Malware analysis Malicious activity
Por um escritor misterioso
Descrição

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Top 10 Types of Information Security Threats for IT Teams

TryHackMe Cyber Security Exercises and Labs
Malware analysis Malicious activity

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs
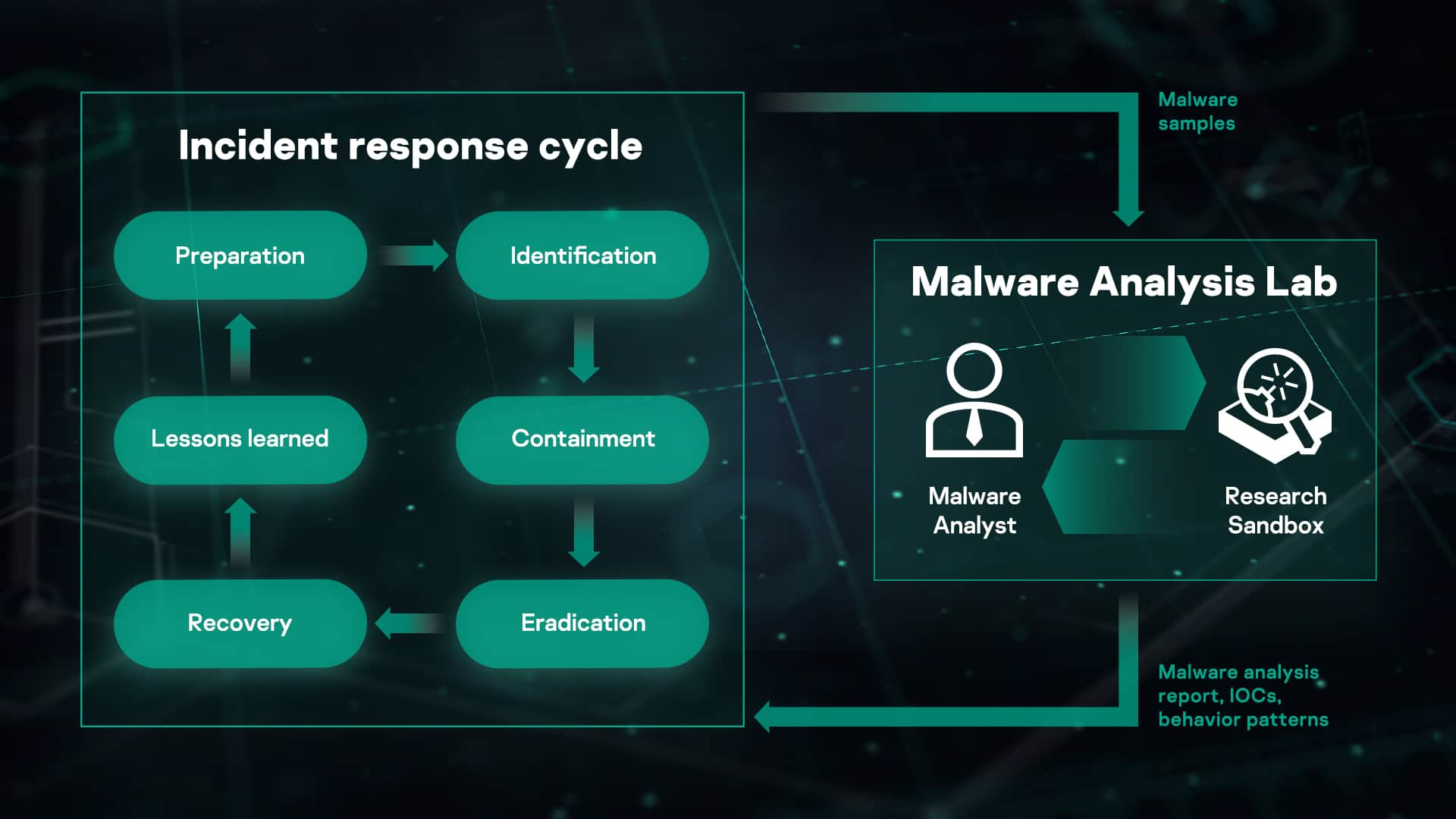
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Unveiling activities of Tropic Trooper 2023 deep analysis of Xiangoop Loader and EntryShell payload

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac
Malicious URL Scanner, Scan URLs for Malware

Malware leveraging public infrastructure like GitHub on the rise - Security Boulevard
de
por adulto (o preço varia de acordo com o tamanho do grupo)







