Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Descrição
Describing activities of a crime group attacking Ukraine.

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

ISACA Now Blog Global Perspectives & Real-Time Insights

Google: Former Conti ransomware members attacking Ukraine

Targeted Cyberattacks: A Superset of Advanced Persistent Threats
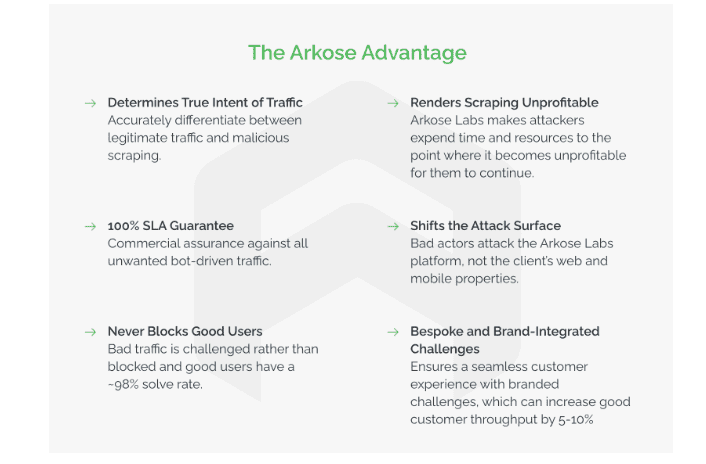
Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Into the Hashed Realm: Understanding the Privacy Risks Associated with the Use of Hashed Emails for Advertising, by Tolulope Ogundele
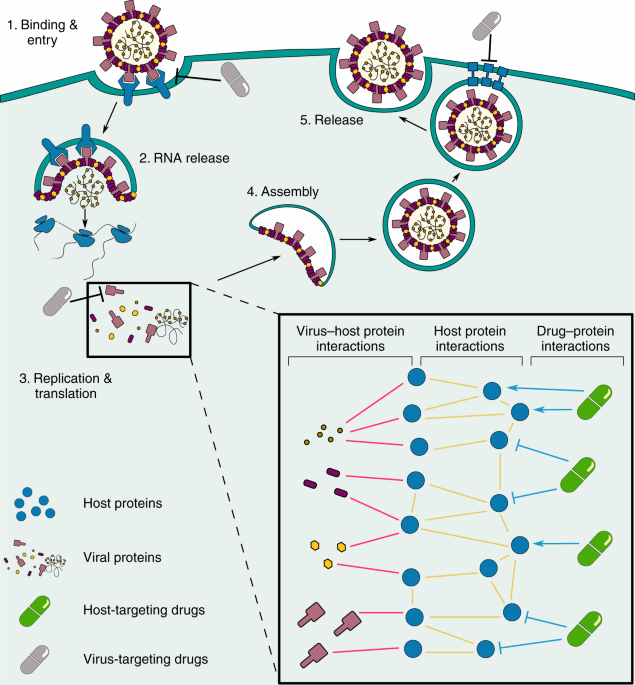
Exploring the SARS-CoV-2 virus-host-drug interactome for drug repurposing
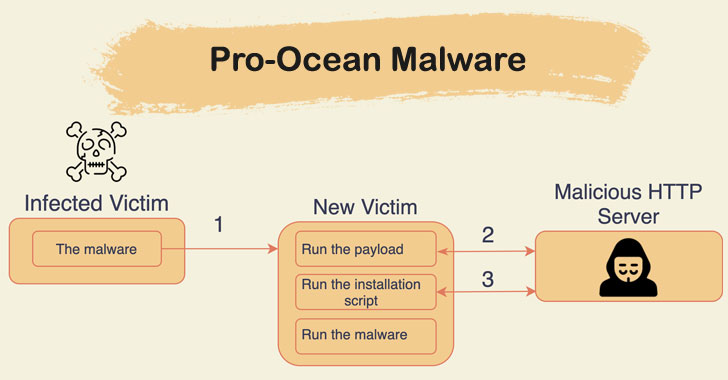
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database
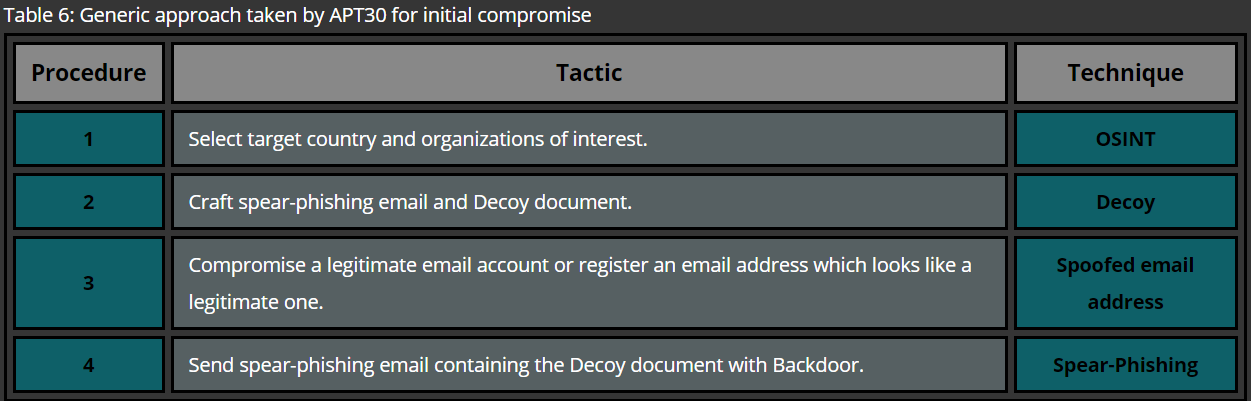
Initial Compromise

Security in product lifecycle of IoT devices: A survey - ScienceDirect

The State of Healthcare Cybersecurity: VMware Carbon Black Explores the Surge in Cyber Threats
de
por adulto (o preço varia de acordo com o tamanho do grupo)





