How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Descrição
In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.

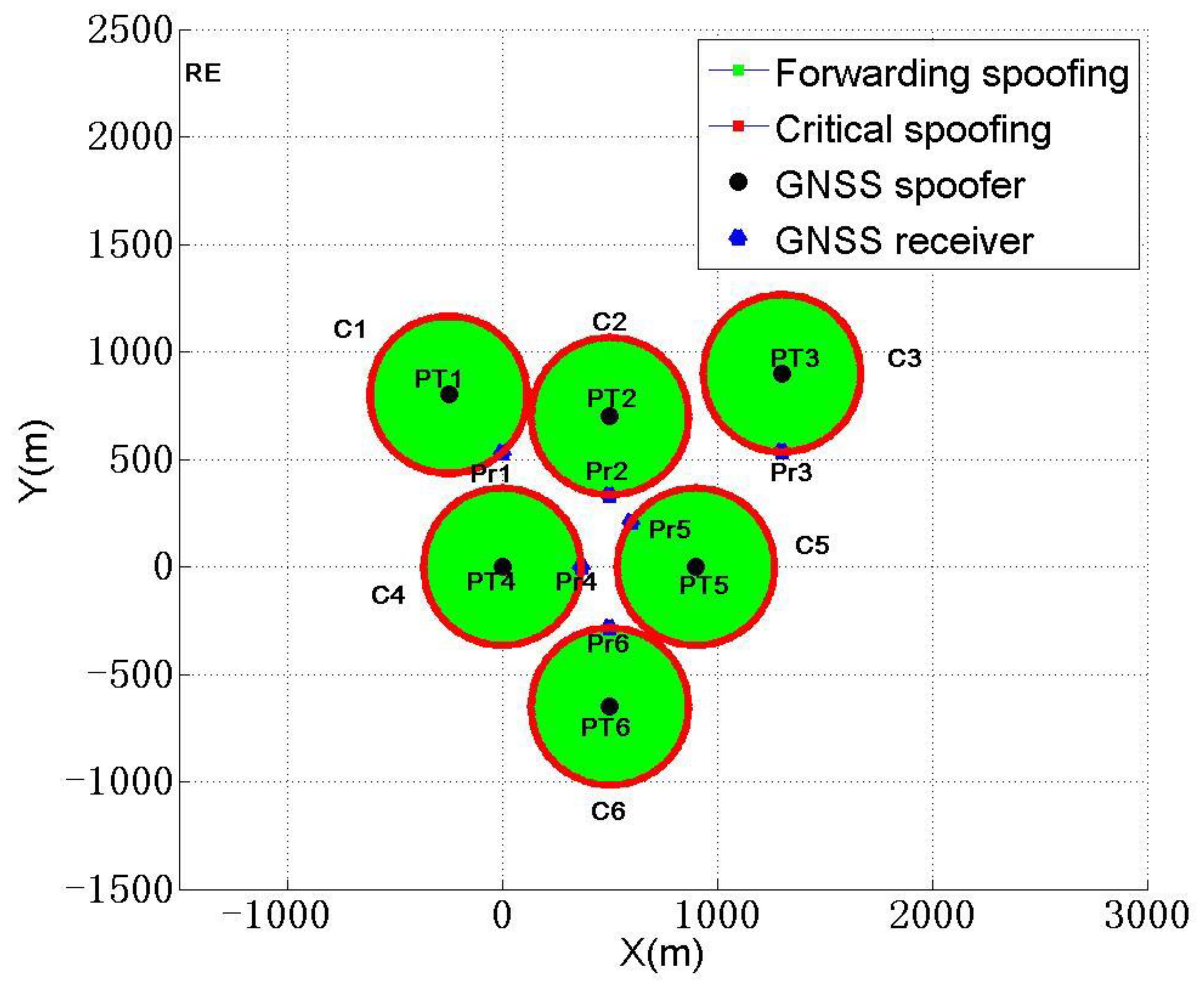
Layer 2 Attacks – MAC Address Spoofing Attacks

Configuring MAC-IP Anti-Spoof
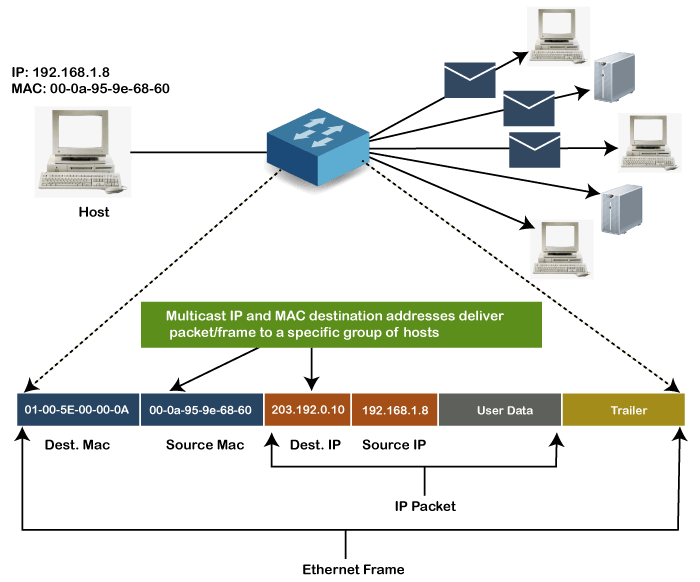
What is MAC Address? - javatpoint
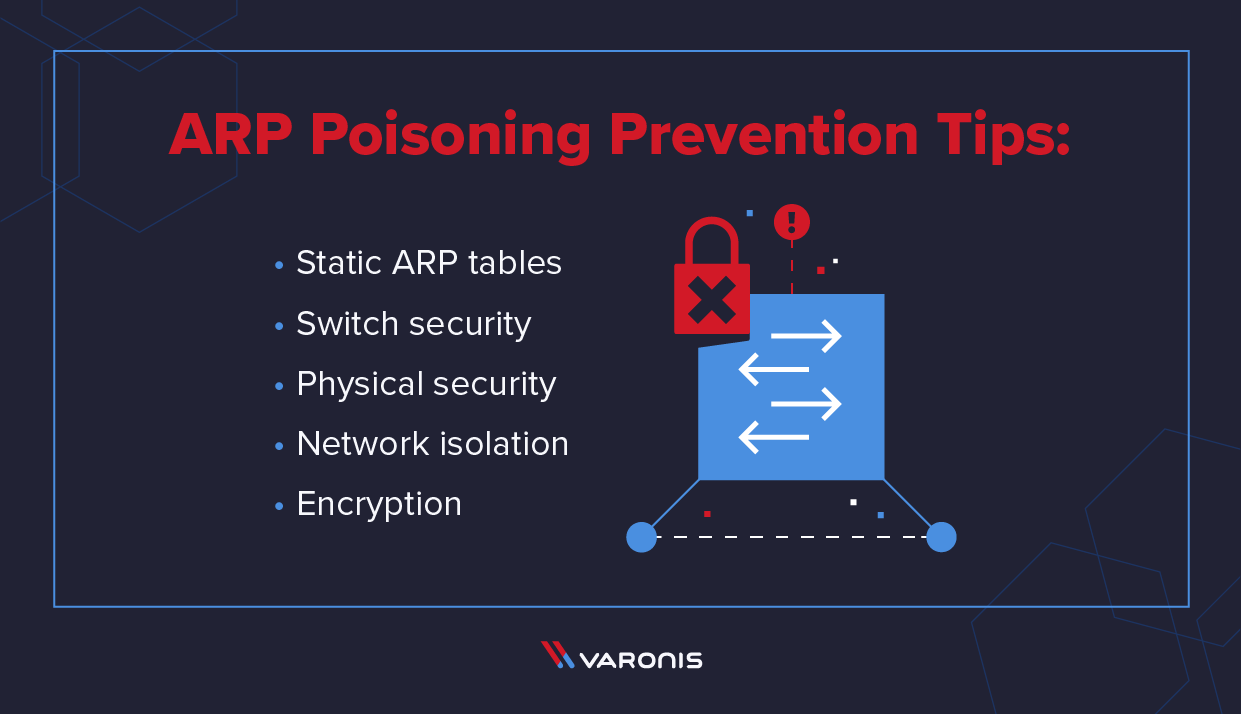
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks
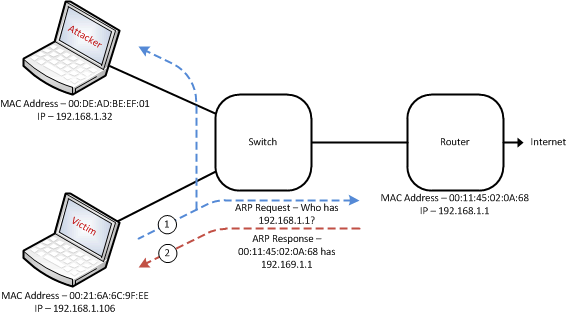
Man in the Middle (MITM) Attacks Explained: ARP Poisoining – ShortestPathFirst

What Is a MAC Spoofing Attack and How Can You Prevent It?
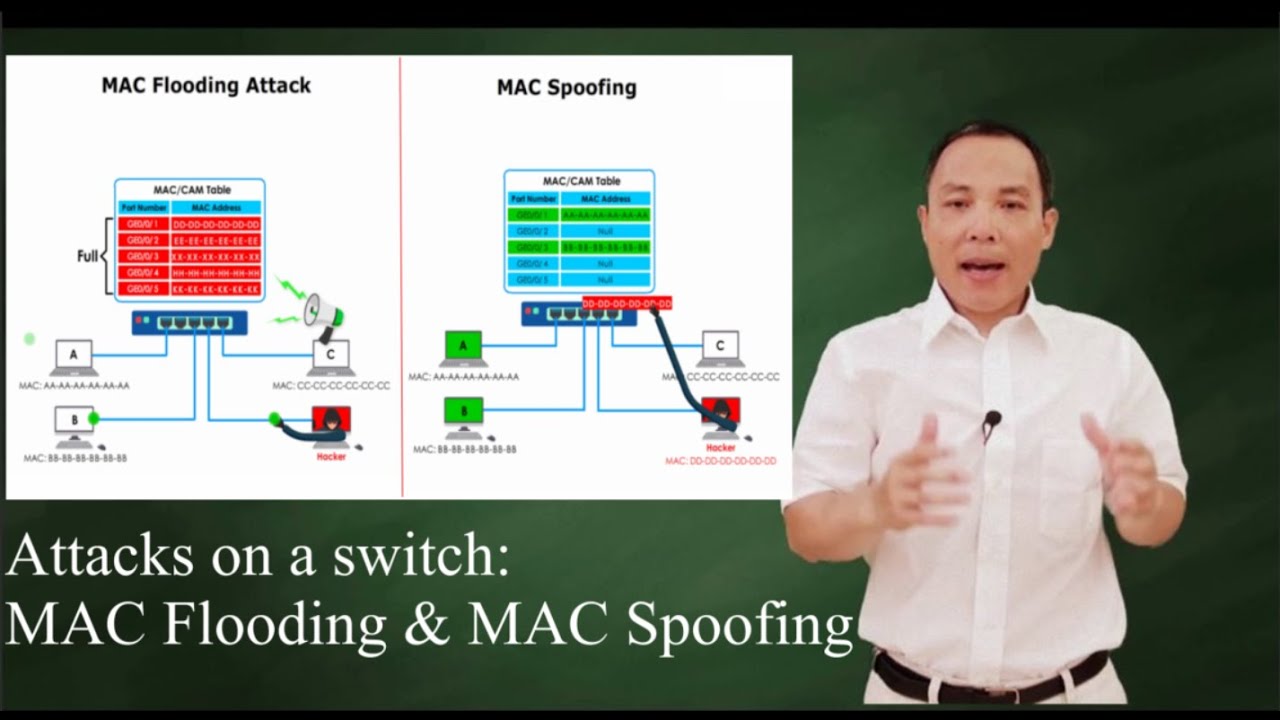
Switch attacks: MAC Flooding and MAC Spoofing

MAC Spoofing: Understanding and Preventing Unauthorized Network Access - FasterCapital

What is Spoofing Attack and How to Prevent It? - SOCRadar® Cyber Intelligence Inc.

IP address spoofing - Wikipedia

What is a MAC address, and what can it reveal about you?
de
por adulto (o preço varia de acordo com o tamanho do grupo)