Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Descrição

10 Steps to Automate Container Security Into the CI/CD Pipeline

What is CI/CD, and How to Integrate Security? - GuardRails

CI / CD Pipeline Integrations
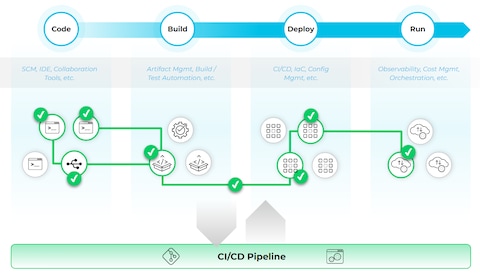
What Is CI/CD Security? - Palo Alto Networks

Vulnerability Scanning in your CI/CD Pipeline - Part Two

8 tips for securing your CI/CD pipeline with Snyk
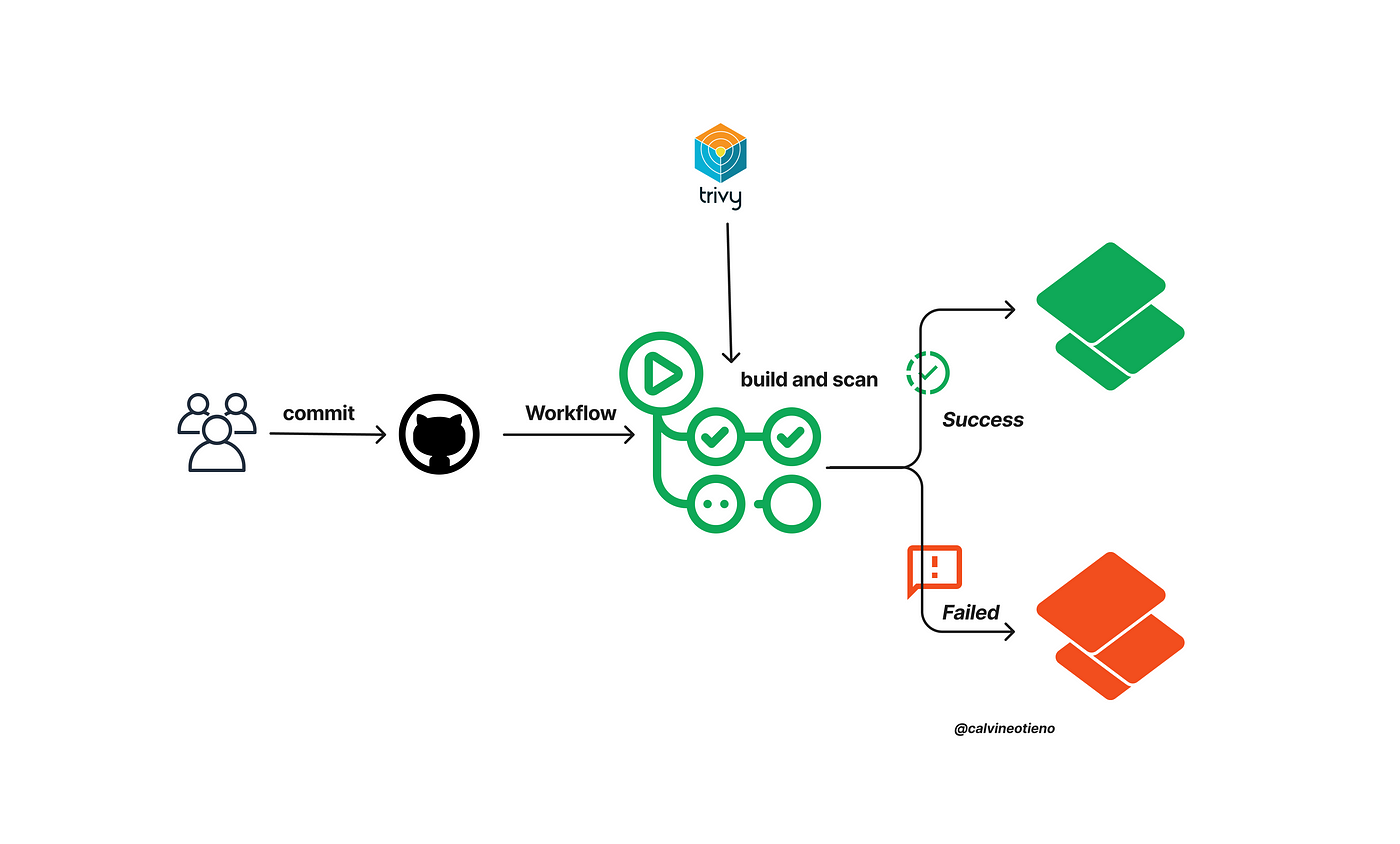
Improving your CI/CD Pipeline: Helm Charts Security Scanning with Trivy and GitHub Actions, by Calvine Otieno
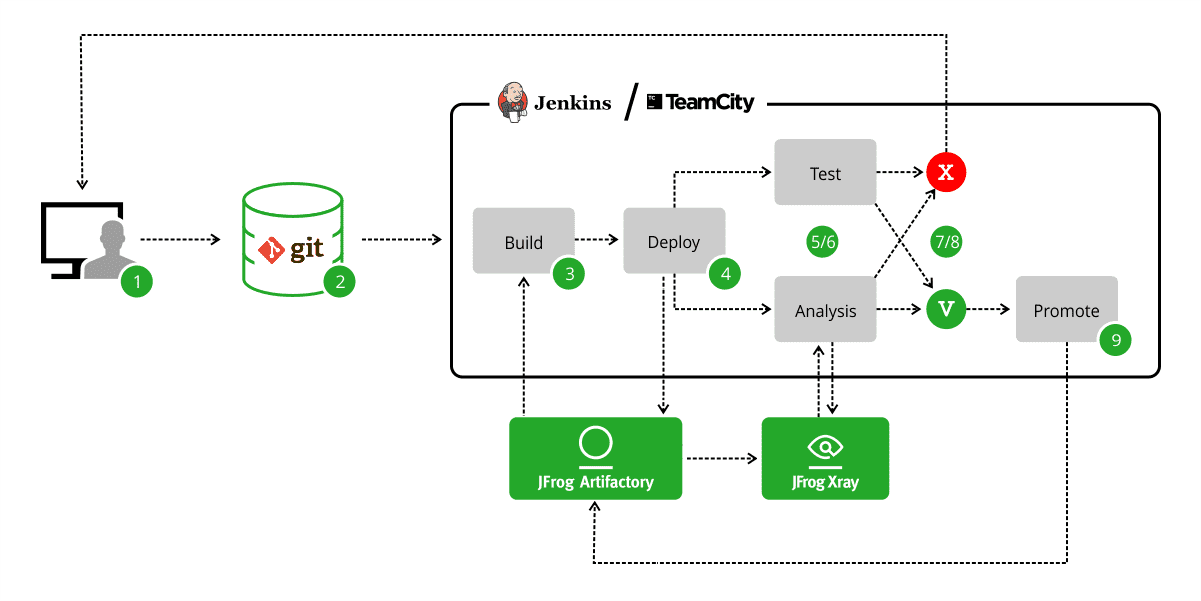
Security vulnerability detection scan for CI/CD pipeline with JFrog Xray
DevSecOps in AWS using different security tools Part-I, by Rakesh Chatla
de
por adulto (o preço varia de acordo com o tamanho do grupo)