Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

What to Include in a Malware Analysis Report
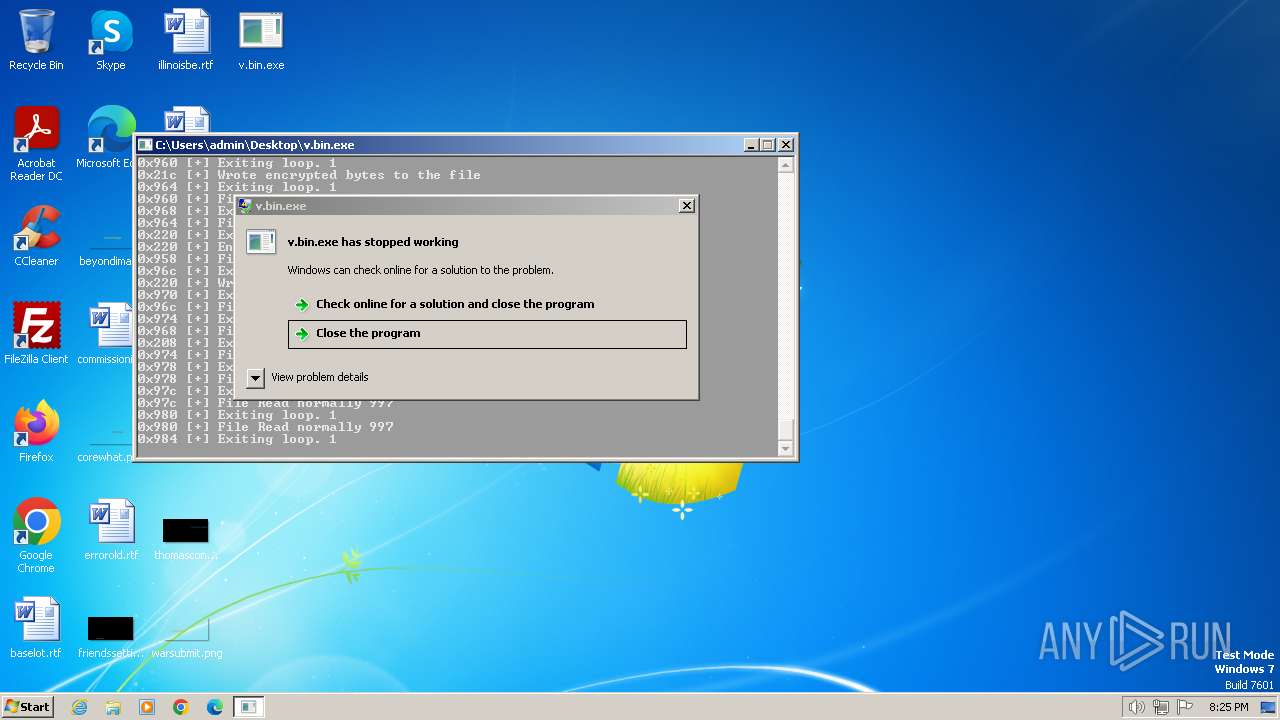
Malware analysis v.bin Malicious activity

Interactive Online Malware Sandbox

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Malware analysis Program_Install_and_Uninstall Malicious activity

PROUD-MAL: static analysis-based progressive framework for deep

Endpoint Detection and Response, Free - What is EDR Security?

What Is Malware Analysis? Definition, Types, Stages, and Best

Routers Roasting on an Open Firewall: the KV-botnet Investigation
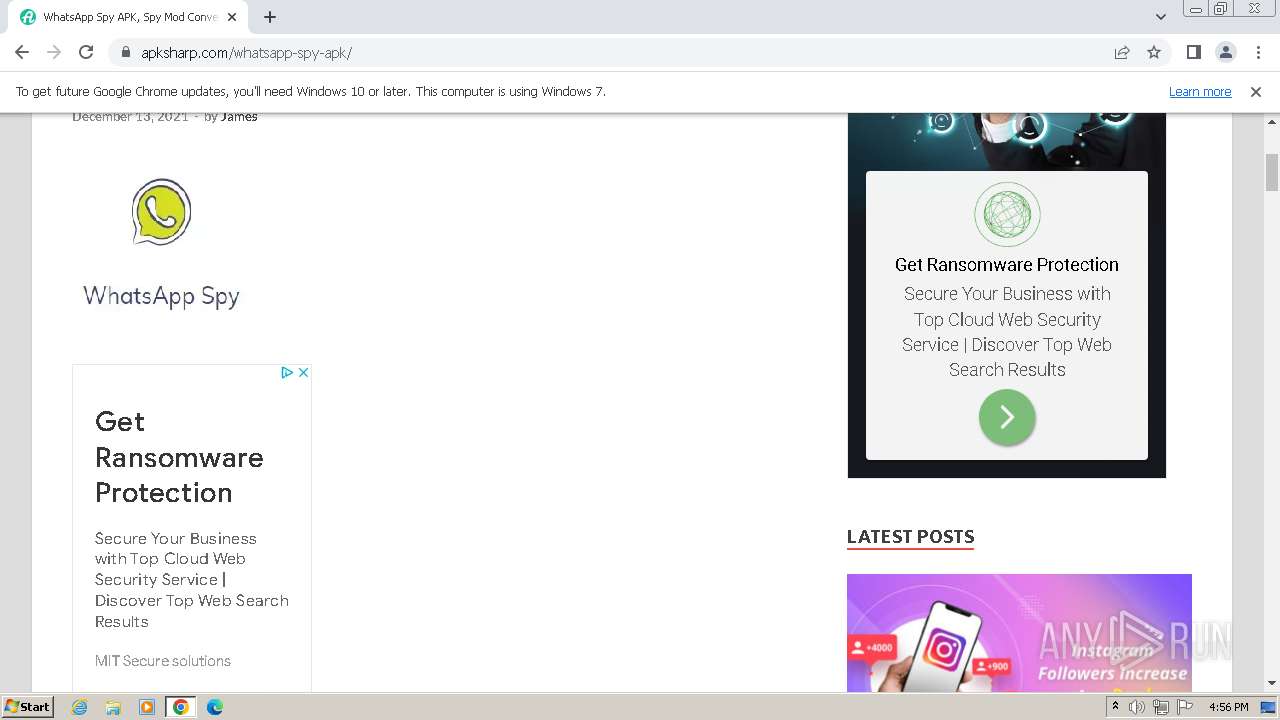
Malware analysis apksharp.com Malicious activity

Security Orchestration Use Case: Automating Malware Analysis

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging
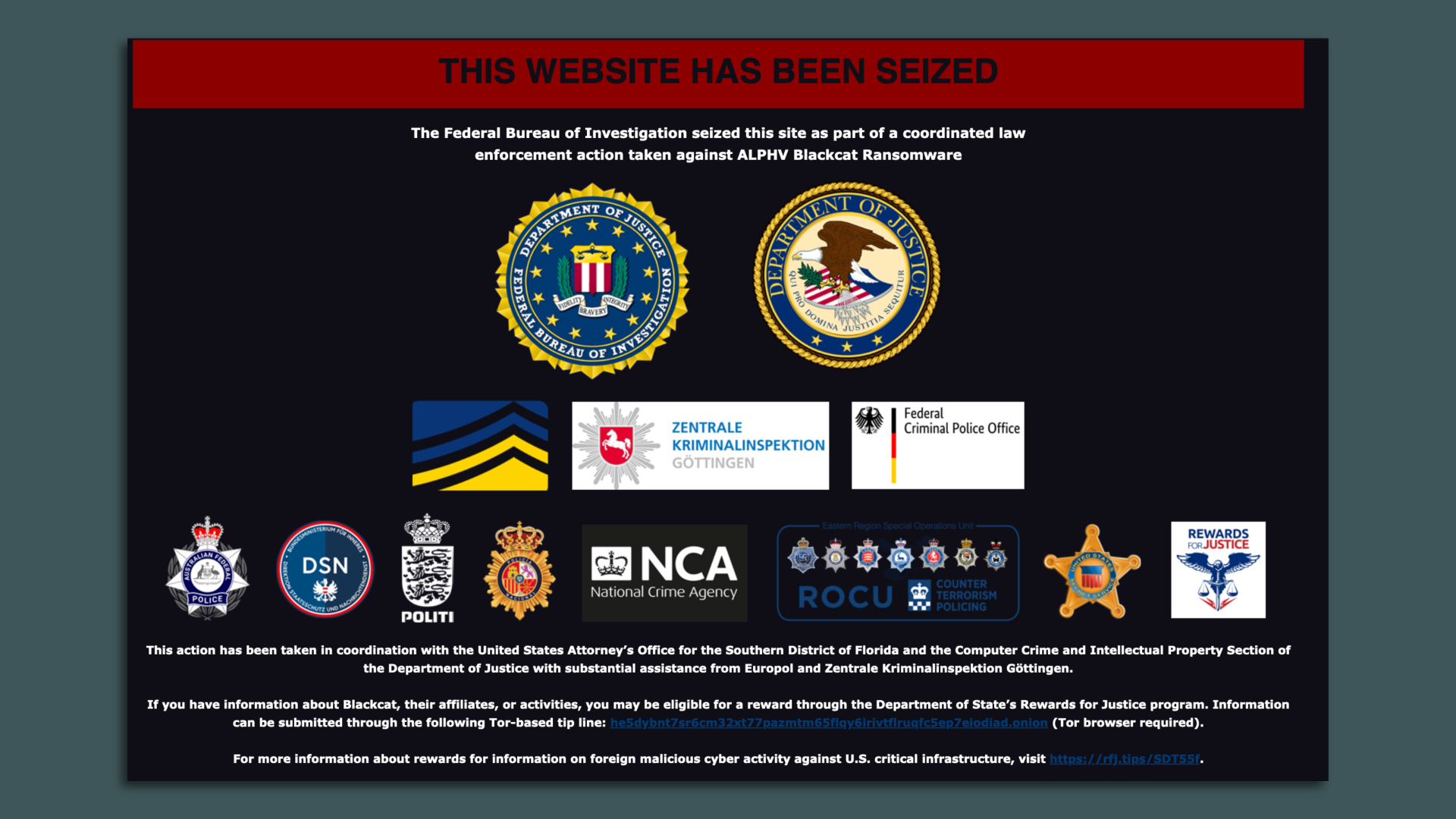
U.S. law enforcement seizes BlackCat ransomware site, distributes
Malware analysis
de
por adulto (o preço varia de acordo com o tamanho do grupo)







