Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Protecting Your Network from Cyber Attacks

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey

What is Malware? Definition, Types, Prevention - TechTarget

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

How to Analyze Malware's Network Traffic in A Sandbox
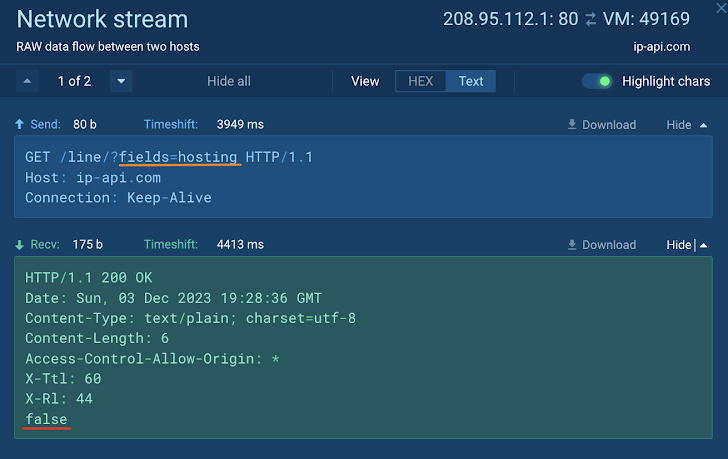
How to Analyze Malware's Network Traffic in A Sandbox

Malware Analysis - What is, Benefits & Types (Easily Explained)
TryHackMe Hacktivities
MetaDefender Cloud Advanced threat prevention and detection
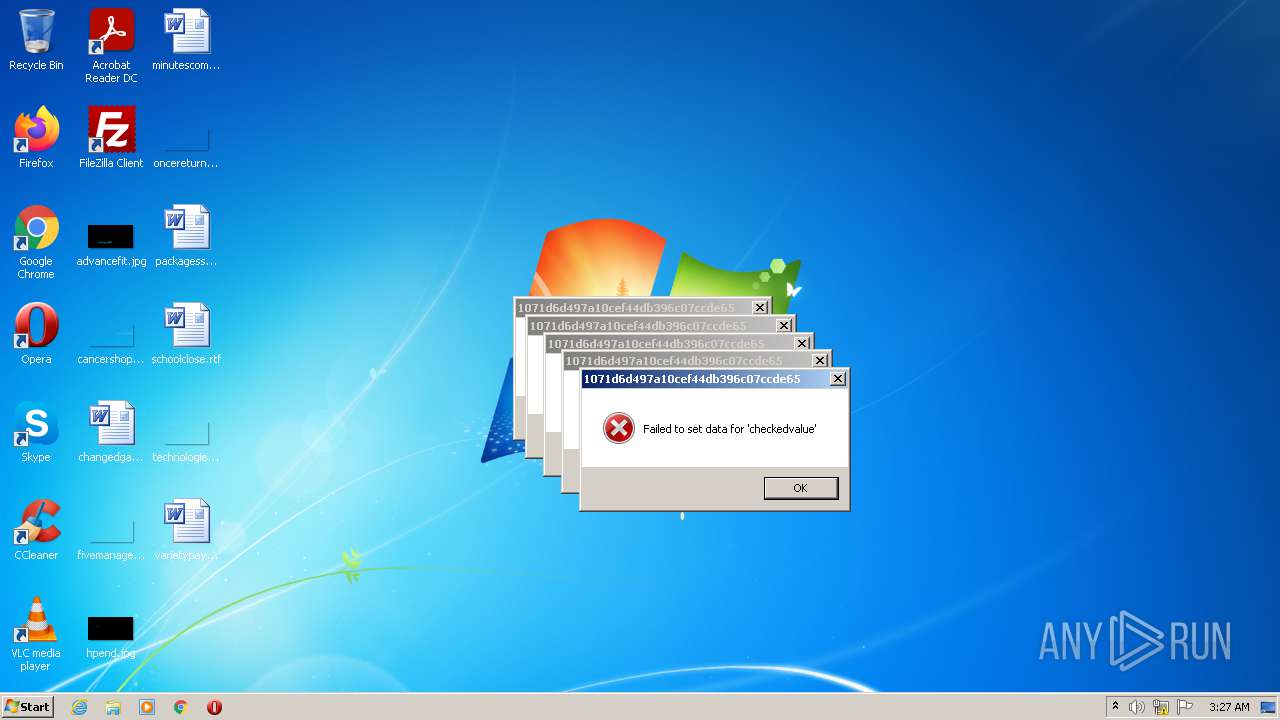
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Free Cybersecurity Training and Career Development

AI and Automation - DZone

Malware Analysis: Steps & Examples - CrowdStrike
de
por adulto (o preço varia de acordo com o tamanho do grupo)




