Complete UAF exploit - UD Capture
Por um escritor misterioso
Descrição

UAF-GUARD: Defending the use-after-free exploits via fine-grained

Automated Use-After-Free Detection and Exploit Mitigation: How Far
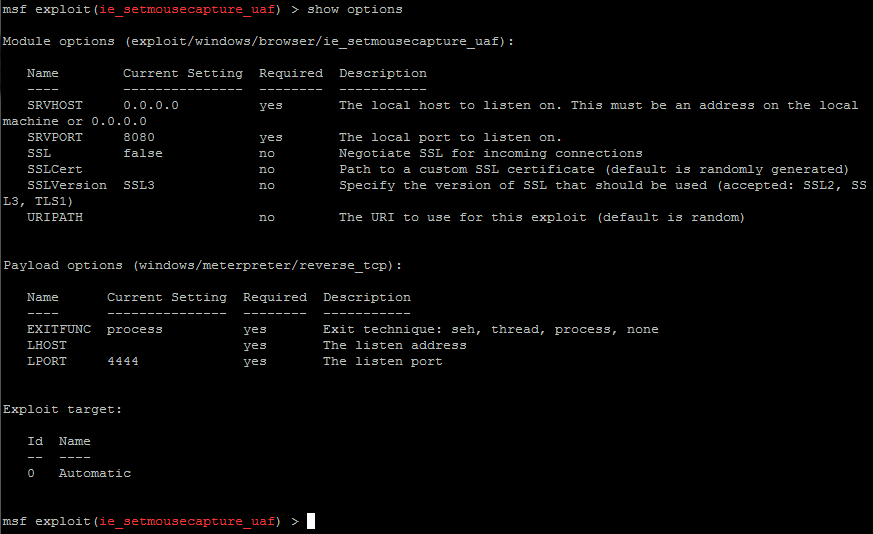
Blog for and by my students, current and future: Exploiting and
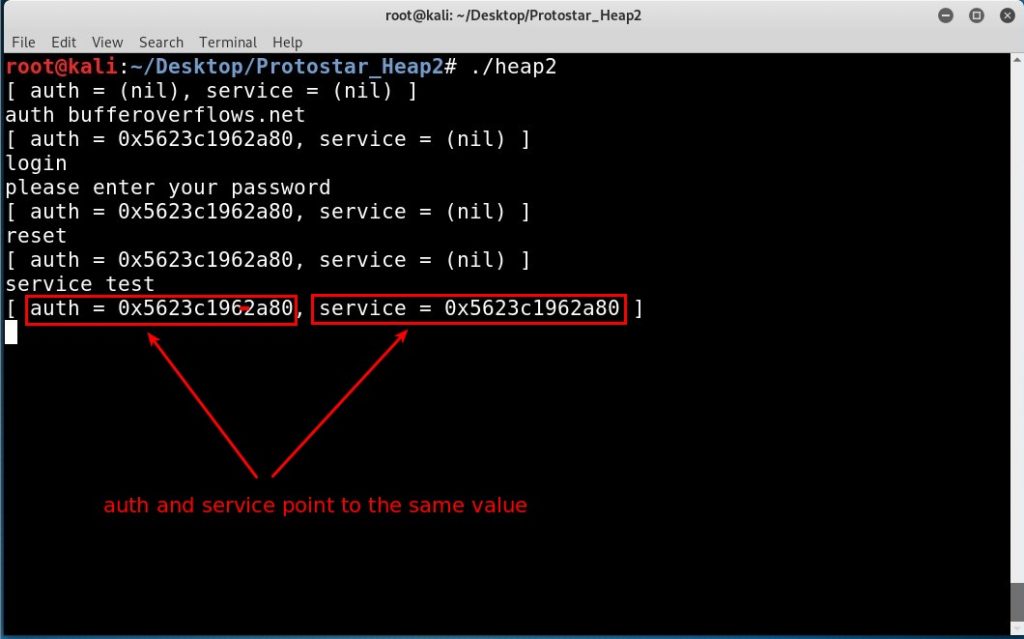
Use-After-Free Vulnerability (UAF) and Demo with Protostar Heap 2

SETTLERS OF NETLINK: Exploiting a limited UAF in nf_tables (CVE
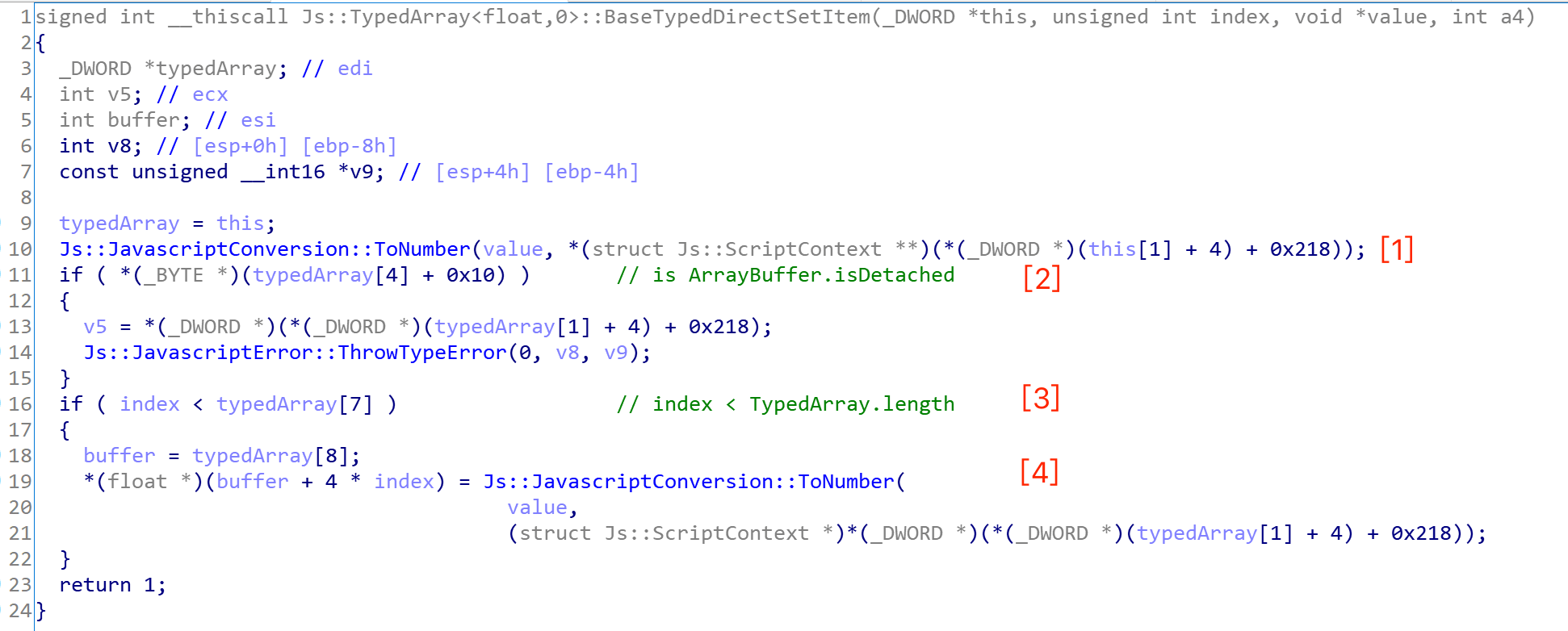
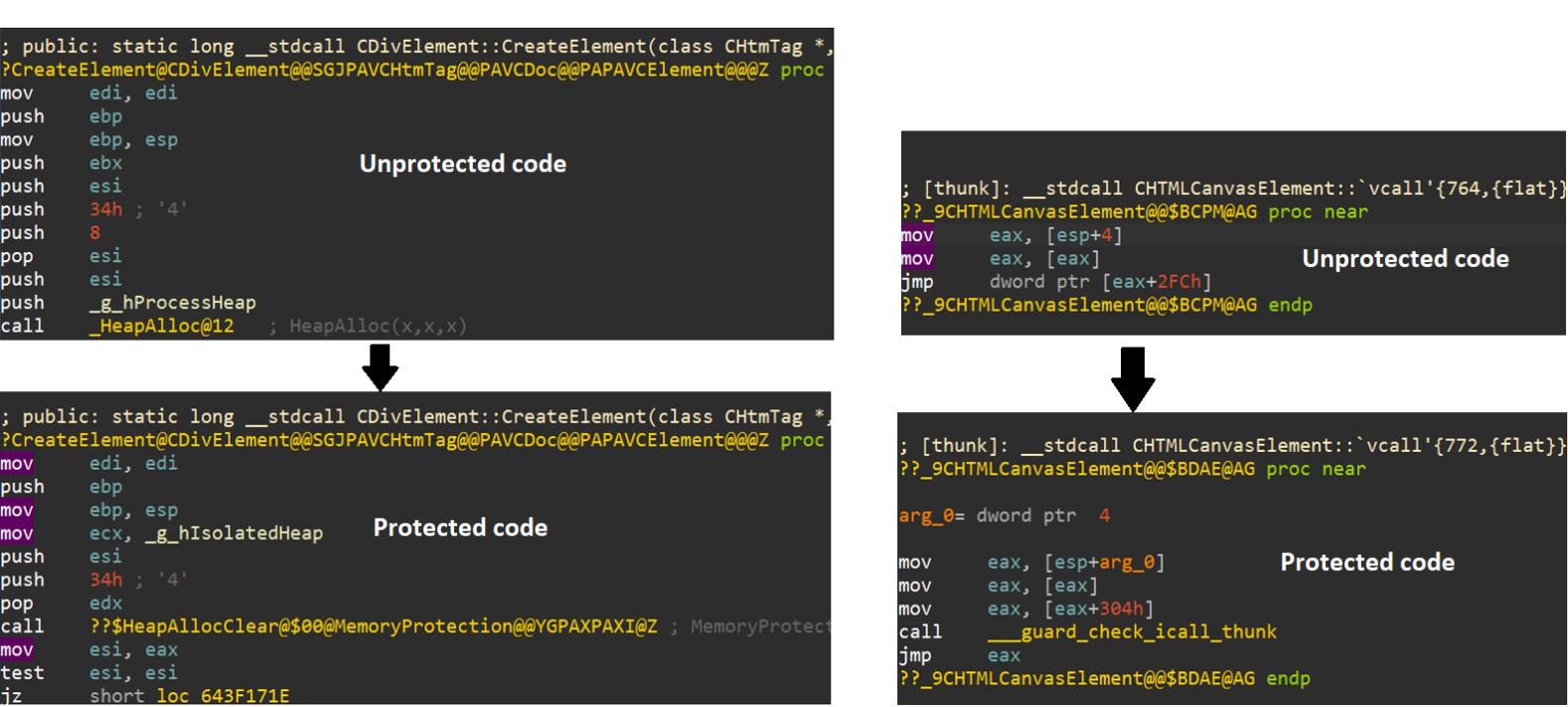
CVE-2020-17053: Use-After-Free IE Vulnerability
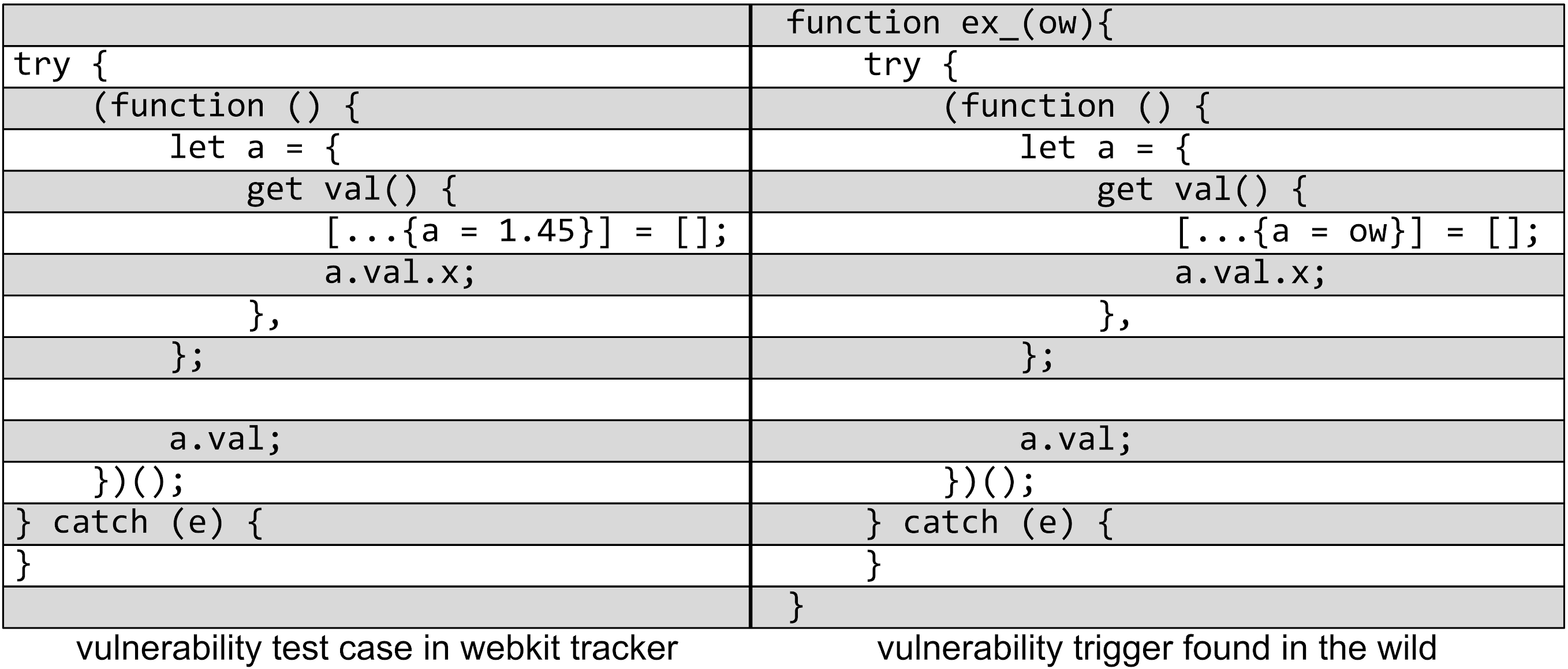
Project Zero: JSC Exploits

Heap Exploit Development

Exploiting a Use-After-Free (UAF) Vulnerability - Unsubscriptions
Beyond Memory Corruption Vulnerabilities – A Security Extinction
de
por adulto (o preço varia de acordo com o tamanho do grupo)



:extract_cover():upscale()/2014/11/10/742/n/1922283/1cd2ac05e0beb9f8_thumb_temp_cover_file23875021415637889.jpg)


