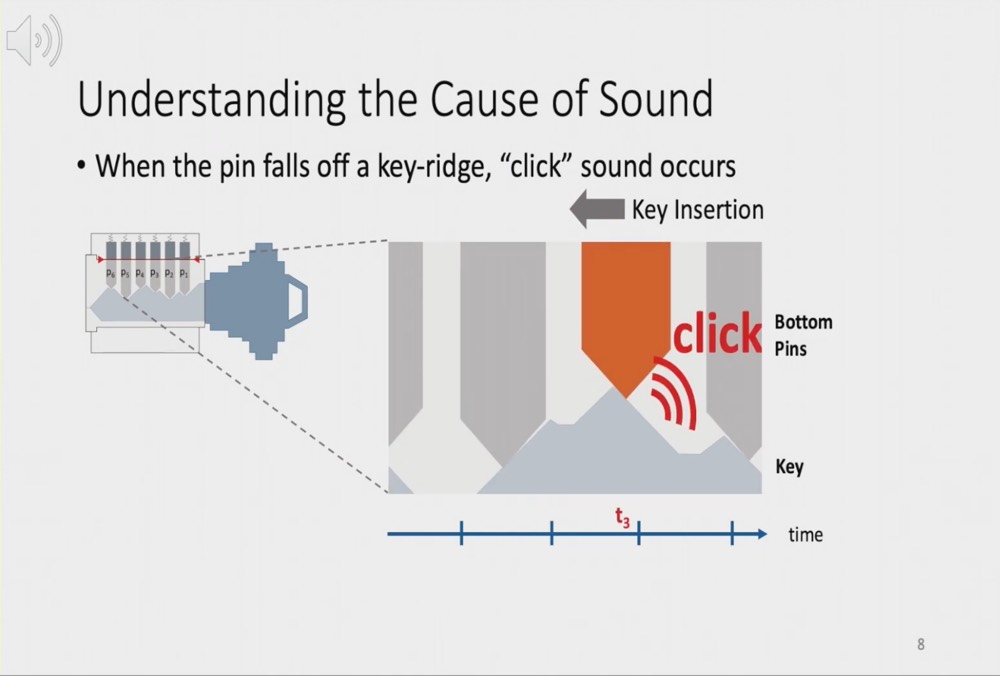
The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Descrição
The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.

The 23 Most Rare and Expensive Pokémon Cards

Vengeance Sound
Threat Tracking: Tracking Threats Across the Dark and Clear Web - Flare

Mixing Vocals: 10 Tips To Get A Radio-Ready Vocal Sound

SpiKey technique allows opening the lock by recording a turning key

A mathematical model for the interaction of anisotropic turbulence with a rigid leading edge, Journal of Fluid Mechanics

What is Peer to Peer Network, and How does it work? [UPDATED] - Blockchain Council
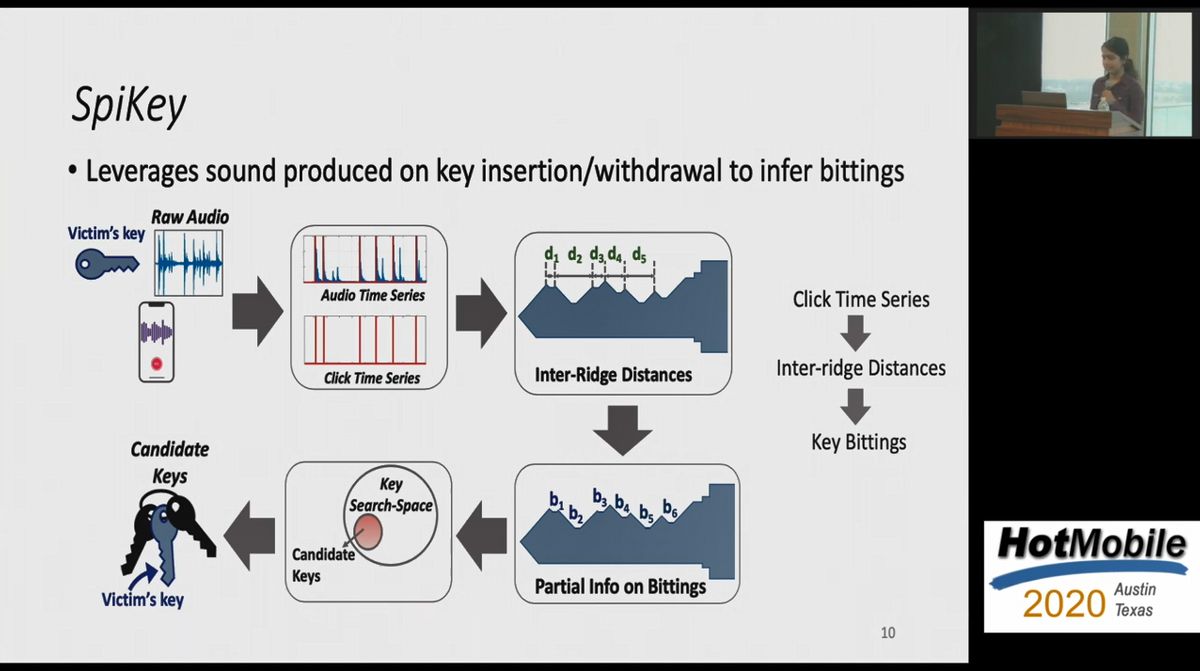
Researchers warn that there is a danger that a duplicate key will be made from 'sound when inserting a key into a keyhole' - GIGAZINE

Can the Technology Behind Covid Vaccines Cure Other Diseases? - WSJ

Trader Bets Big on Volatility Index (VIX) Spike Hours Before US Payrolls Data - Bloomberg
I made a video game with a pencil and paper
How to expedite your investigations with a DFIR - Cynet

SpiKey technique allows opening the lock by recording a turning key
Researchers Can Duplicate Keys from the Sounds They Make in Locks

Hackers can now clone your keys just by listening to them with a smartphone
de
por adulto (o preço varia de acordo com o tamanho do grupo)