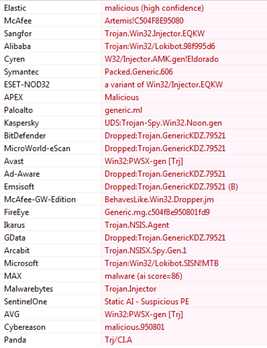
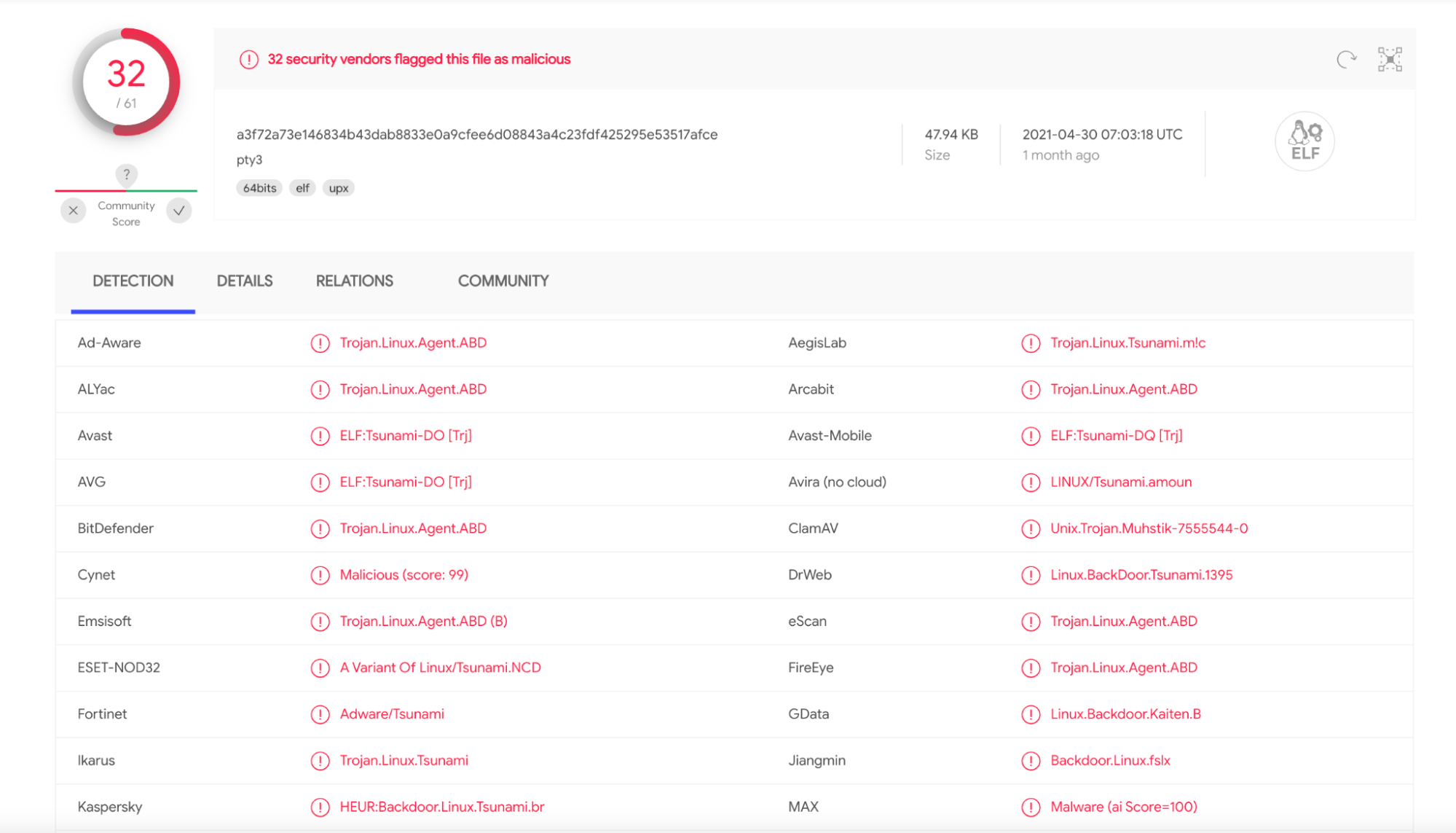
PDF] Analysing web-based malware behaviour through client honeypots
Por um escritor misterioso
Descrição
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/18-Figure1-1-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.ntt-review.jp/archive_html/201210/images/fa2_fig04.jpg)
Detection, Analysis, and Countermeasure Technologies for Cyber Attacks from Evolving Malware
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/65-Figure4-2-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://0.academia-photos.com/attachment_thumbnails/98730676/mini_magick20230216-1-1dasecv.png?1676525923)
PDF) Honeypot: A Way to Capture Attackers
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.ntt-review.jp/archive_html/201509/images/fr1_fig01.jpg)
Recognizing the Importance of Dissemination Skills after 10 Years of Combating Malware
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/35-Table2-1-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/39-Figure2-7-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://0.academia-photos.com/attachment_thumbnails/80517577/mini_magick20220209-19651-qadq0y.png?1644400593)
PDF) Analysis of Client Honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://i1.rgstatic.net/publication/271503033_Hybrid_honeypot_framework_for_malware_collection_and_analysis/links/634806e42752e45ef6b495a7/largepreview.png)
PDF) Hybrid honeypot framework for malware collection and analysis
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.mdpi.com/futureinternet/futureinternet-15-00127/article_deploy/html/images/futureinternet-15-00127-g005-550.jpg)
Future Internet, Free Full-Text
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.webtitan.com/wp-content/uploads/2022/09/WebTitan_Cloud_UI_-_Security_Reports.png)
Web Filtering Blog
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.apriorit.com/wp-content/uploads/2018/09/Honeypot.png)
Honeypots as a Method of Malware Detection
![PDF] Analysing web-based malware behaviour through client honeypots](https://ars.els-cdn.com/content/image/1-s2.0-S1319157821003621-gr4.jpg)
Tools and Techniques for Collection and Analysis of Internet-of-Things malware: A systematic state-of-art review - ScienceDirect
![PDF] Analysing web-based malware behaviour through client honeypots](https://www.cse.wustl.edu/~jain/cse571-09/ftp/honey/fig7.gif)
A Practical Guide to Honeypots
![PDF] Analysing web-based malware behaviour through client honeypots](https://d3i71xaburhd42.cloudfront.net/16a19e59aa8694dbc45be22e6dc3b2ca47b8fc85/30-Figure2-2-1.png)
PDF] Analysing web-based malware behaviour through client honeypots
de
por adulto (o preço varia de acordo com o tamanho do grupo)