Malware analysis Malicious activity
Por um escritor misterioso
Descrição

How to Do Malware Analysis?
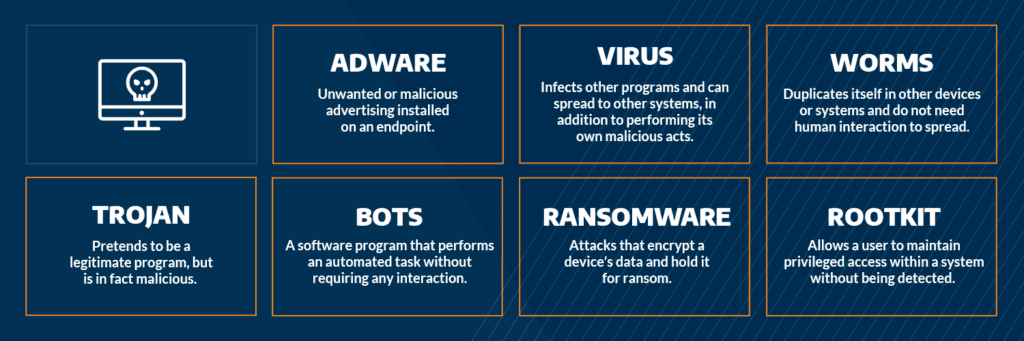
Most Common Malware Attacks

Malware analysis Program_Install_and_Uninstall Malicious activity

Detail procedure of malware analysis

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Malware Analysis: Protecting Your Network from Cyber Attacks

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Malware analysis Release.zip Malicious activity
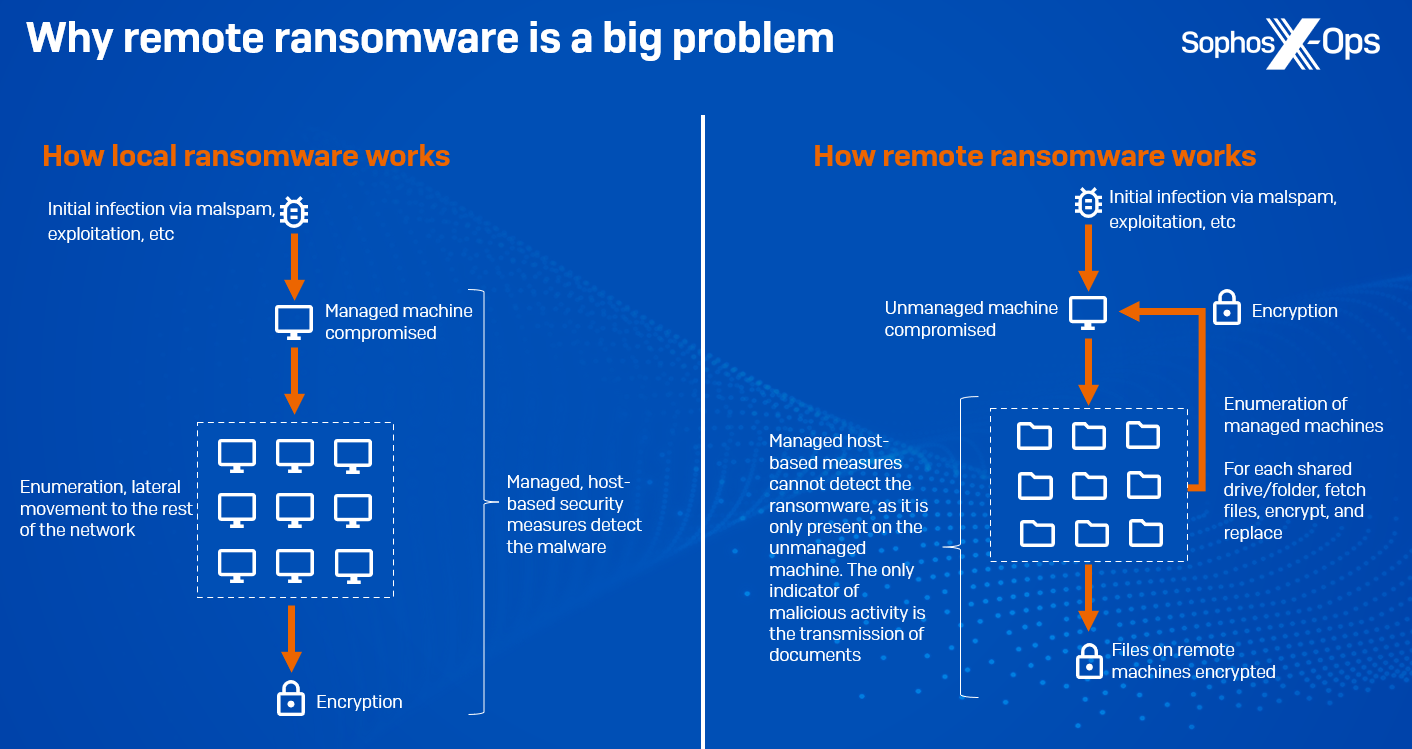
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News

Malware analysis mykey_.rar Malicious activity

What is Malware? Definition, Types, Prevention - TechTarget

Comprehensive Protection Strategies Against Cyber Threats

Malware analysis index.html Malicious activity

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
de
por adulto (o preço varia de acordo com o tamanho do grupo)