License to Kill: Leveraging License Management to Attack ICS Networks
Por um escritor misterioso
Descrição
Claroty researchers have uncovered six critical vulnerabilities in Wibu-Systems’ CodeMeter third-party license management component, which could expose OT environments across numerous industries to exploits via phishing campaigns or direct attacks.
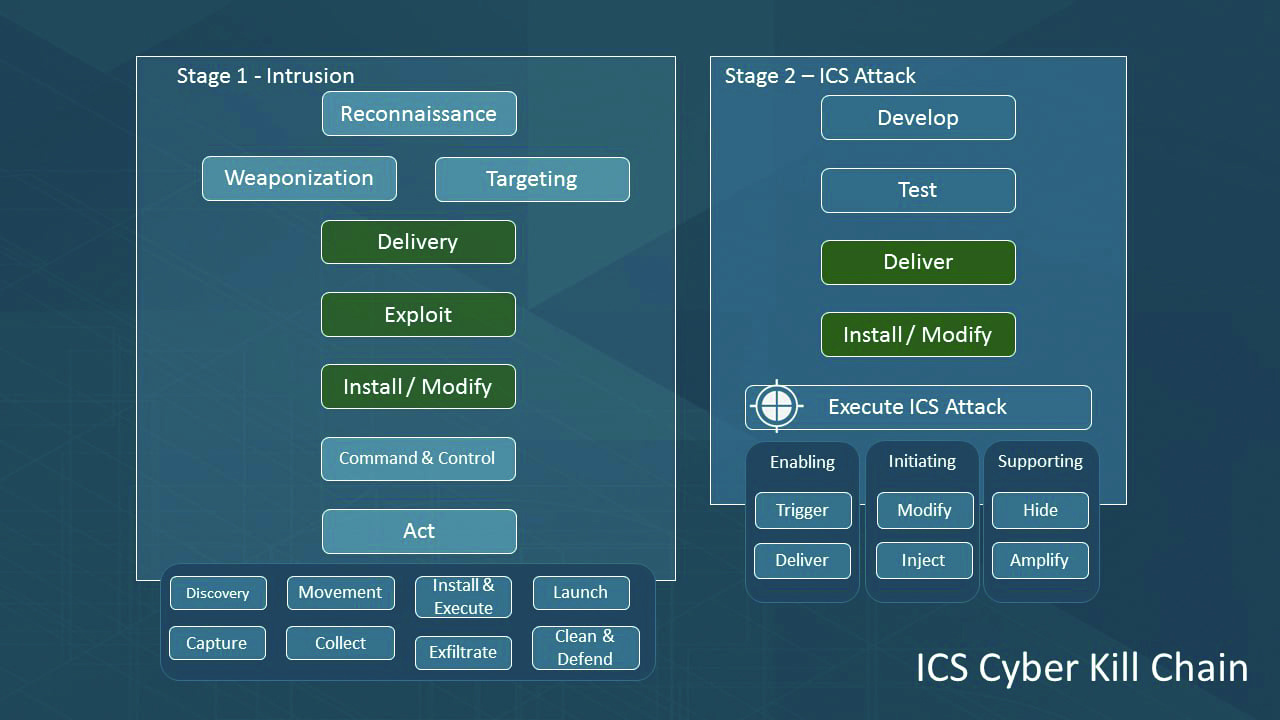
Malware in Modern ICS: Understanding Impact While Avoiding Hype
-min.png)
BlastShield White Paper
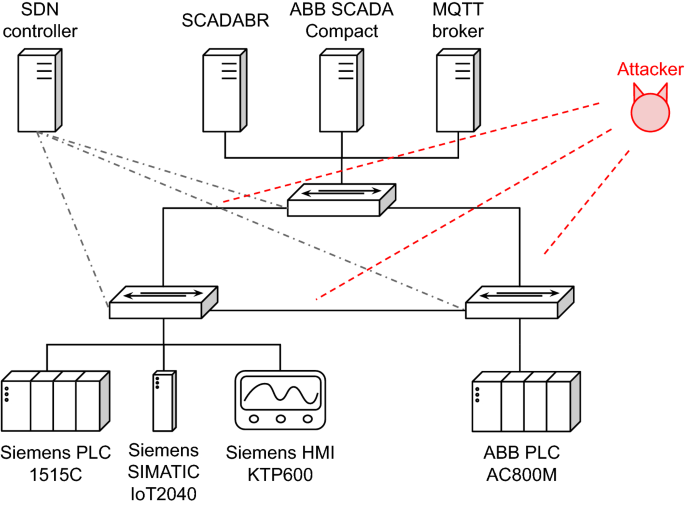
Low delay network attributes randomization to proactively mitigate reconnaissance attacks in industrial control systems

COVID-19 Cybersecurity Alerts, Coronavirus Phishing Scam, Covid 19 Malware, Cyware
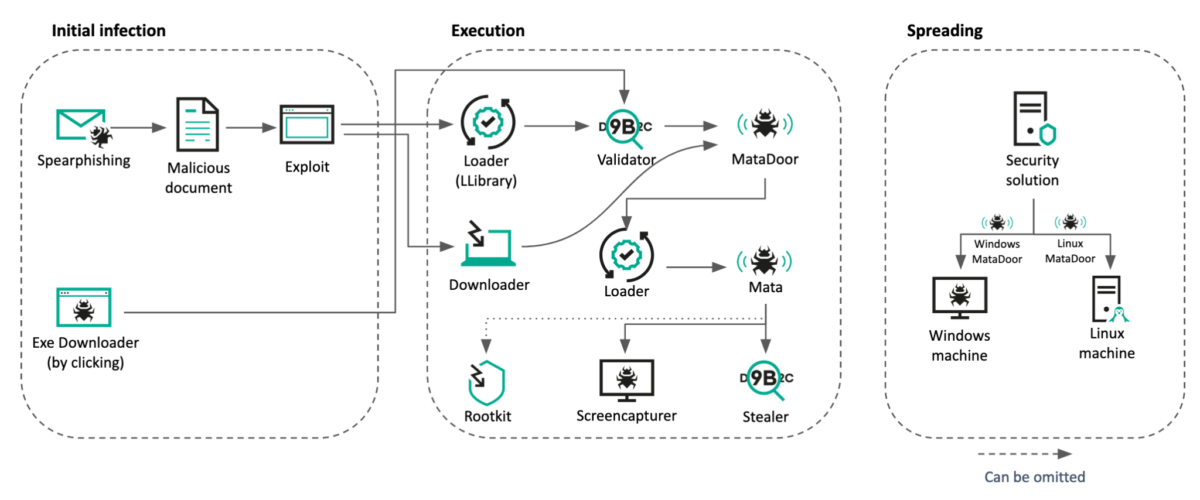
Updated MATA attacks industrial companies in Eastern Europe
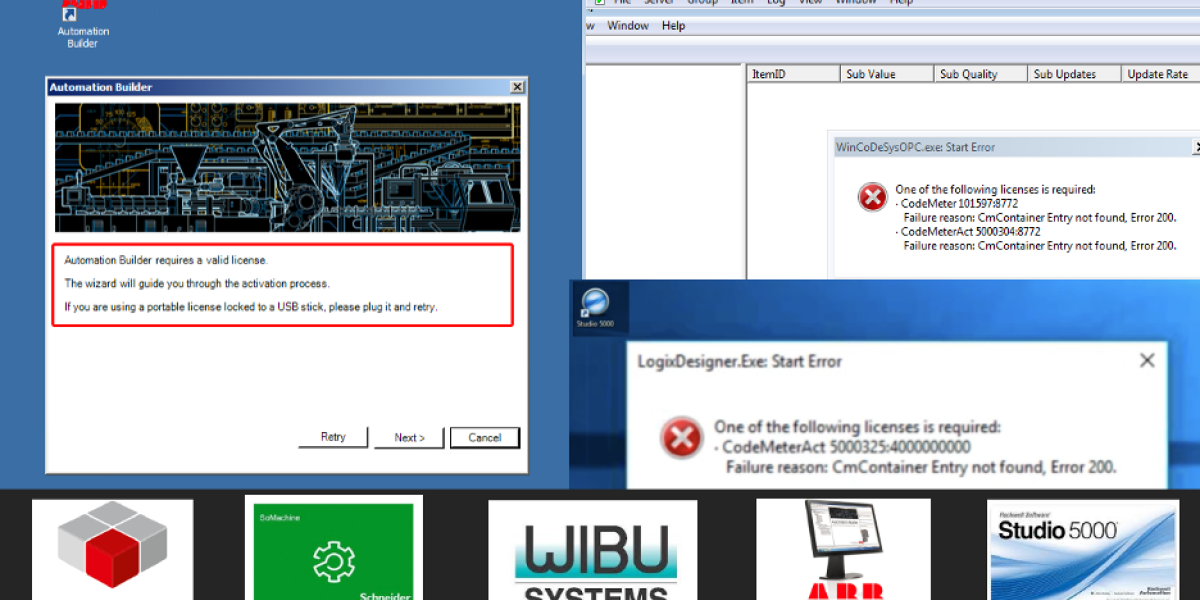
Wibu-Systems CodeMeter Vulnerabilities Expose OT Networks
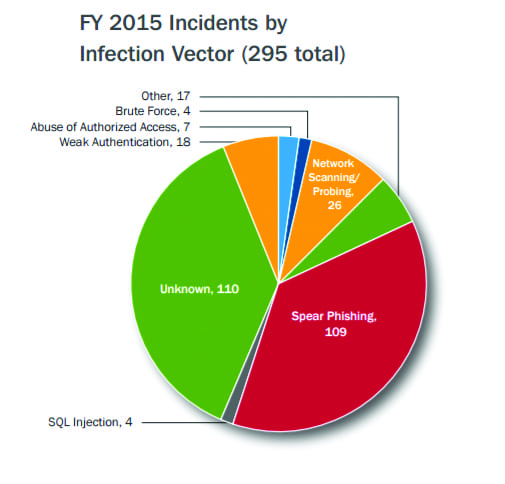
Malware in Modern ICS: Understanding Impact While Avoiding Hype
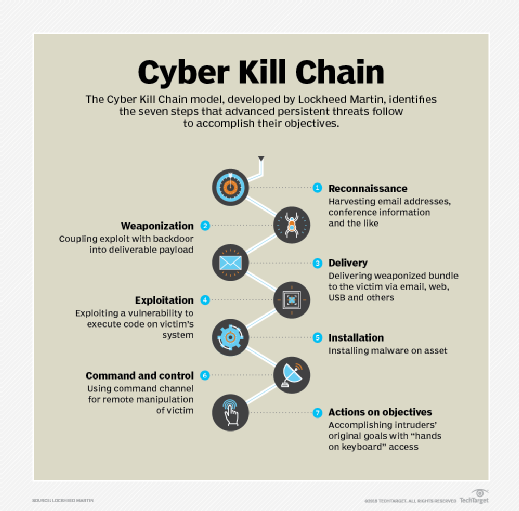
Tackle ICS IoT security challenges with 6 processes

What Happens When Malware Targets Process Safety Systems?, Chemical Processing
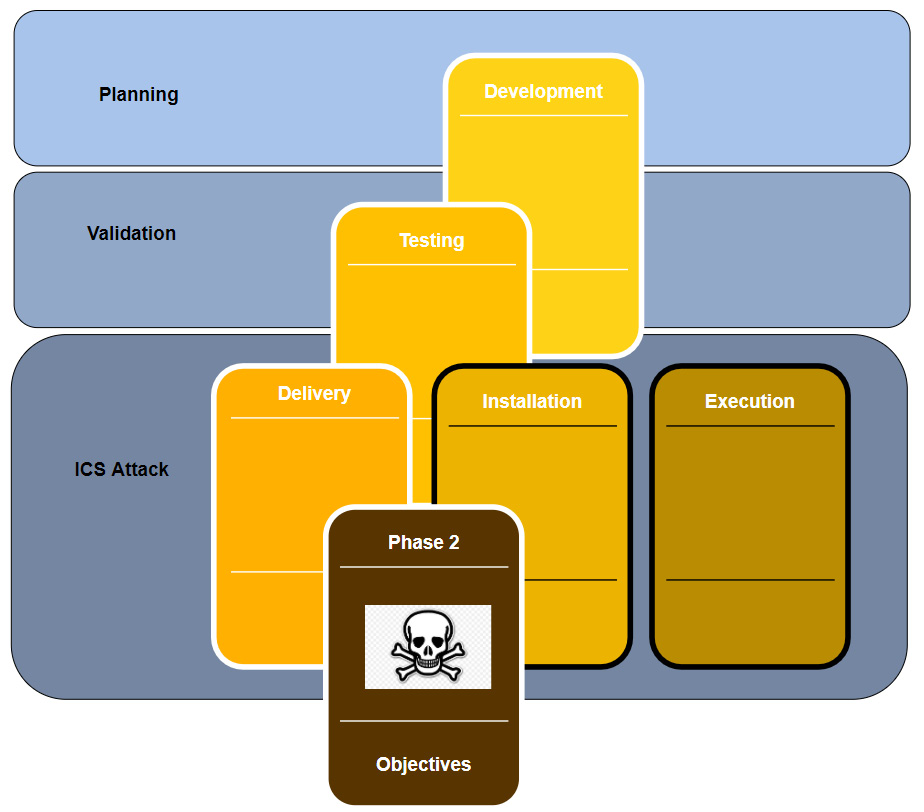
How to Pentest ICS Environments - Packt - SecPro
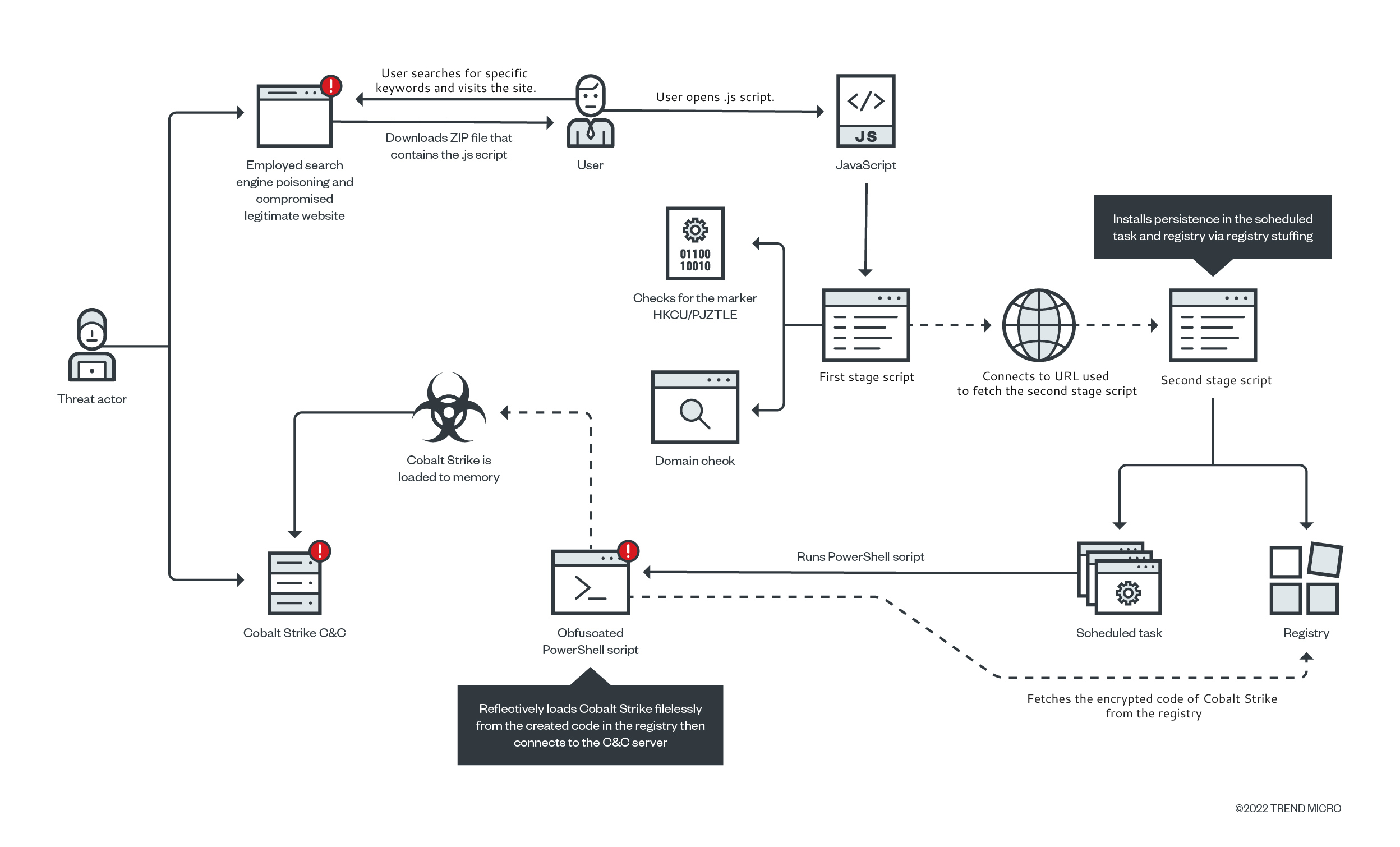
Gootkit Loader's Updated Tactics and Fileless Delivery of Cobalt Strike
PDF) Keeping Host Sanity for Security of the SCADA Systems

Leveraging Attack Surface Management Tactics to Improve ICS Security
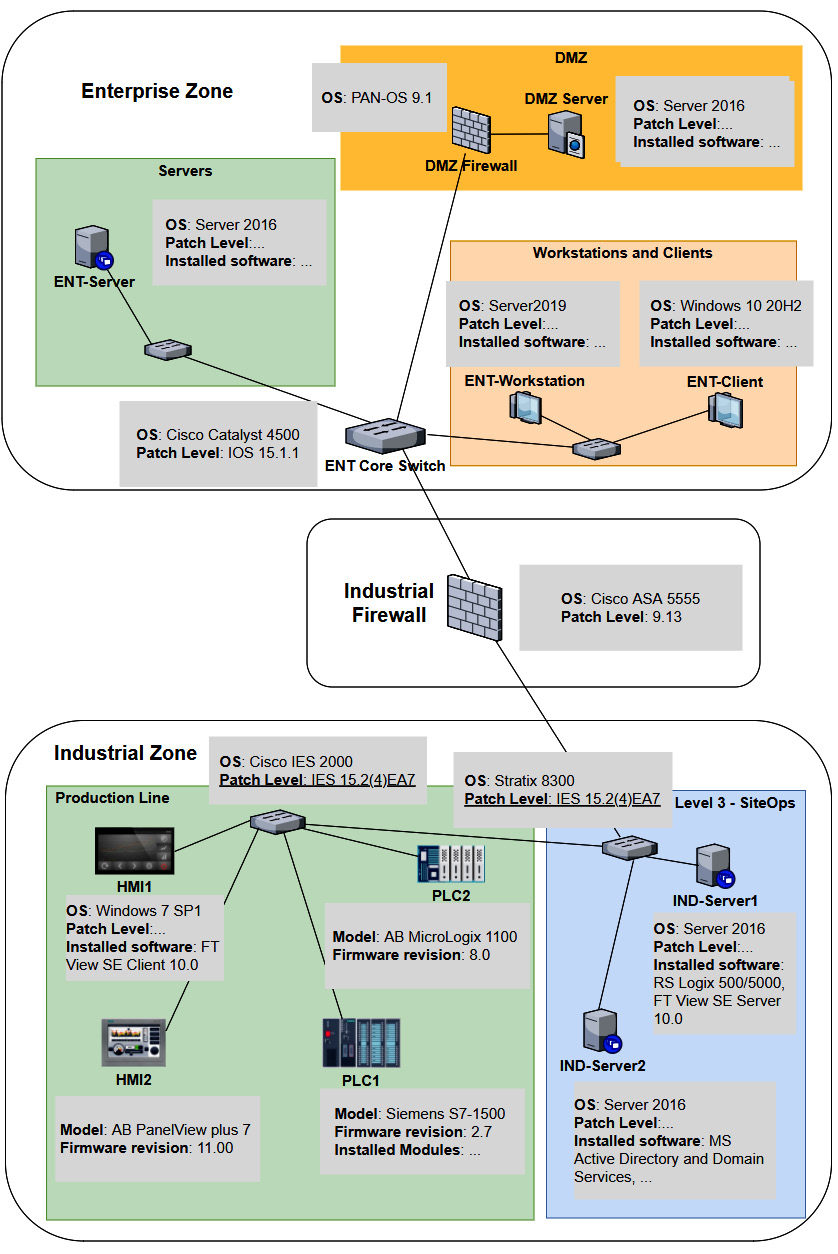
How to Pentest ICS Environments - Packt - SecPro
de
por adulto (o preço varia de acordo com o tamanho do grupo)