Malware analysis Malicious activity
Por um escritor misterioso
Descrição

TryHackMe Hacktivities

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1
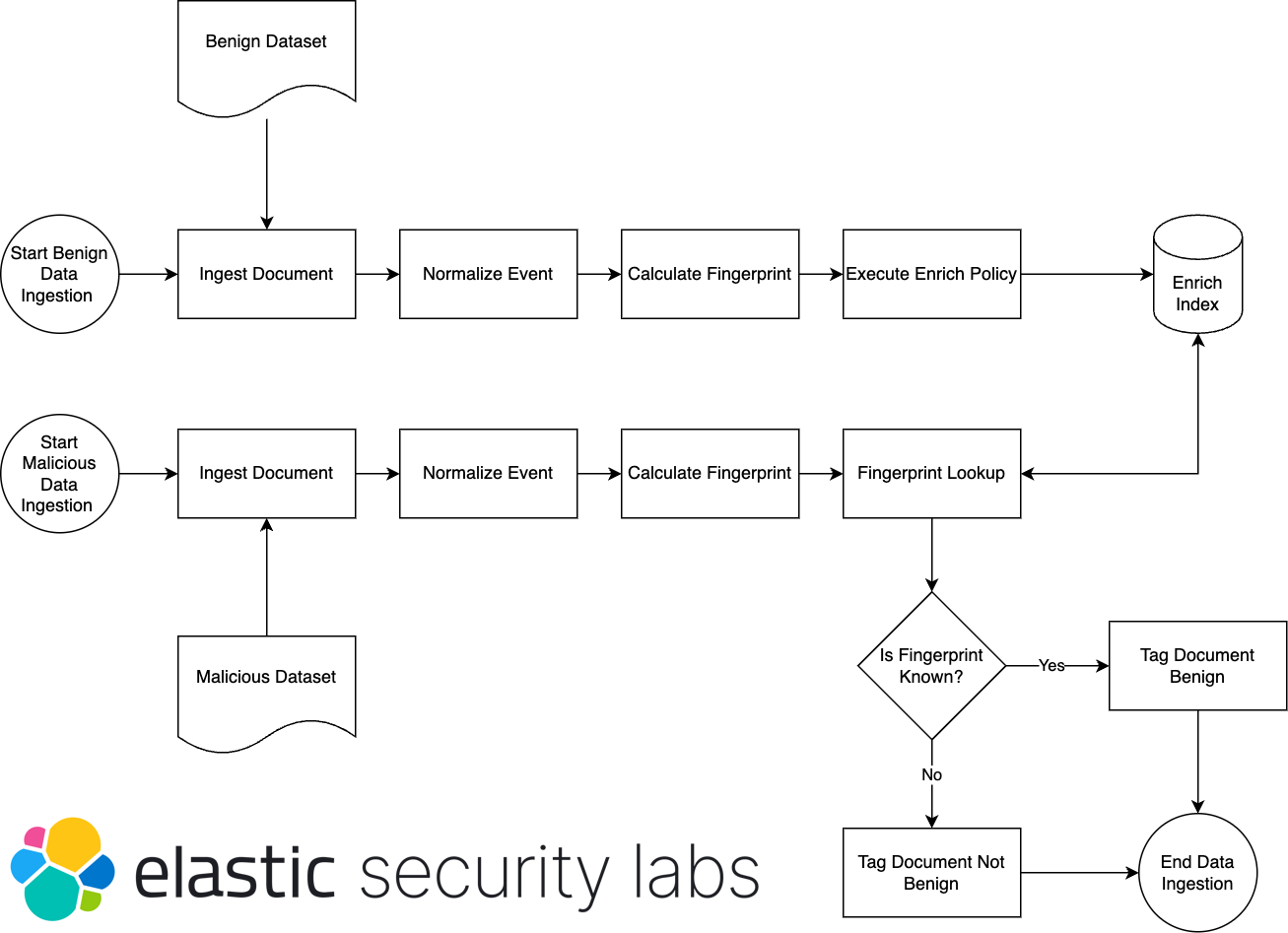
An Elastic approach to large-scale dynamic malware analysis
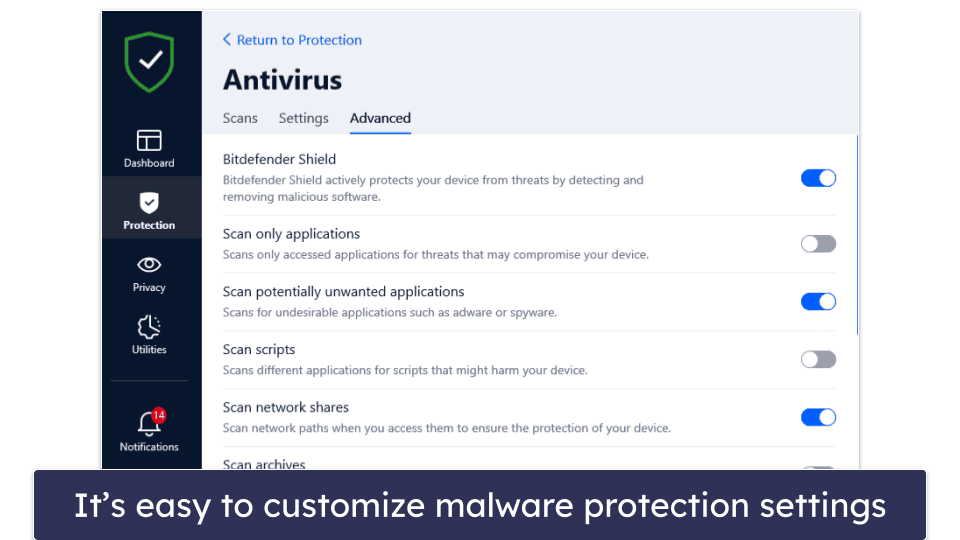
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Unveiling activities of Tropic Trooper 2023 deep analysis of
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Robust Malware Detection Models: Learning From Adversarial Attacks
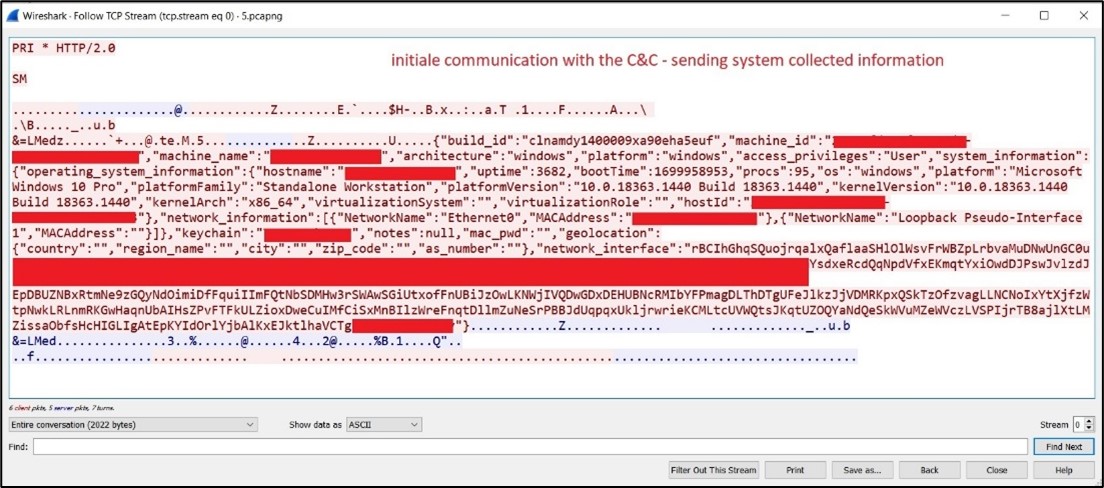
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows
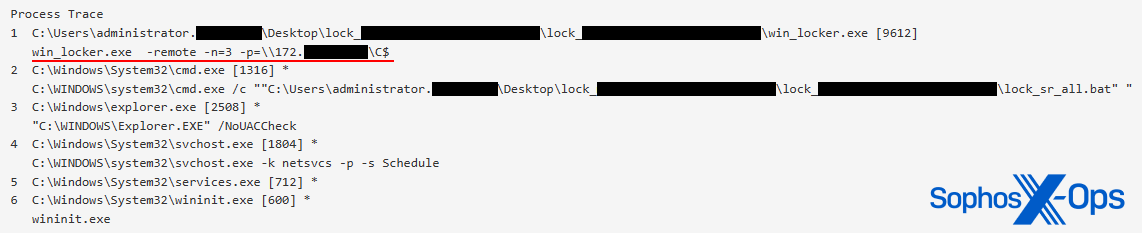
CryptoGuard: An asymmetric approach to the ransomware battle

Security Orchestration Use Case: Automating Malware Analysis

Playbook of the Week: Malware Investigation and Response - Palo

StopRansomware: Rhysida Ransomware

Intro to Malware Analysis: What It Is & How It Works - InfoSec
de
por adulto (o preço varia de acordo com o tamanho do grupo)