IT threat evolution Q3 2022
Por um escritor misterioso
Descrição
Recent APT campaigns, a sophisticated UEFI rootkit, new ransomware for Windows, Linux and ESXi, attacks on foreign and crypto-currency exchanges, and malicious packages in online code repositories.

Malware Statistics in 2023: Frequency, impact, cost & more
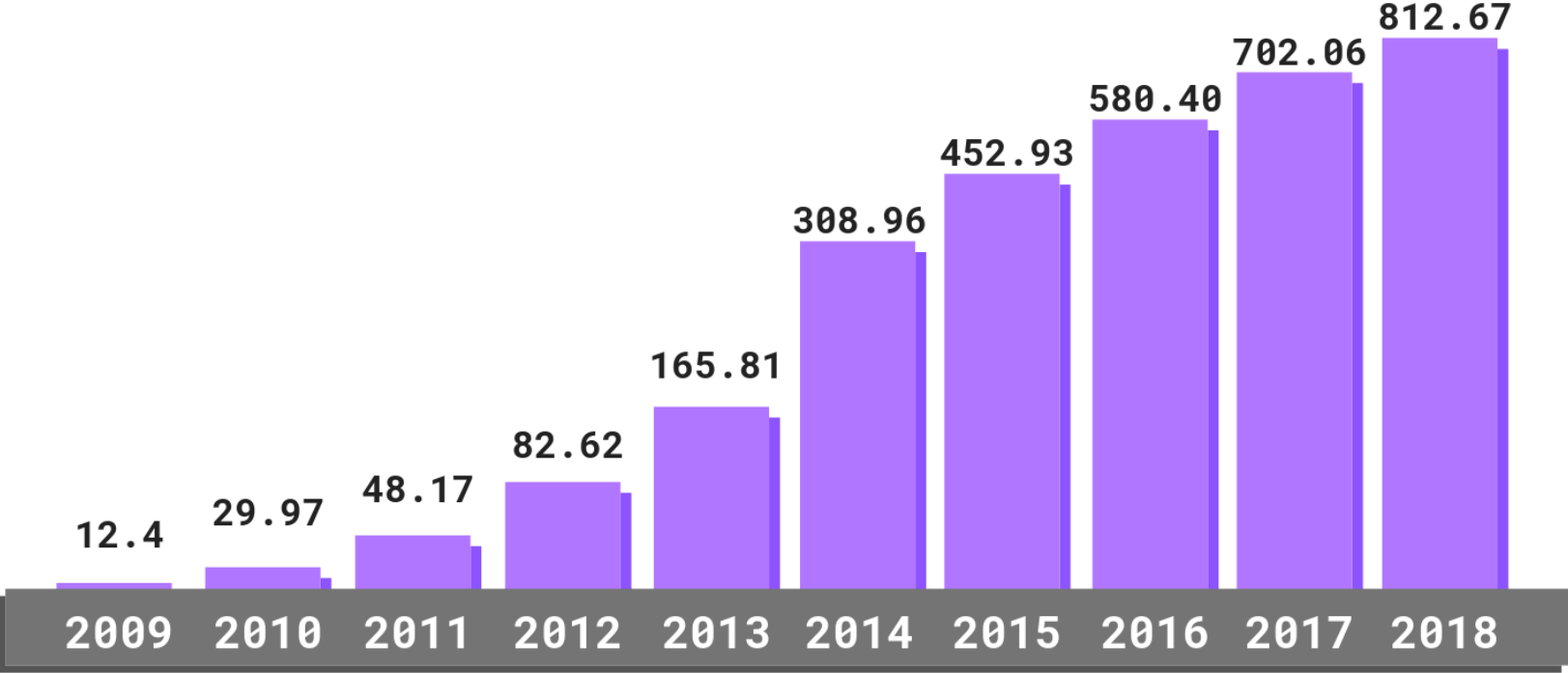
2023 Cyber Security Statistics: The Ultimate List Of Stats, Data & Trends
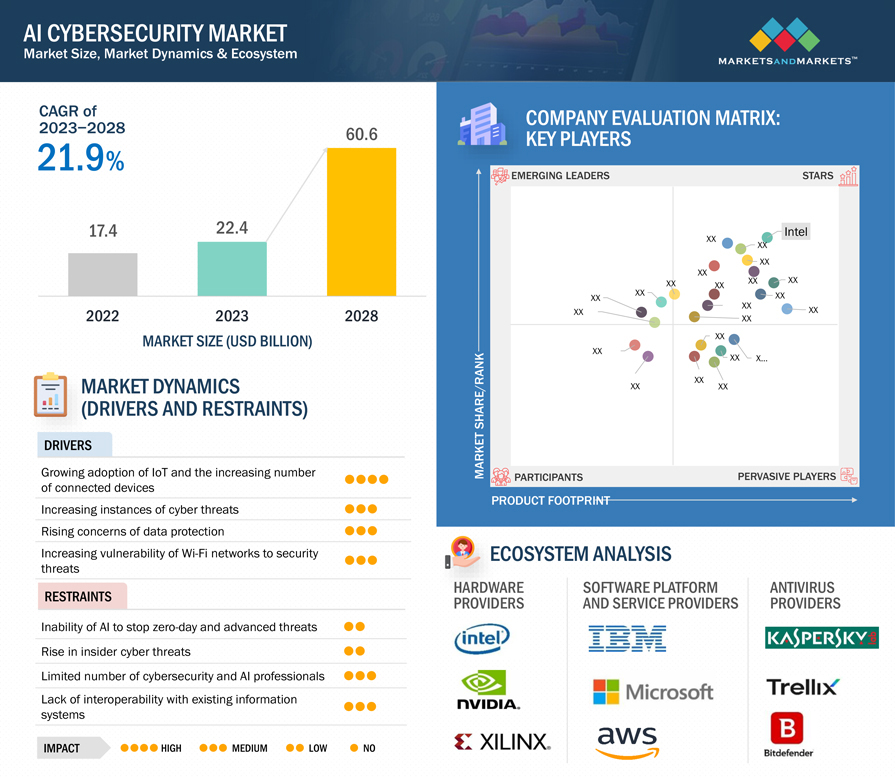
AI in cybersecurity Market Size, Growth Opportunities, Industry Trends and Analysis 2030
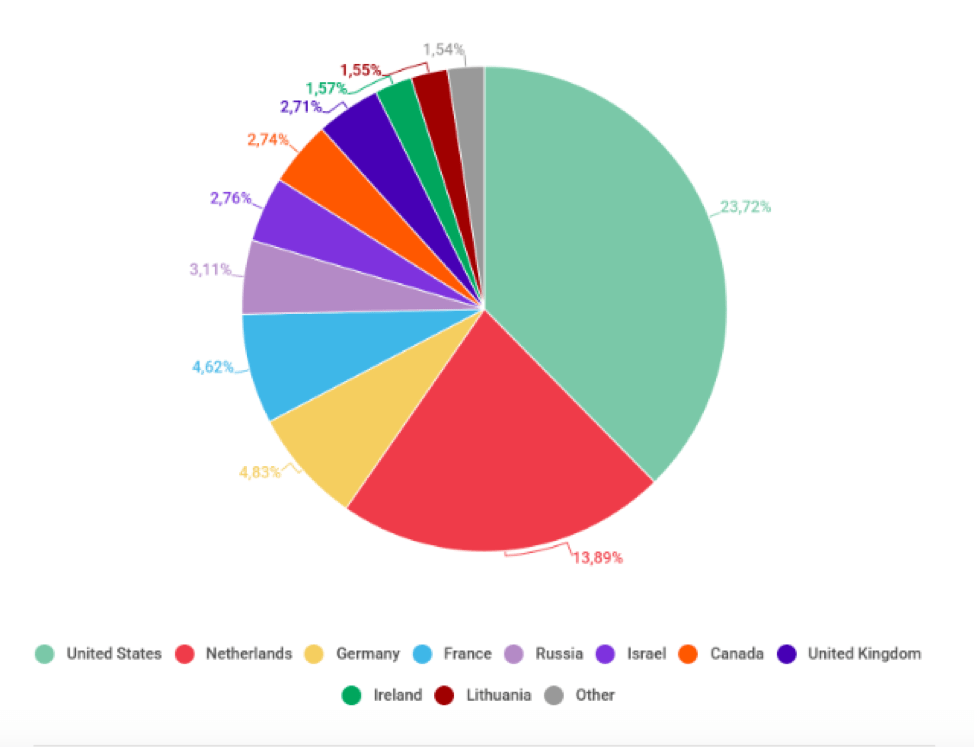
Half of the Malware Detected in 2019 was Classified as Zero-Day Threats, Making it the Most Common Malware to Date - Cynet

IT threat evolution Q3 2020 Mobile statistics
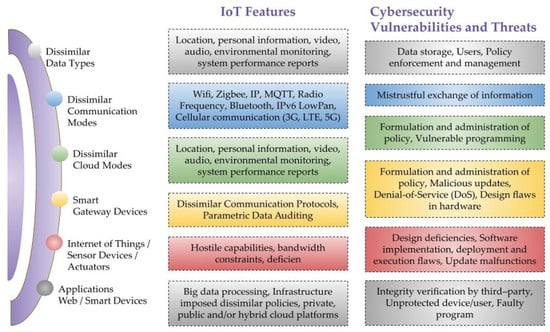
Sensors, Free Full-Text

PC malware statistics, Q3 2023
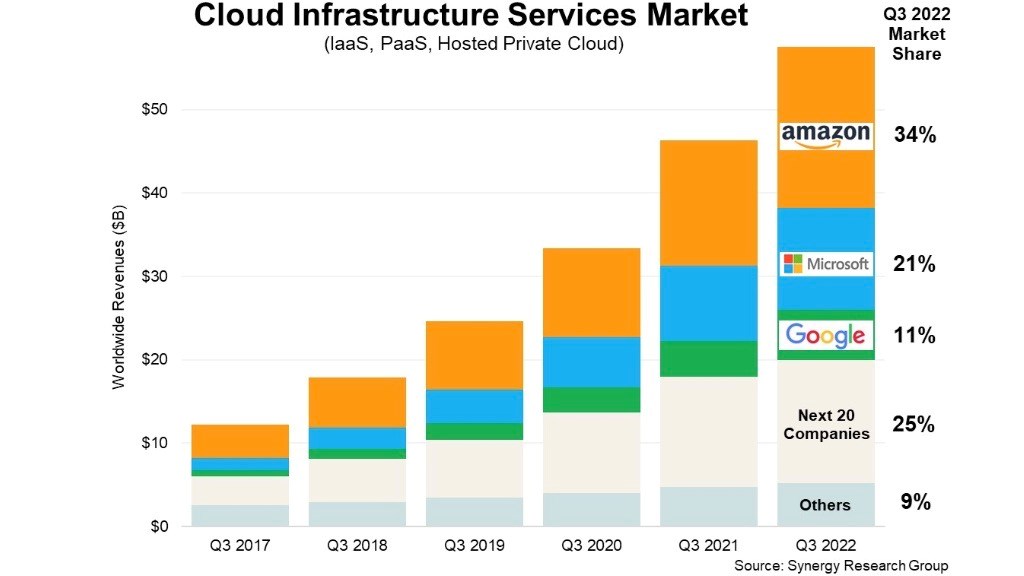
Google gaining market share in $220bn+ cloud infrastructure market

IT threat evolution in Q2 2022. Mobile statistics
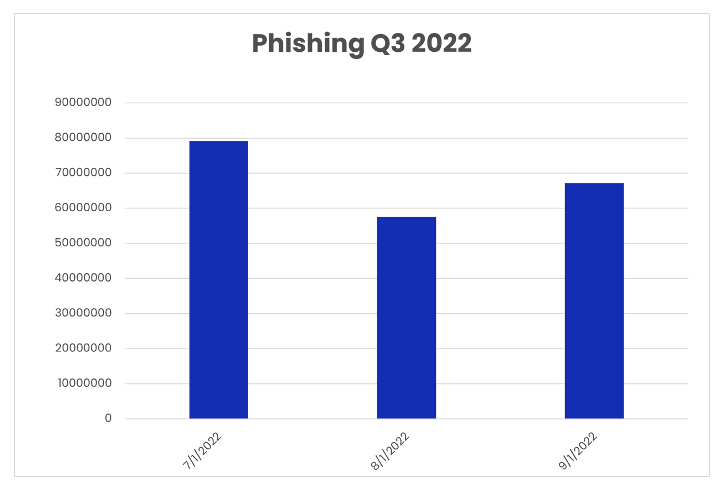
Q3 2022 Phishing and Malware Report: Phishing Volumes Increase 31%

Delivery of Malware: A Look at Phishing Campaigns in Q3 2022

Octo Tempest crosses boundaries to facilitate extortion, encryption, and destruction
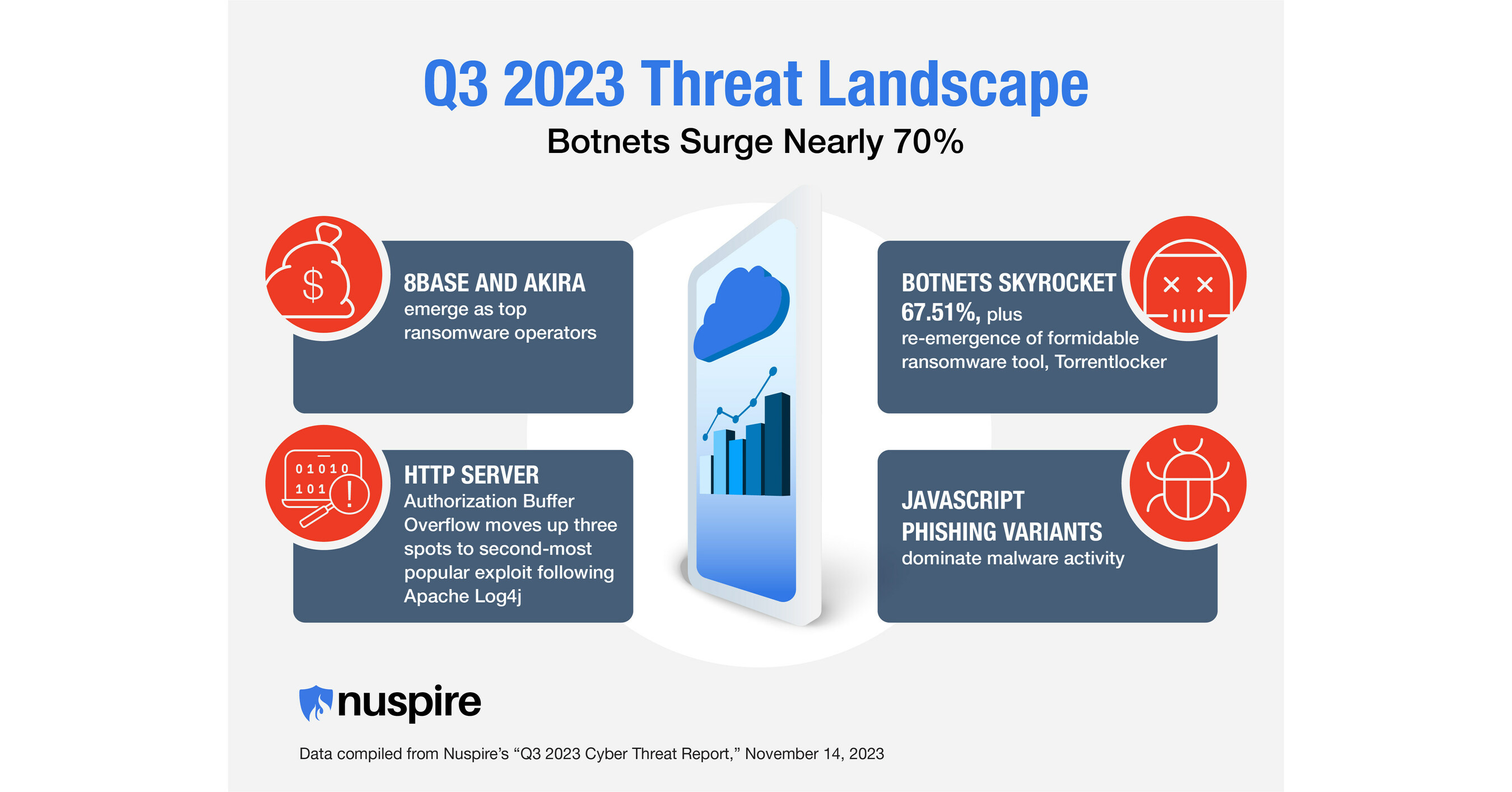
Botnet Activity Surges in Q3 2023
de
por adulto (o preço varia de acordo com o tamanho do grupo)