CSP and Bypasses
Por um escritor misterioso
Descrição
This blog post aims to demonstrate what CSP is and why CSP is implemented. And how attackers can bypass CSP. In this article, I will include how you can bypass some directives to achieve XSS on the target application.
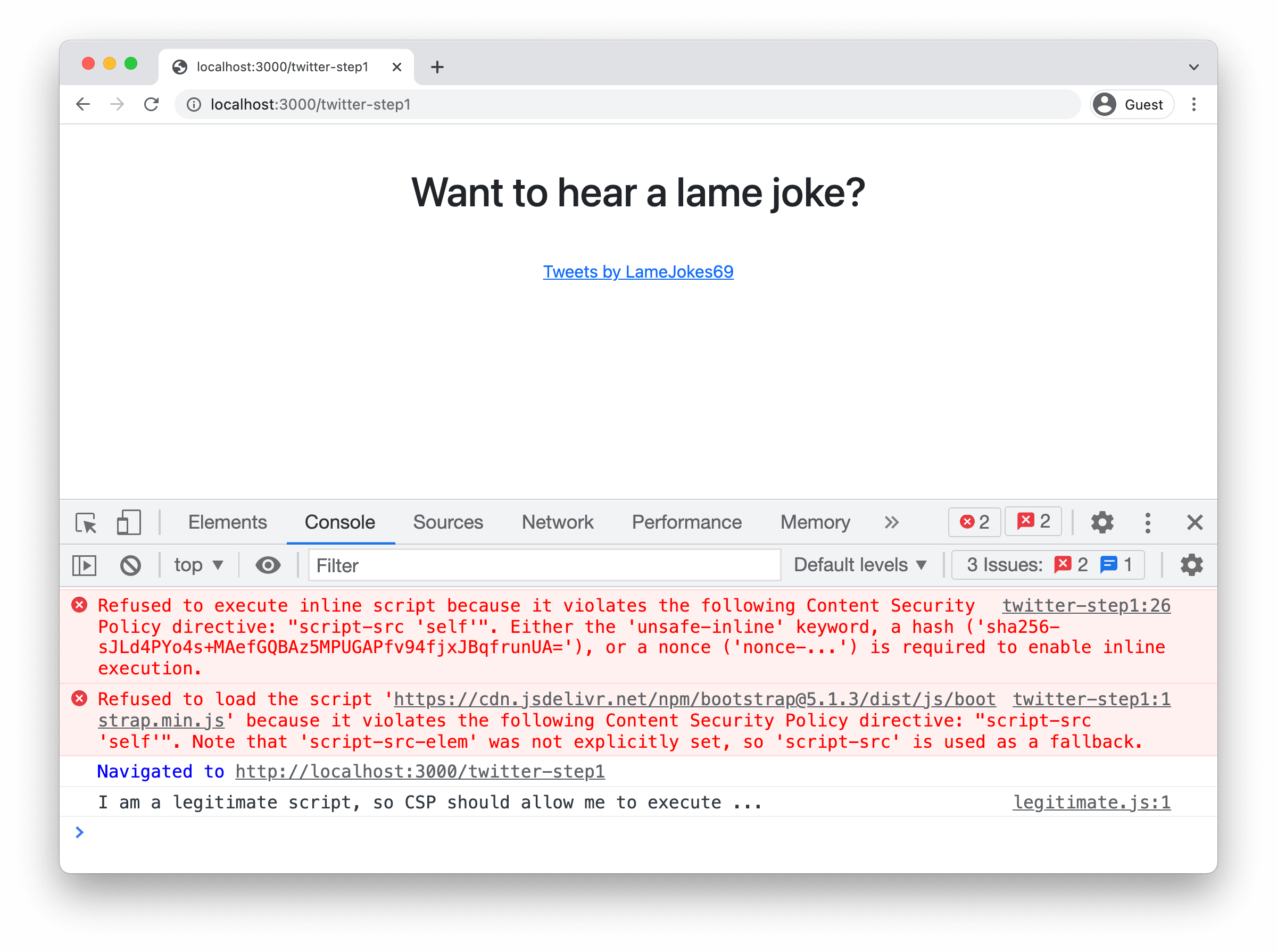
Defending against XSS with CSP
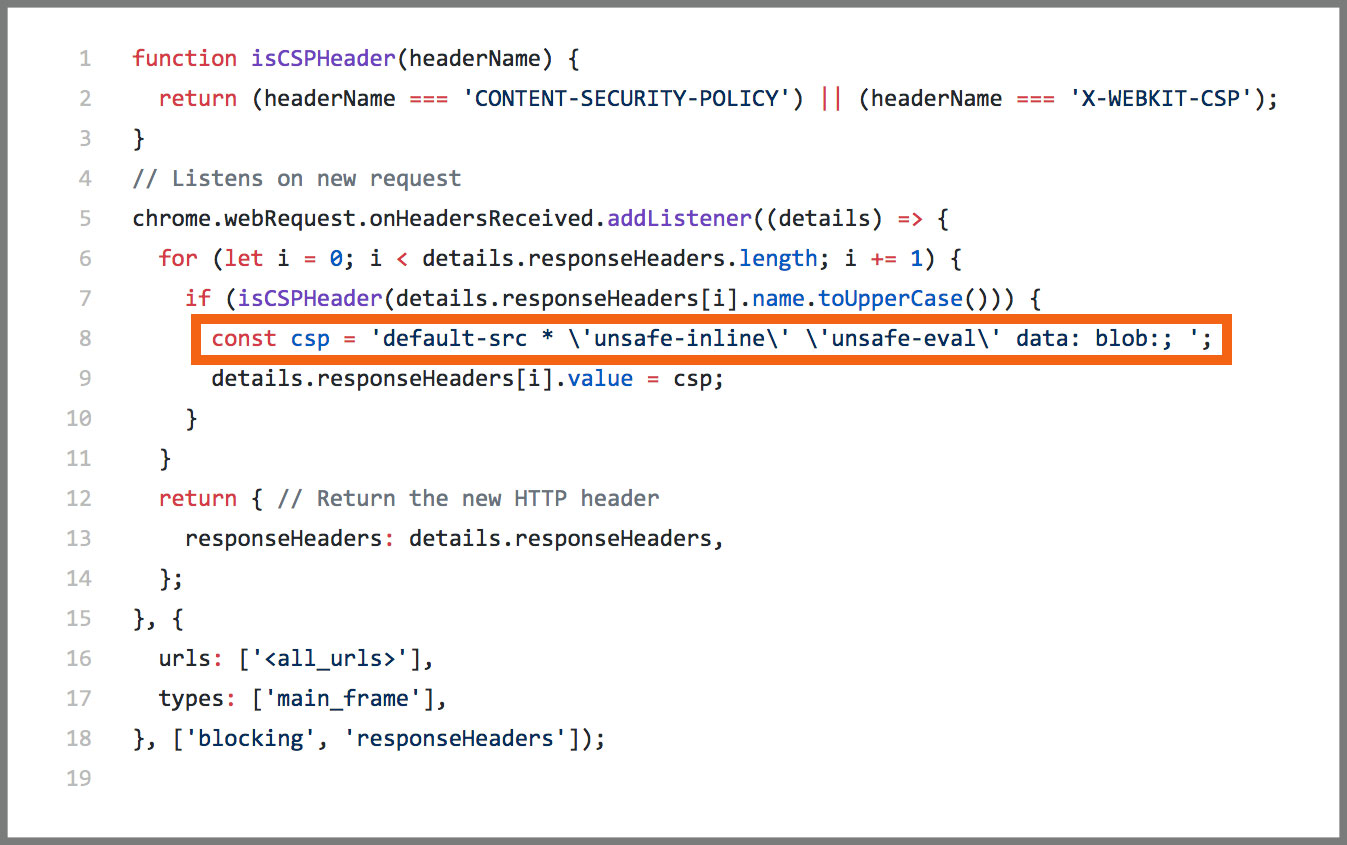
How Browser Extensions Routinely Bypass a CSP

Learn & bypass Content Security Policy HTTP Response Header - Requestly

leveraging the SQL Injection to Execute the XSS by Evading CSP

Content Security Policy (CSP) Bypass - HackTricks - Boitatech
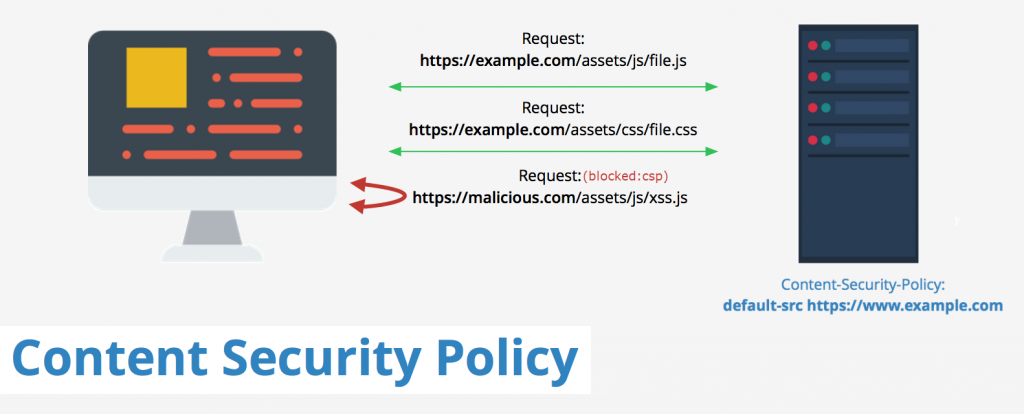
Content Security Policy Bypass - Deteact - continuous information security services
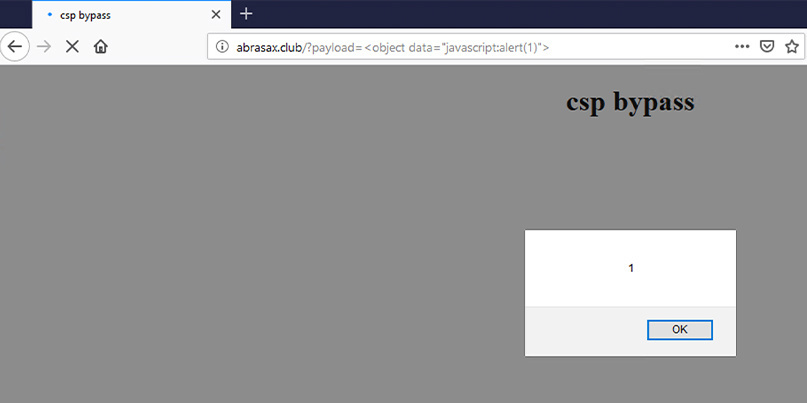
Firefox vulnerable to trivial CSP bypass
Content Security Policy Bypass - Deteact - continuous information security services

Hunting nonce-based CSP bypasses with dynamic analysis

Bypassing CSP with JSONP Endpoints - Hurricane Labs

Content Security Policy Can be bypassed in Chrome?

Using Content Security Policy (CSP) to Secure Web Applications
de
por adulto (o preço varia de acordo com o tamanho do grupo)