Conceal Threat Alert: Phishing Attack Bypasses Traditional Controls, ConcealBrowse to the Rescue
Por um escritor misterioso
Descrição
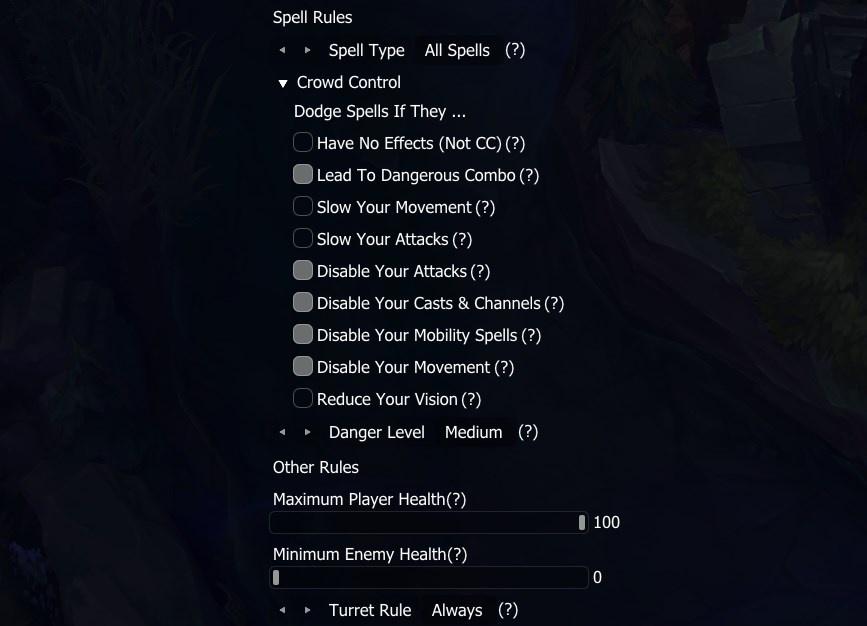
Attackers continue to innovate in their efforts to bypass traditional security controls and deliver credential theft links to unsuspecting users. In an environment rich with information about how security controls work and what entices users to click, there is a distinct need for improved protection in the browser.

Conceal - AI-Powered Browser Security - Get Started Now

Conceal - AI-Powered Browser Security - Get Started Now

Federal Government Industry Cybersecurity Solution

What is Trap Phishing?

Field Test: HTC Concealment Low Profile System
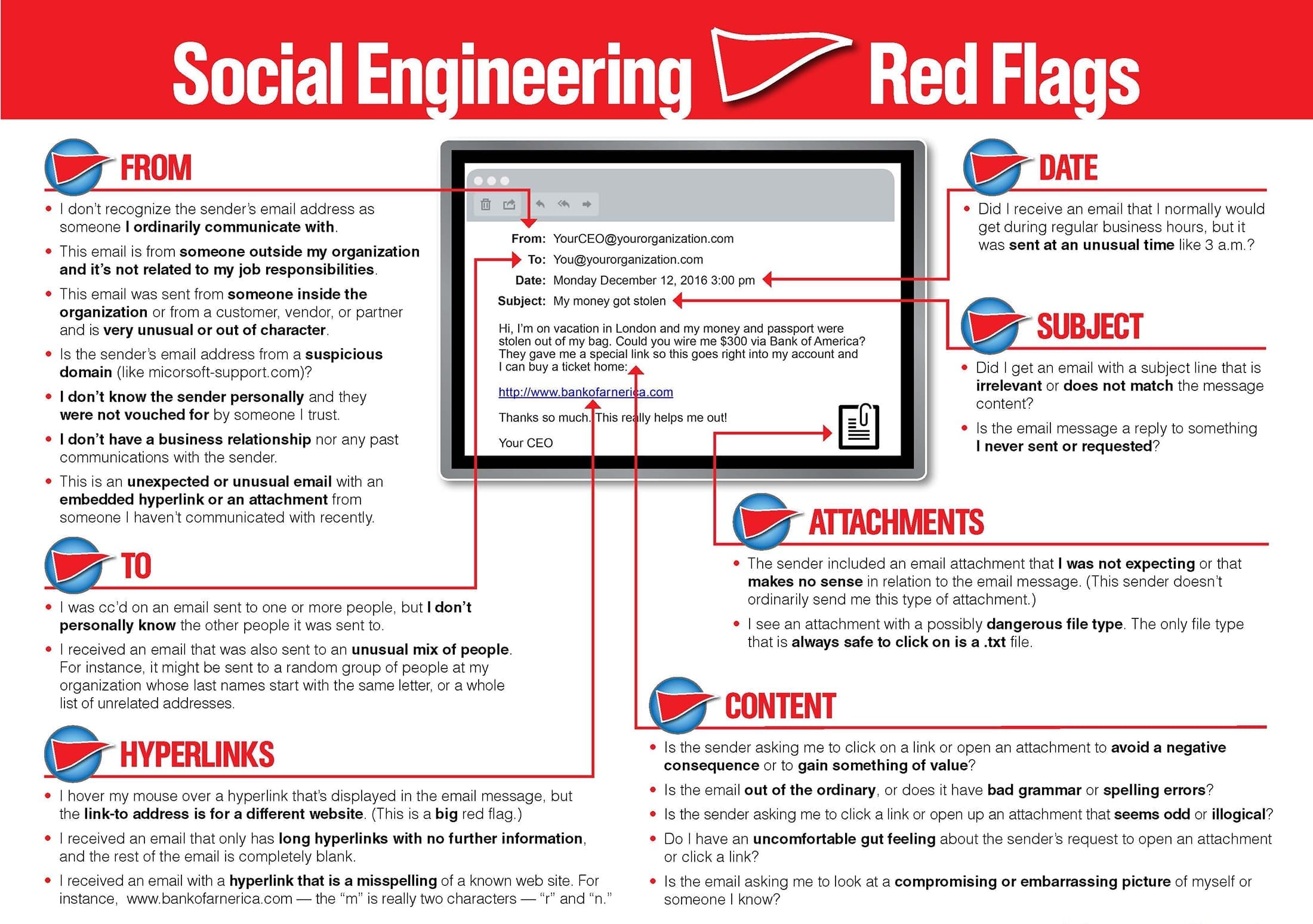
Beware of Phishing Scams - Tech Networks of BostonTech Networks of

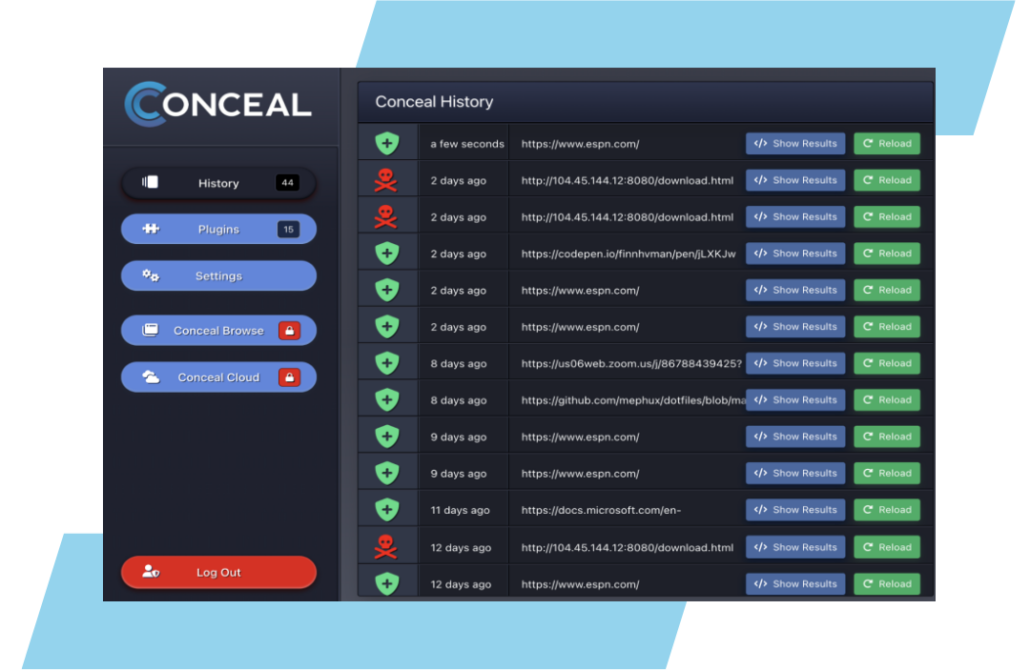
The Final Barrier to Stop the Phishing Attacks
Conceal - AI-Powered Browser Security - Get Started Now
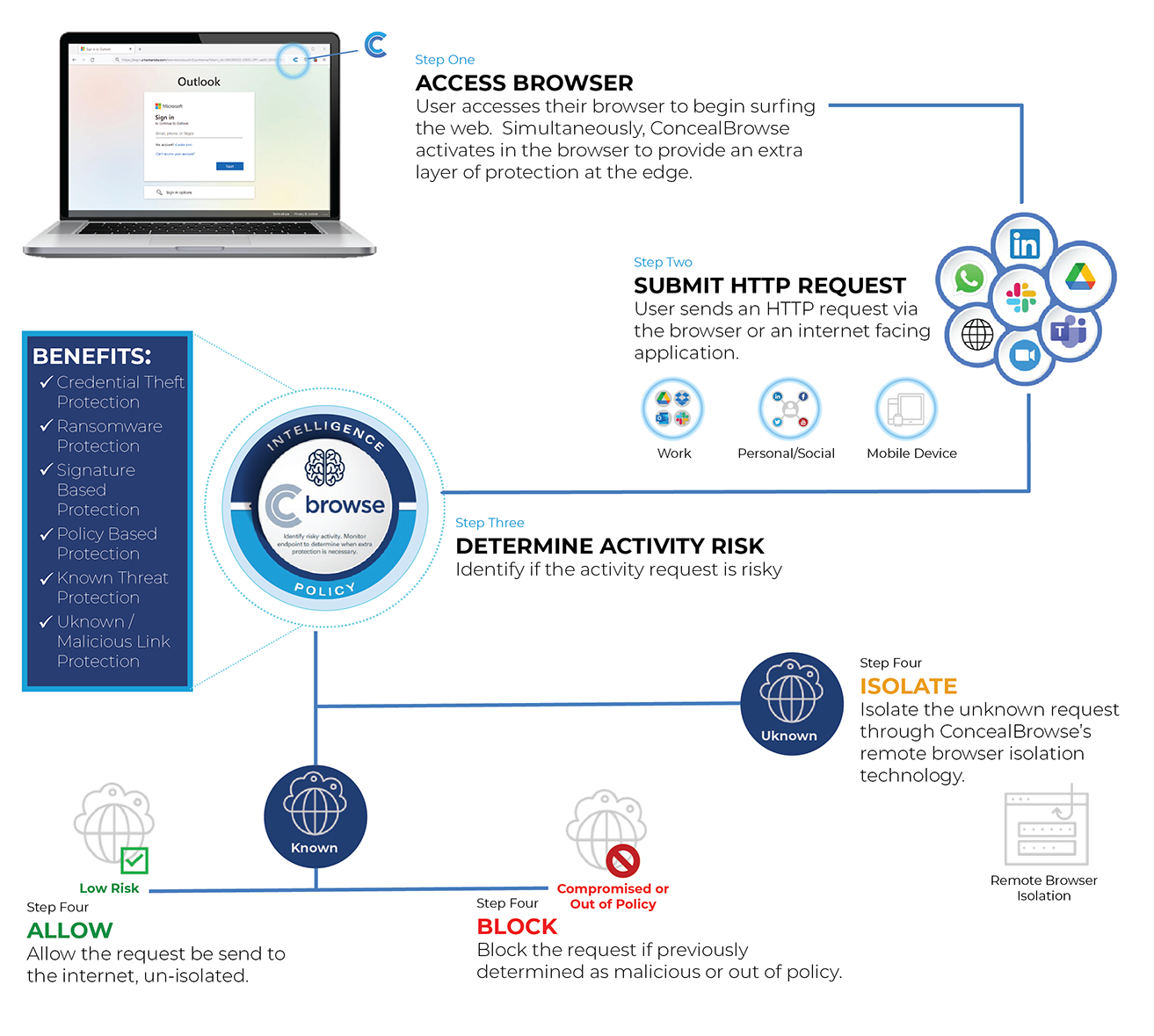
Conceal Brigantia
How to Prevent Callback Phishing Attacks on Your Organization

Legitimate SaaS Platforms Being Used to Host Phishing Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)