Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
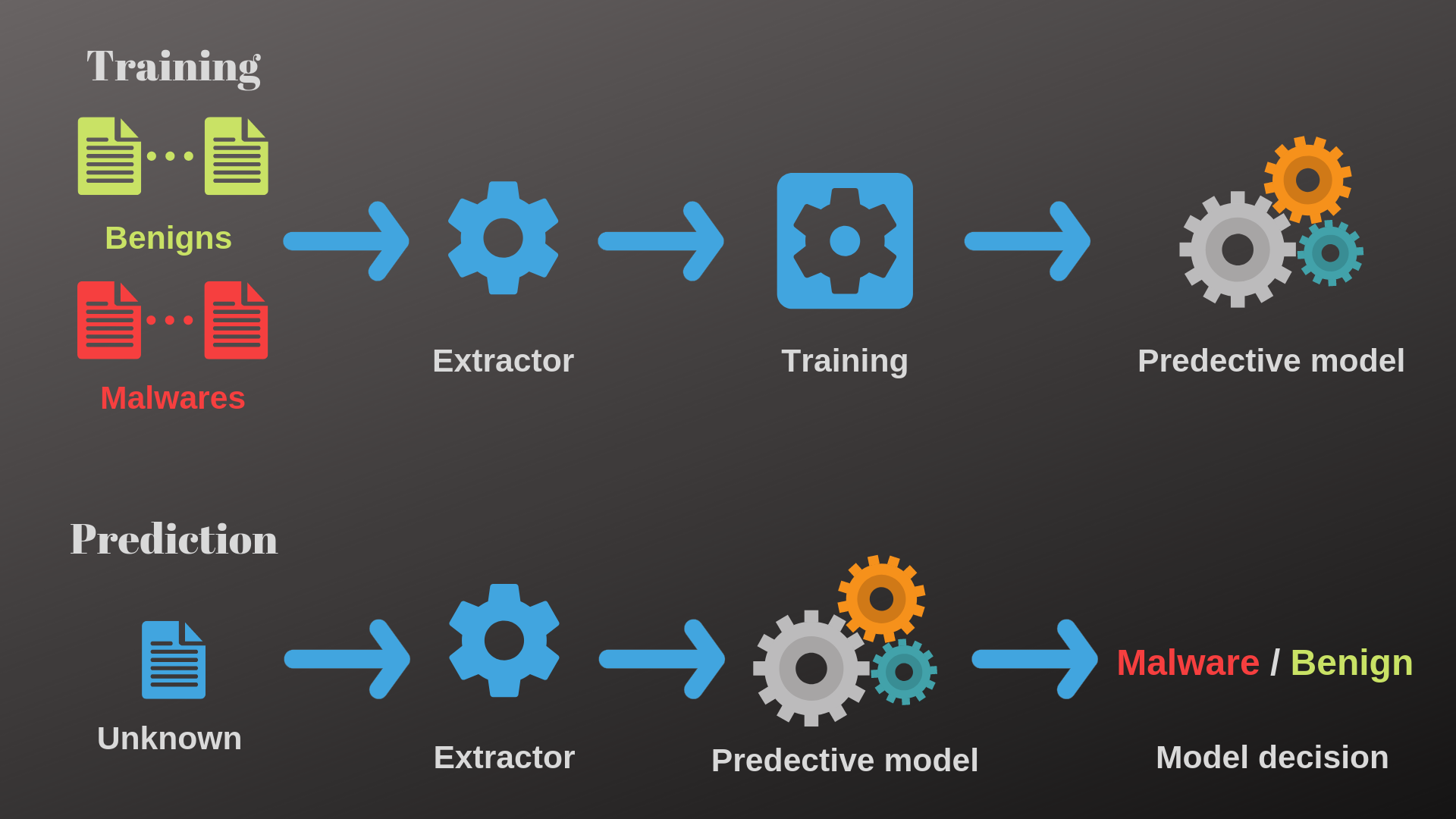
Feature Extraction and Detection of Malwares Using Machine Learning

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Malware Analysis: Steps & Examples - CrowdStrike

Comprehensive Protection Strategies Against Cyber Threats
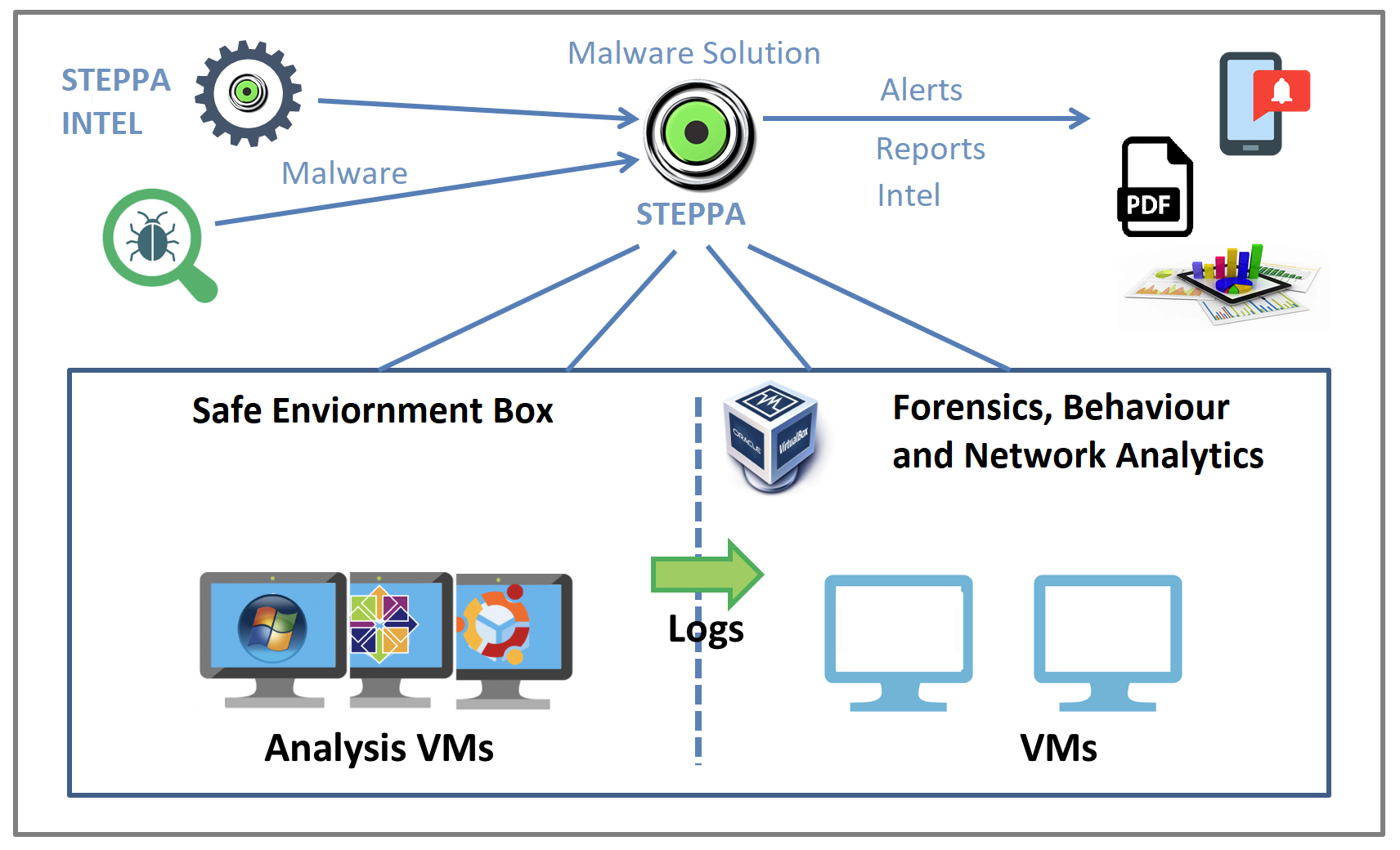
Malware Analysis Solution: Analyze, Detect, and Protect

Endpoint Detection and Response, Free - What is EDR Security?
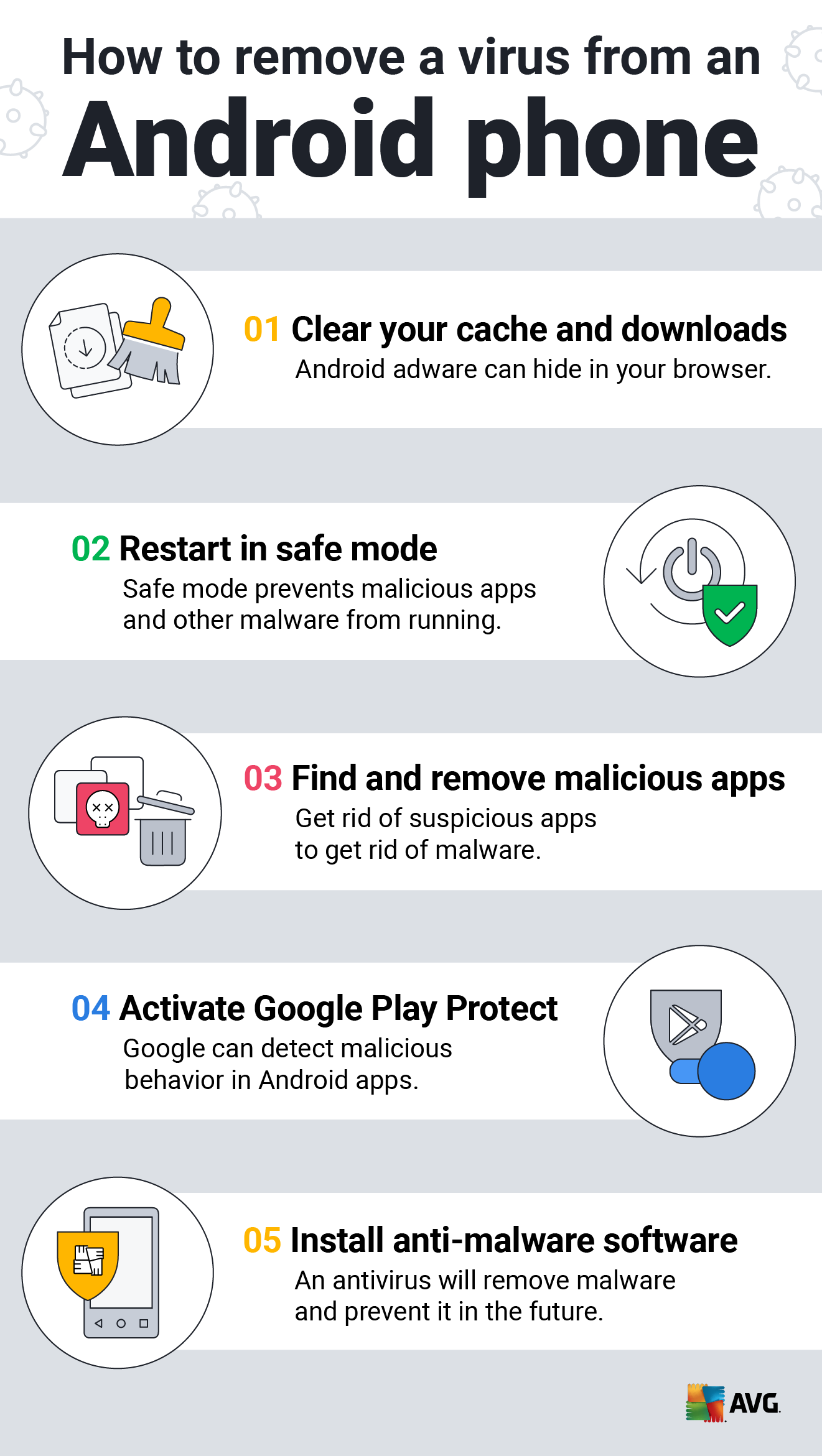
How to Clean an Android or iPhone from Viruses for Free
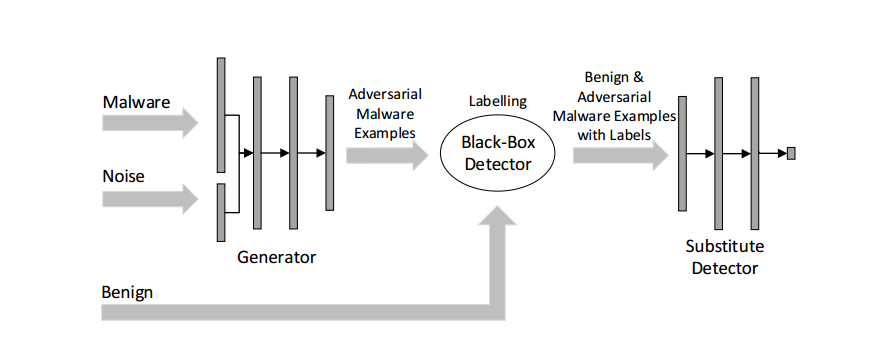
Malware Detection

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Remediation and Malware Detection Overview

Malware analysis file Malicious activity
de
por adulto (o preço varia de acordo com o tamanho do grupo)