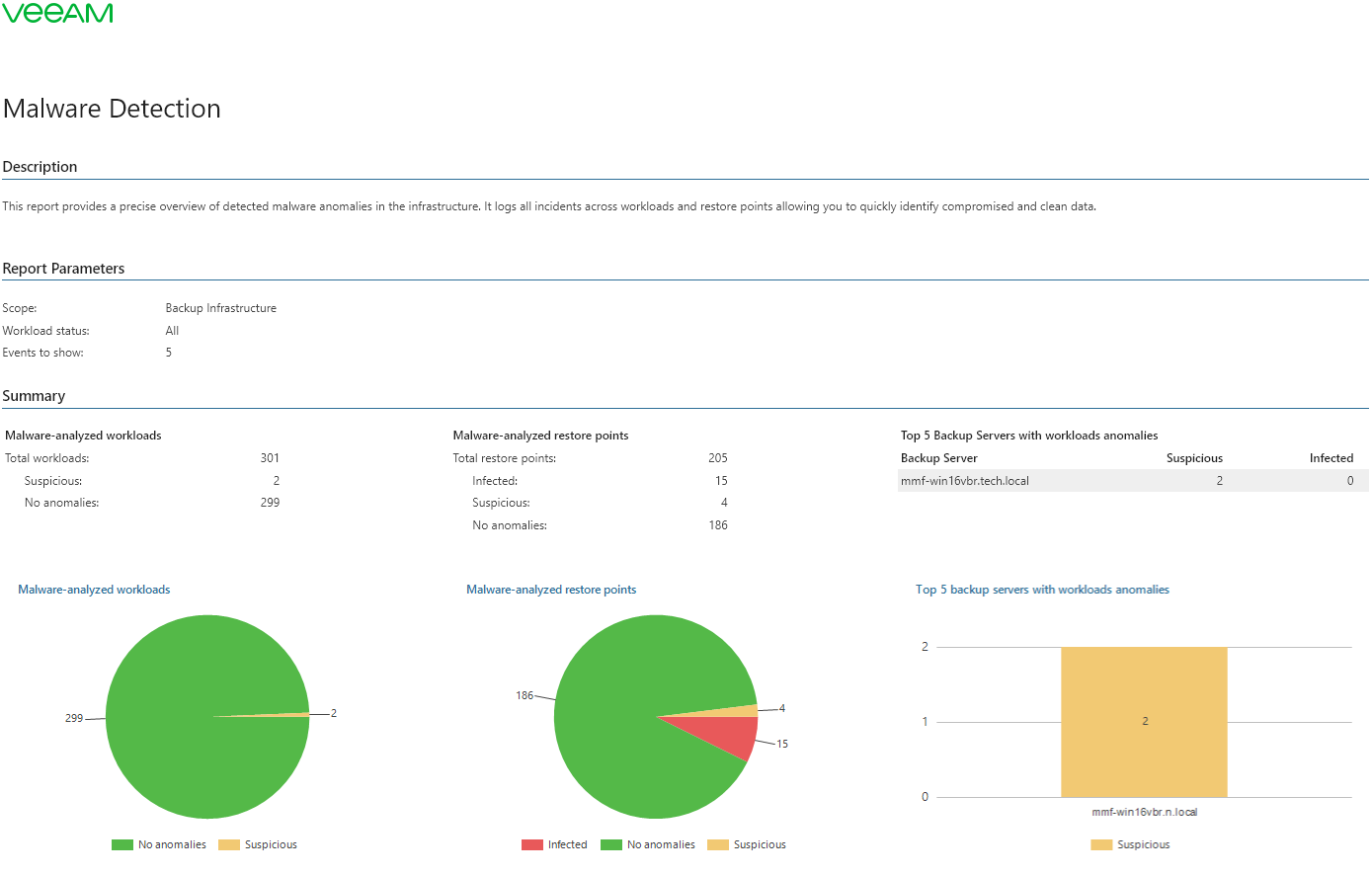
Malware Detection - Veeam ONE Reporting Guide

Ransomware: How it Works & How to Remove It
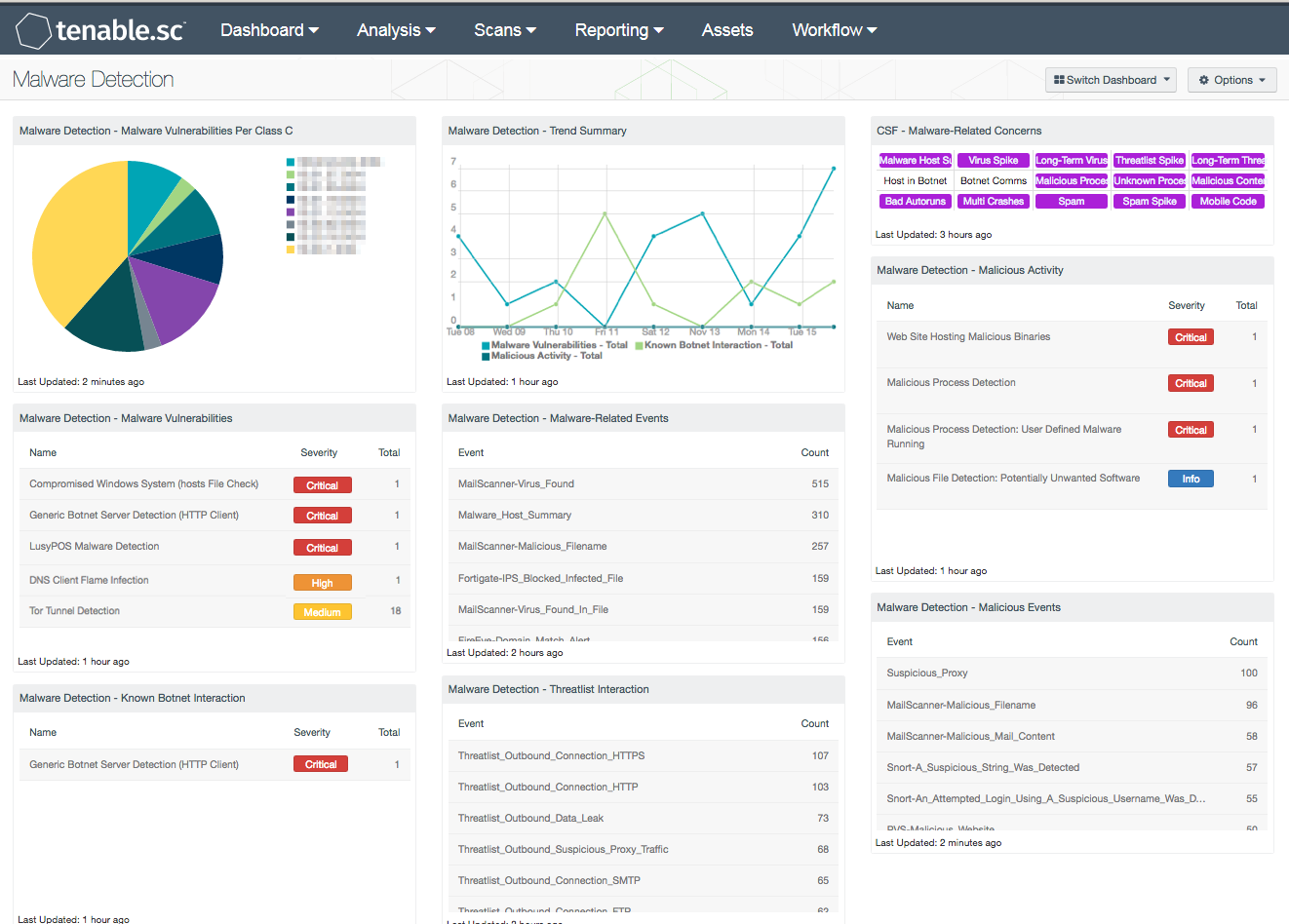
Malware Detection - SC Dashboard
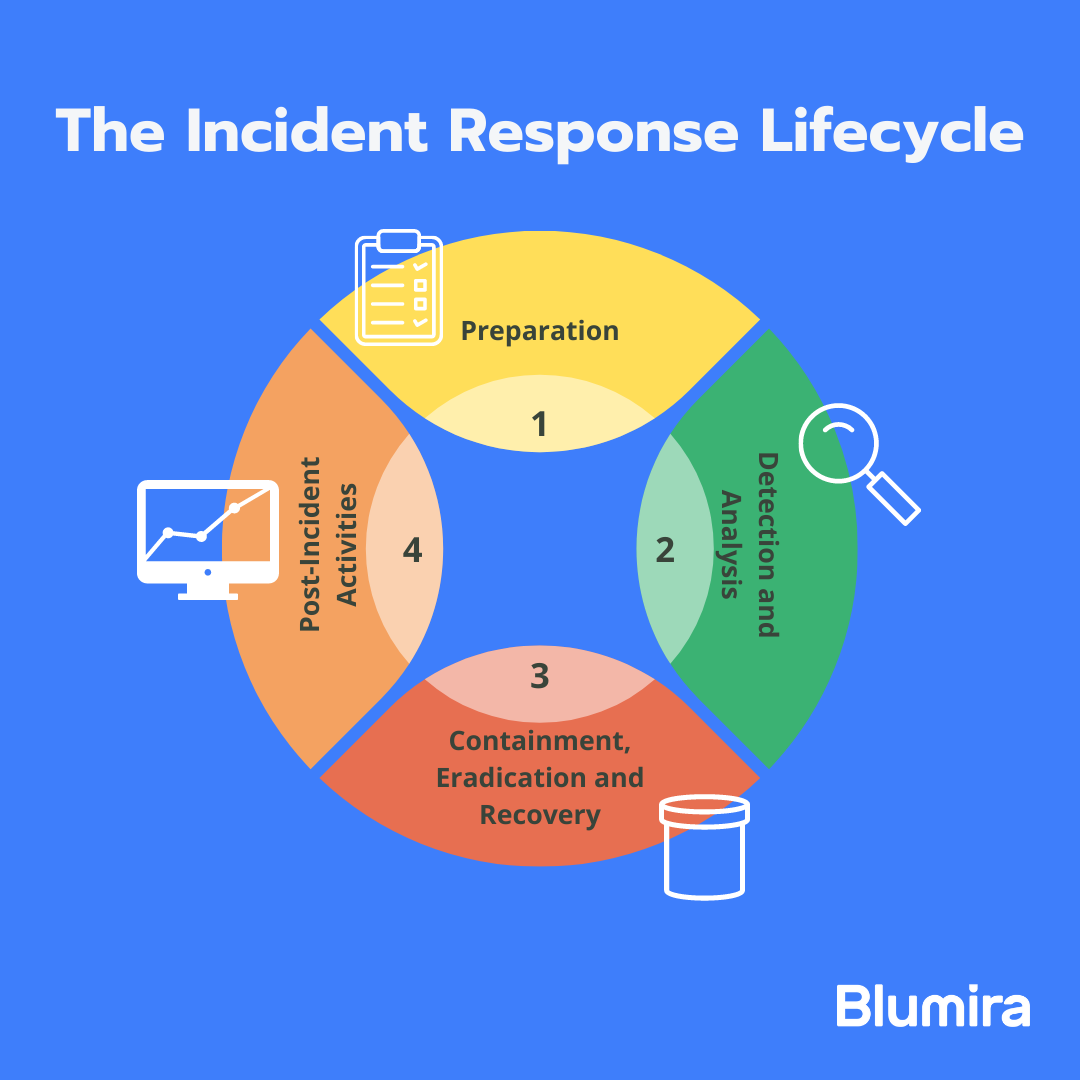
Building Effective Incident Response Procedures
de
por adulto (o preço varia de acordo com o tamanho do grupo)