Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Descrição
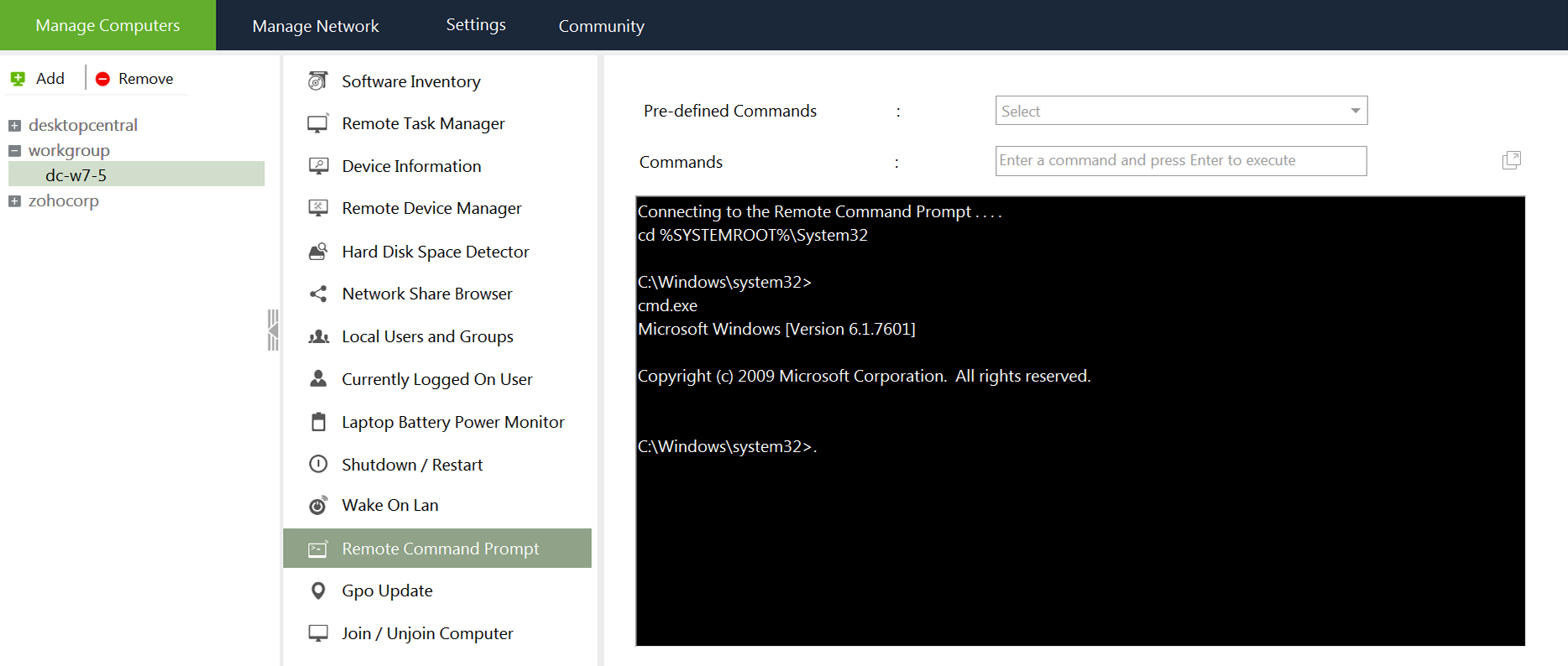
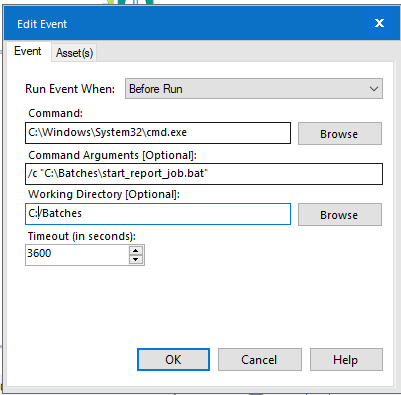
The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

T1202: Indirect Command Execution - Red Team Notes 2.0

TRY HACK ME: Living Off The Land Write-Up, by Shefali Kumari

Cyber Operations during the Russo-Ukrainian War

TryHackMe Hacktivities
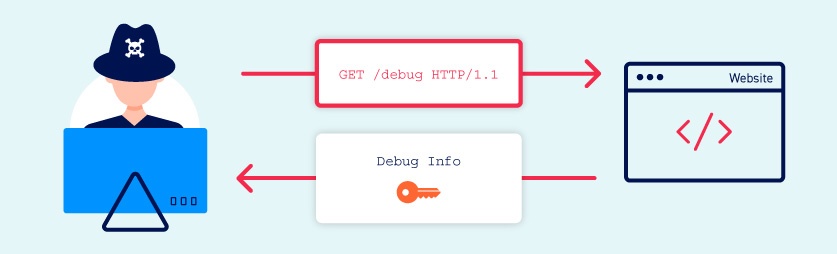
Information disclosure vulnerabilities

TryHackMe Hacktivities
Securing LLM Systems Against Prompt Injection

How prepared is the world? Identifying weaknesses in existing assessment frameworks for global health security through a One Health approach - The Lancet
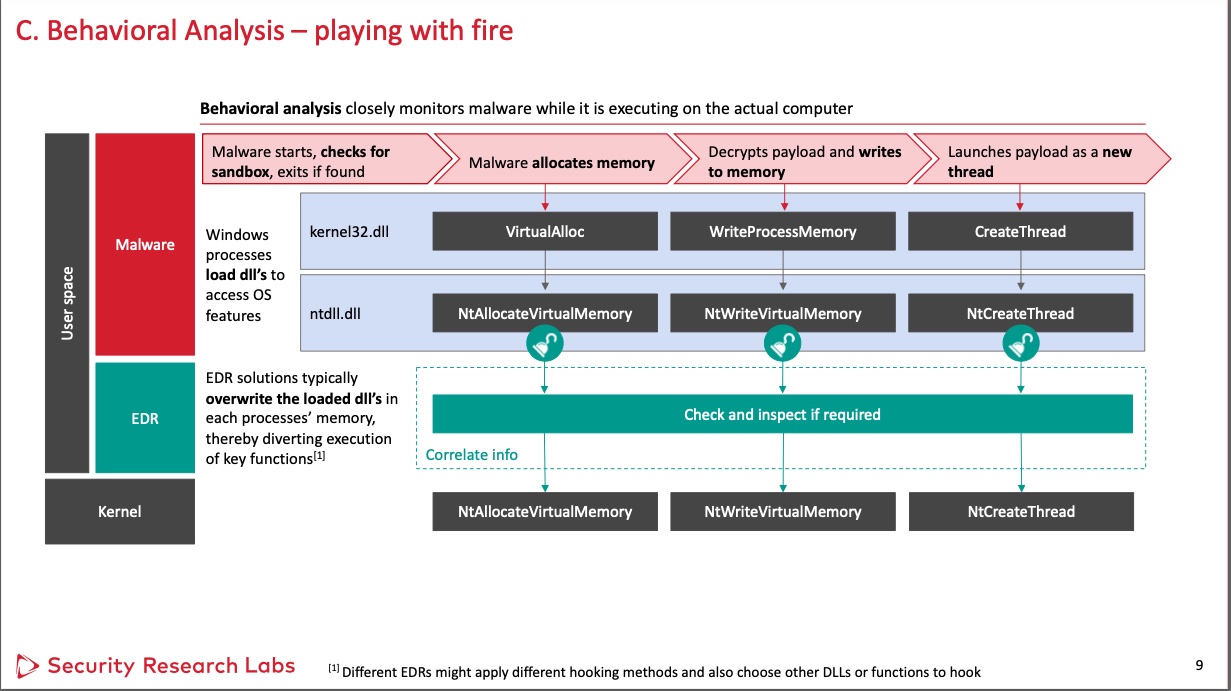
Organizations are spending billions on malware defense that's easy to bypass

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
de
por adulto (o preço varia de acordo com o tamanho do grupo)