Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Malware analysis mykey_.rar Malicious activity

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber
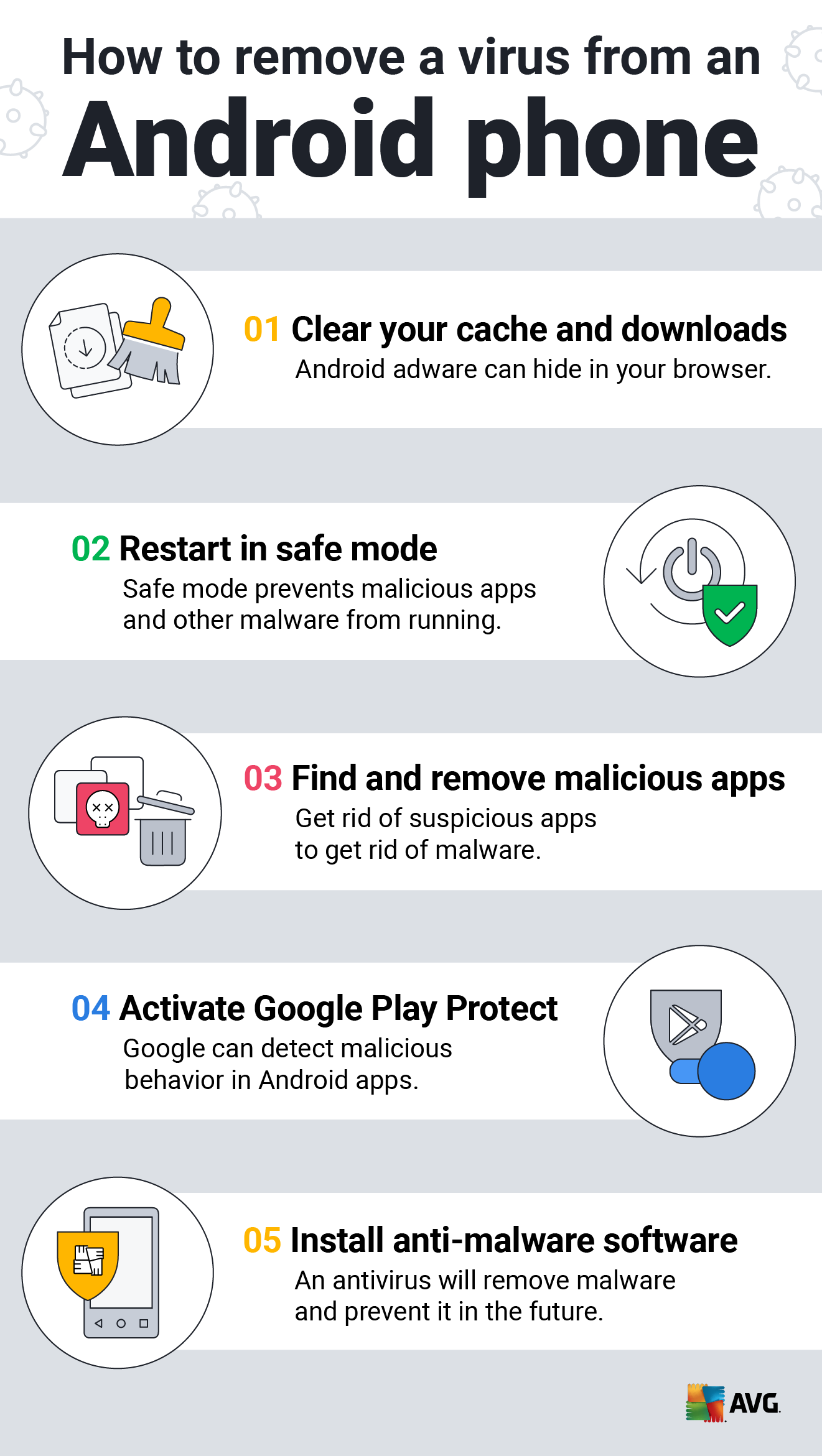
How to Clean an Android or iPhone from Viruses for Free

AV-TEST Confirms Skyhigh Security Service Edge Delivers Superior Threat Protection in All Test Categories

Malware Analysis: Steps & Examples - CrowdStrike

Detail procedure of malware analysis
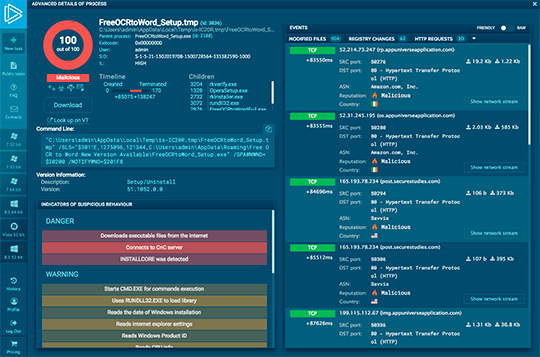
Interactive Online Malware Sandbox

Malware analysis Program_Install_and_Uninstall Malicious activity

What is Malware? Definition, Types, Prevention - TechTarget

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Rising threats: Cybercriminals unleash 411,000 malicious files daily in 2023
de
por adulto (o preço varia de acordo com o tamanho do grupo)