Malware analysis
Por um escritor misterioso
Descrição

Malware Analysis Benefits Incident Response
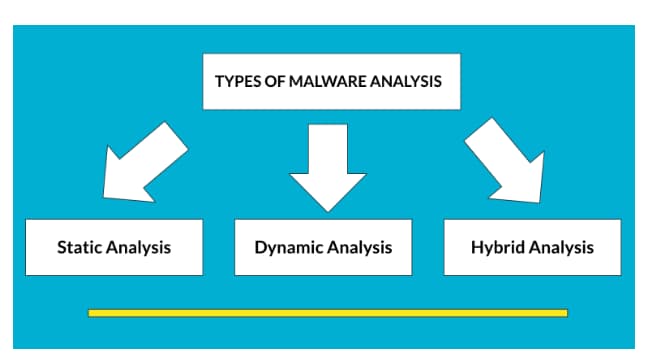
Malware Analysis: Techniques and Tools

Malware Analysis - Credly

How to Do Malware Analysis?

Remediation and Malware Detection Overview

Malware Analysis: Steps & Examples - CrowdStrike
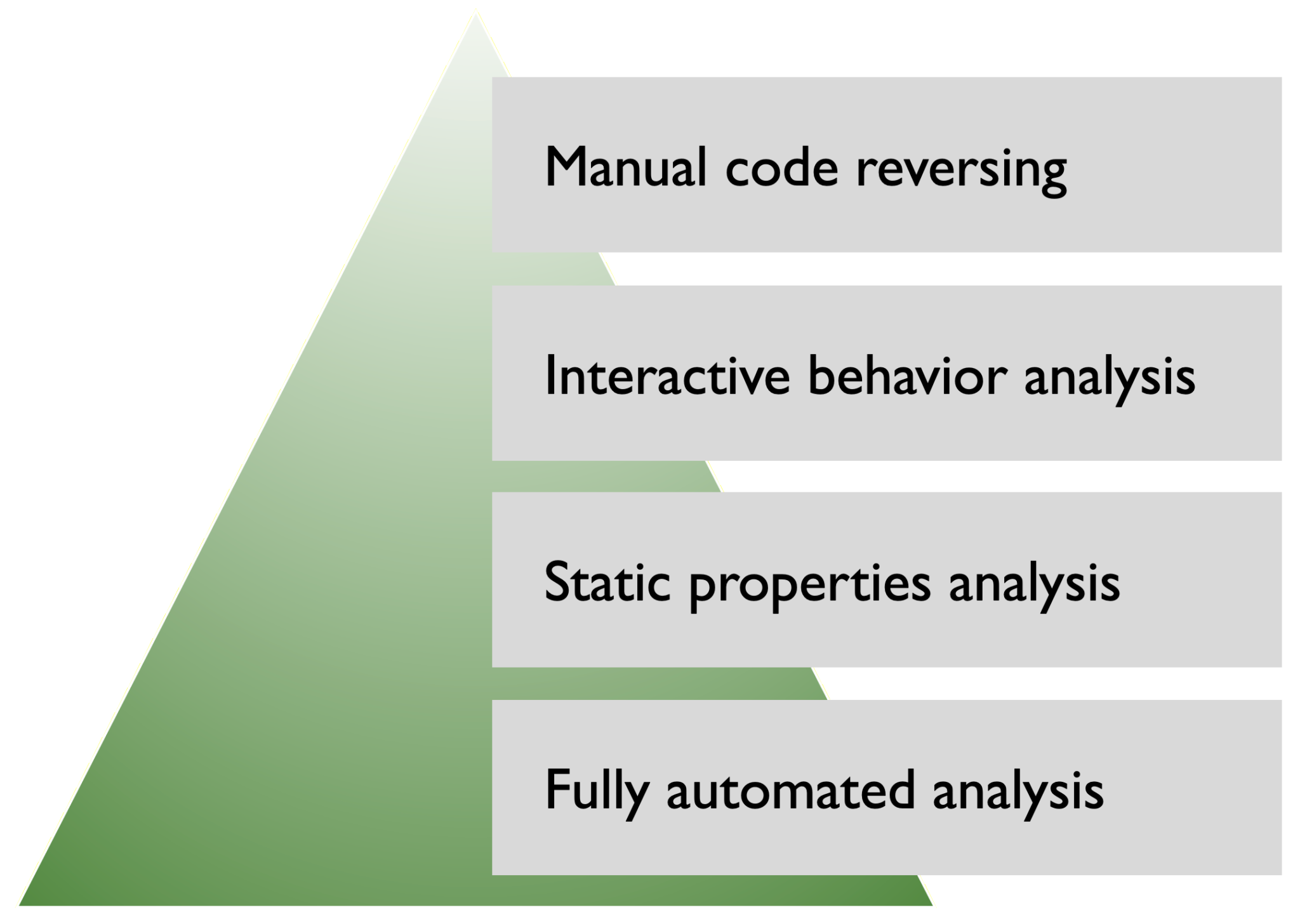
How You Can Start Learning Malware Analysis

Malware analysis reports
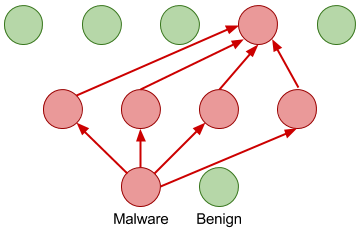
Malware Detection in Executables Using Neural Networks

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A, Monnappa K: Books

Detail procedure of malware analysis

Malware Analysis Explained - 's Cybersecurity Blog

Malware Analysis - Supersuso - CYFIRMA

What Is Dynamic Malware Analysis?

Malware Analysis - What is, Benefits & Types (Easily Explained)
de
por adulto (o preço varia de acordo com o tamanho do grupo)