Anti-Coinminer Mining Campaign
Por um escritor misterioso
Descrição
The Zscaler Research team shared their analysis about a malware operator that is using scareware tactics to give a false sense of security to the end user while exploiting their machine for financial gains. The Malware author, embedded a backdoor code, to steal CPU cycles from infected system to mine coins for author.
Can You Hear The Digging? The Dangers of Mobile Mining - Check Point Blog

Cryptocurrency mining operations target Windows Server, Redis and Apache Solr servers online

Cryptocurrency miners infected more than 50% of the European airport workstations - Cyber Defense Magazine
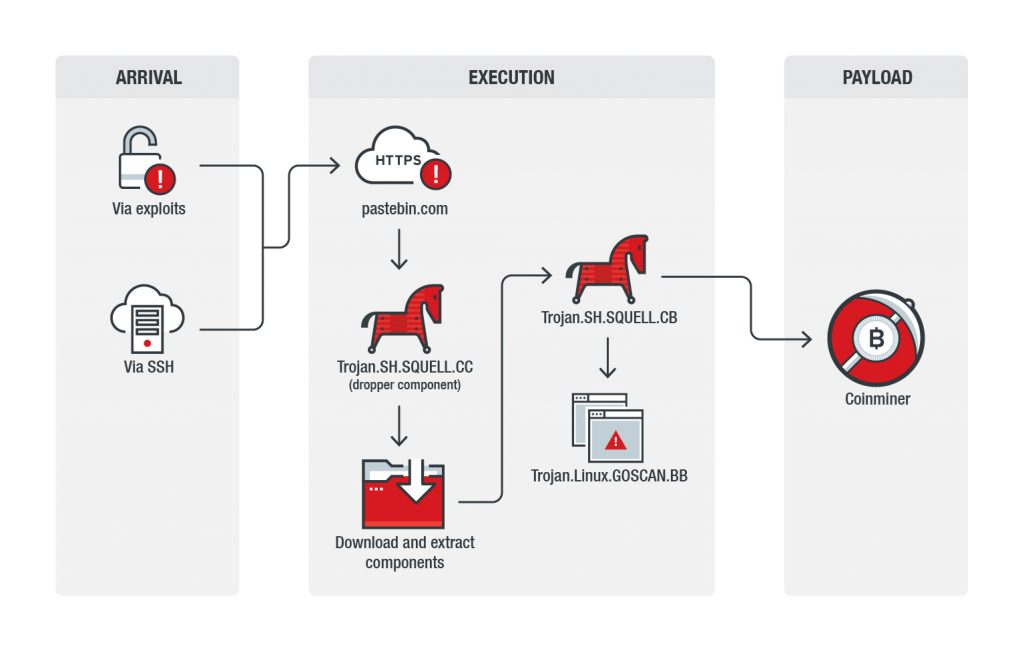
Golang-based Spreader Used in a Cryptocurrency-Mining Malware Campaign - Malware Analysis - Malware Analysis, News and Indicators
What is Coin Miner?, CoinMiner Malware

Uncovering illegitimate Crypto-Mining Activity (Cryptojacking) in the Enterprise: Utilizing Network Logs for Investigation and Remediation

Hunting down Dofoil with Windows Defender ATP
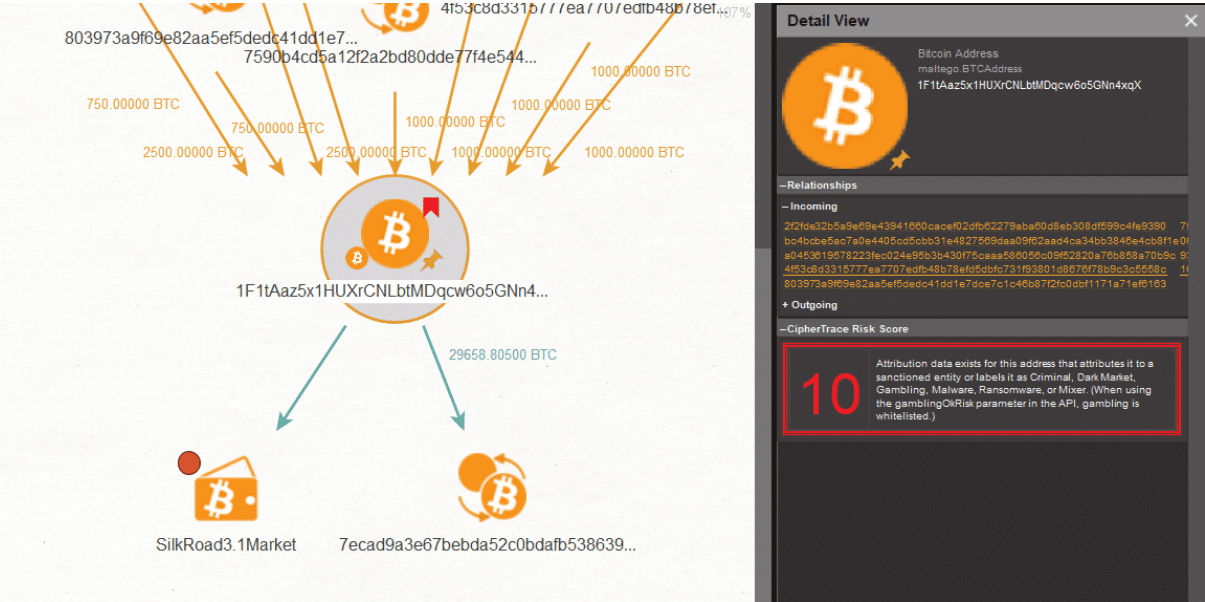
Into the Cryptoverse - The Intersection of Cryptocurrency and Cybersecurity - Cynet

Sophos - NEW from SophosLabs: Two flavors of Tor2Mine miner dig deep into networks with PowerShell, VBScript ⚒️ Using remote scripts and code, one variant can even execute filelessly until it gains

Swedish Windows Security User Group » cryptocurrency mining

CoinMiners are Evasive - BsidesTLV
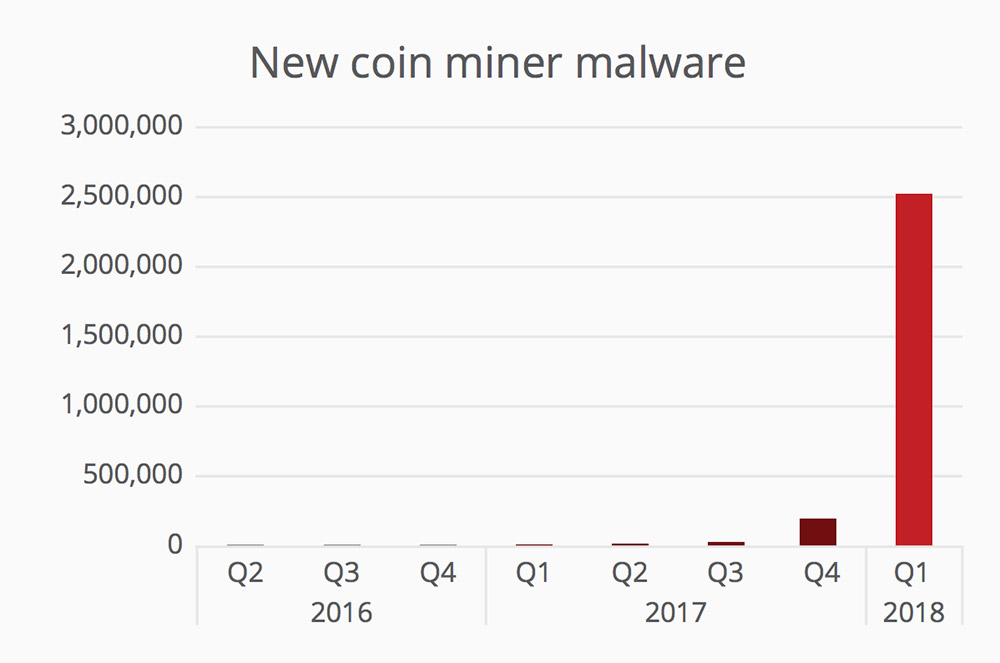
Cryptojacking Displaces Ransomware as Top Malware Threat
de
por adulto (o preço varia de acordo com o tamanho do grupo)