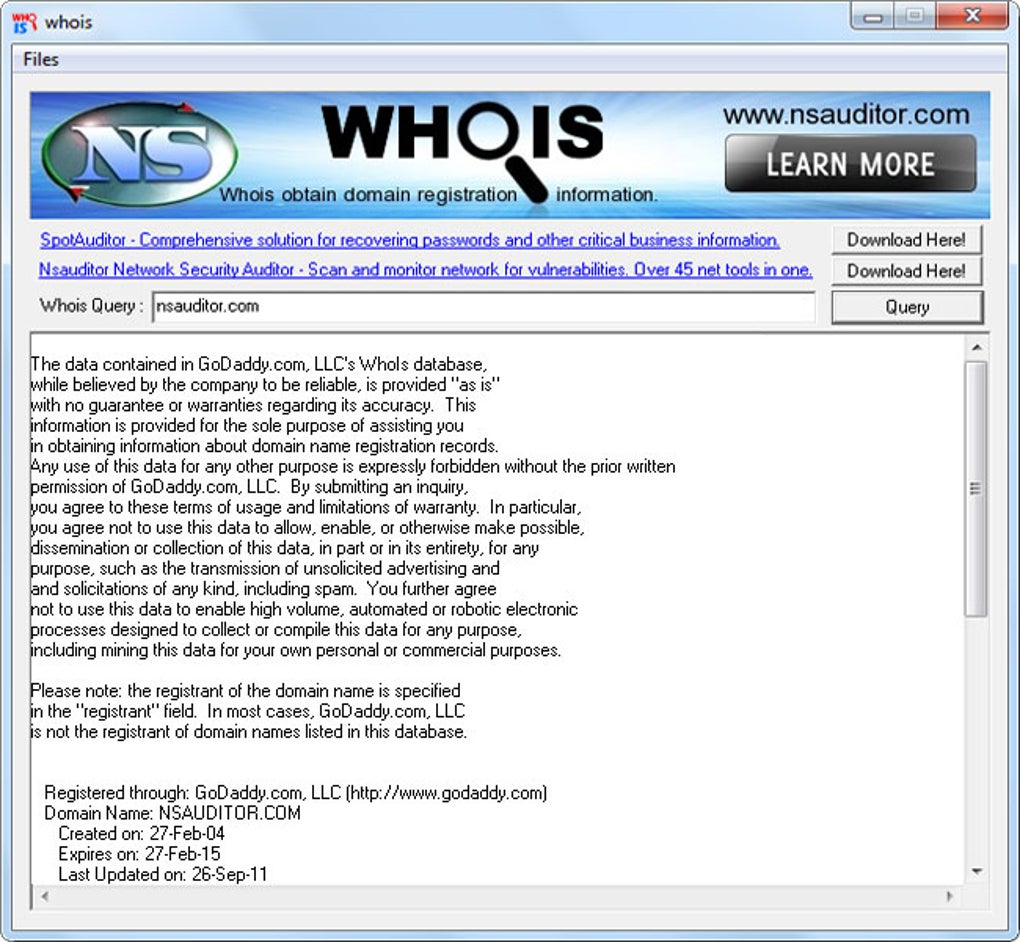
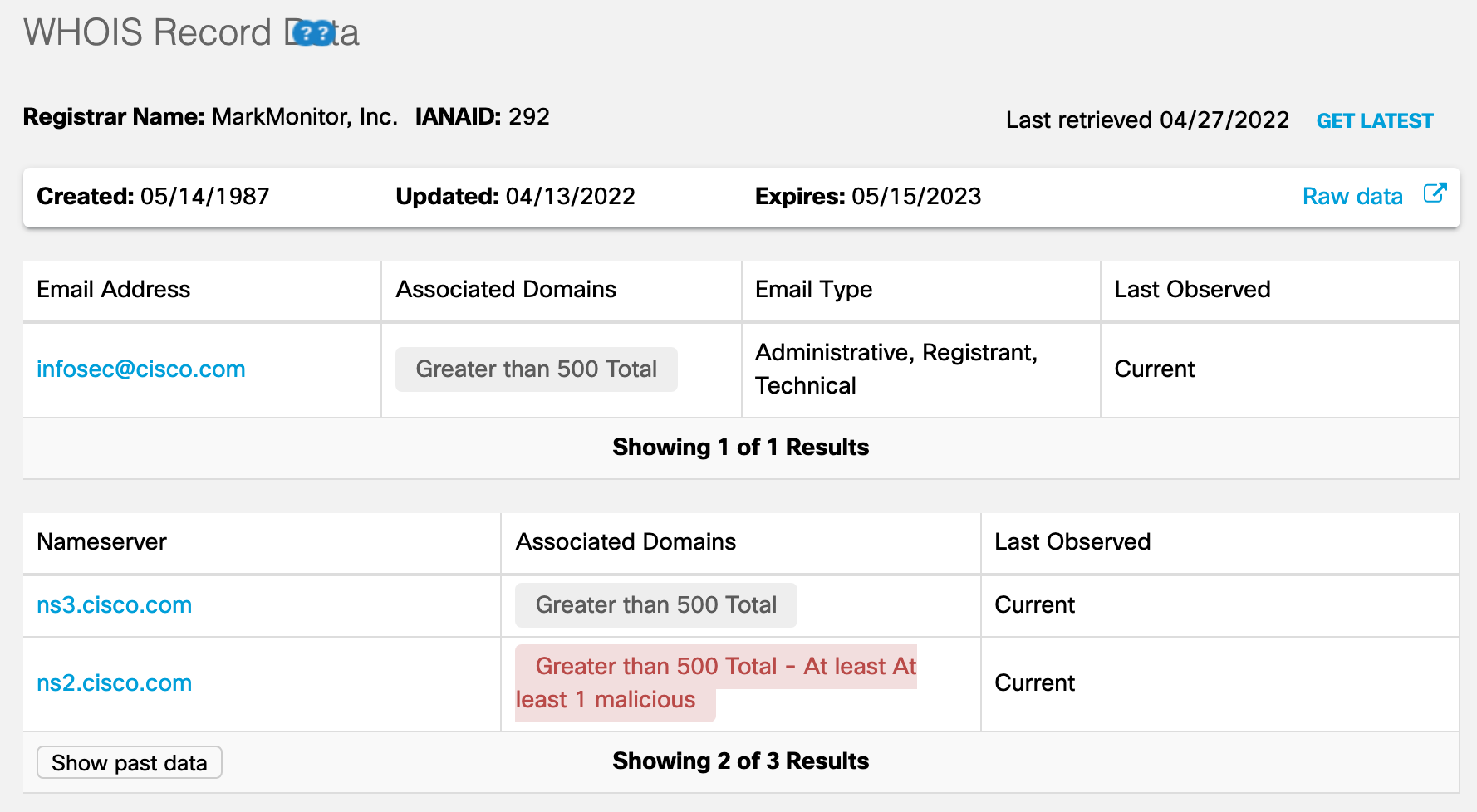
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %
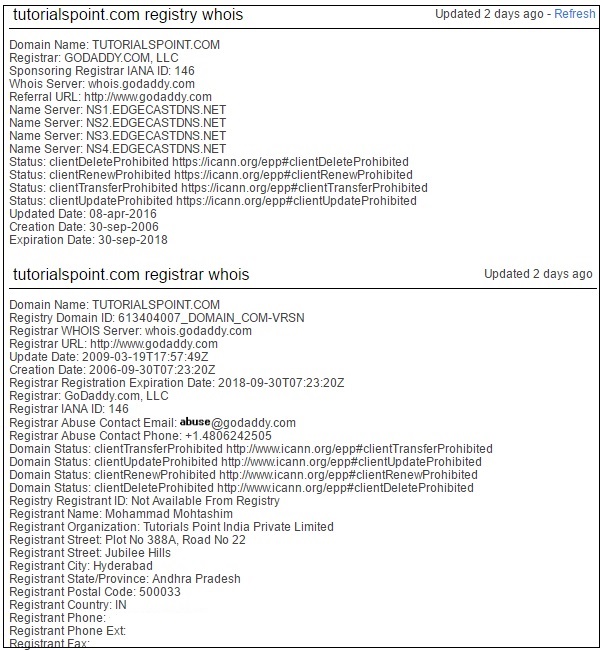
Ethical Hacking - Quick Guide

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

Tips for Investigating Cybercrime Infrastructure

Malicious Life Podcast: Wild West Hackin' Fest

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS

Tips for Investigating Cybercrime Infrastructure

Zvukový „vodoznak“ – konec pirátství?

Ethical Hacking Learning Path — A Complete Roadmap, by crawsecurity

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
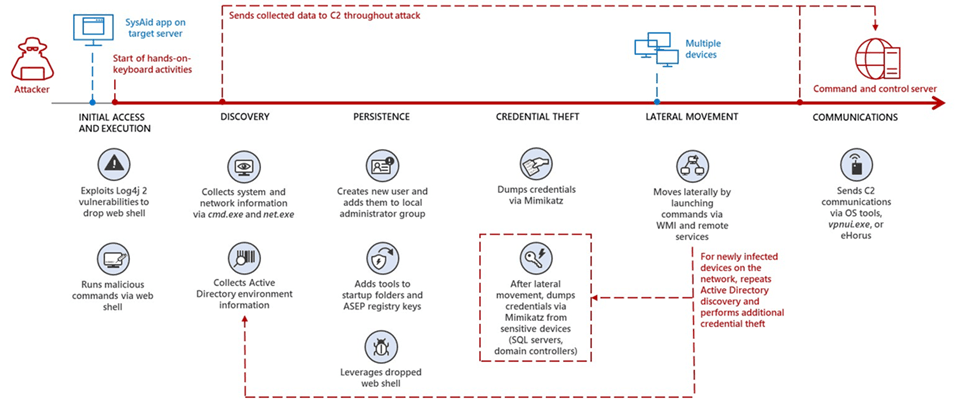
Microsoft: Nation-state Iranian hackers exploit Log4Shell against Israel

Russian APT hacked Iranian APT's infrastructure back in 2017

Hackbun
de
por adulto (o preço varia de acordo com o tamanho do grupo)