Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Descrição
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.

GitHub - mikeroyal/Apple-Silicon-Guide: Apple Silicon Guide. Learn all about the A17 Pro, A16 Bionic, R1, M1-series, M2-series, and M3-series chips. Along with all the Devices, Operating Systems, Tools, Gaming, and Software that

Writing Exploits for Win32 Systems from Scratch, NCC Group Research Blog

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend

Advanced Apple Debugging & Reverse Engineering, Chapter 4: Stopping in Code

iPhone Rootkit? There's an App for that! - Reverse Engineering Mac

Advanced Apple Debugging & Reverse Engineering, Chapter 31: DTrace vs. objc_msgSend
Used Book in Good Condition Highlight, take notes, and search in the book

Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation
Using the Firefox Profiler for web performance analysis - TIB AV-Portal
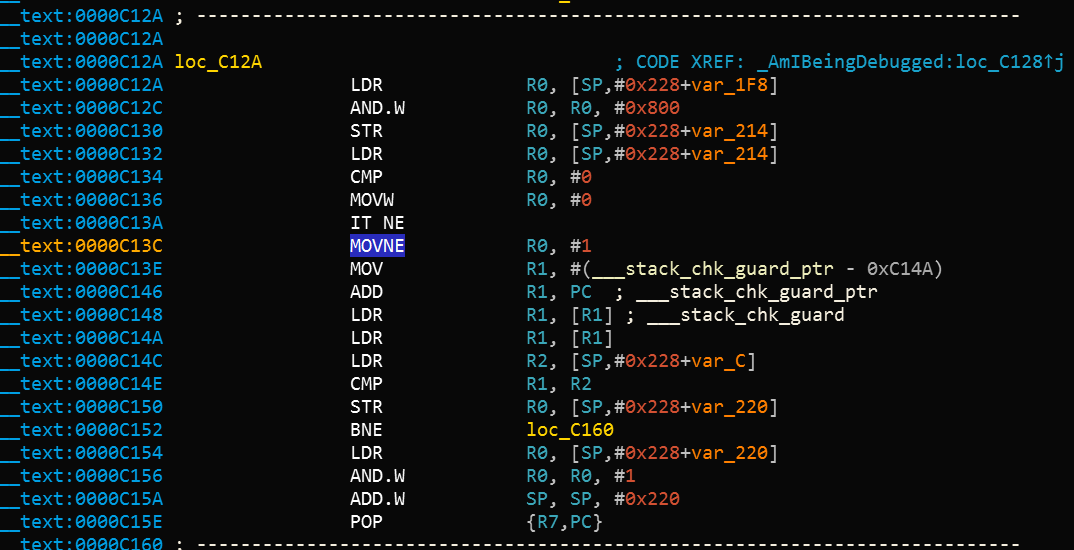
iOS Anti-Reversing Defenses - OWASP Mobile Application Security
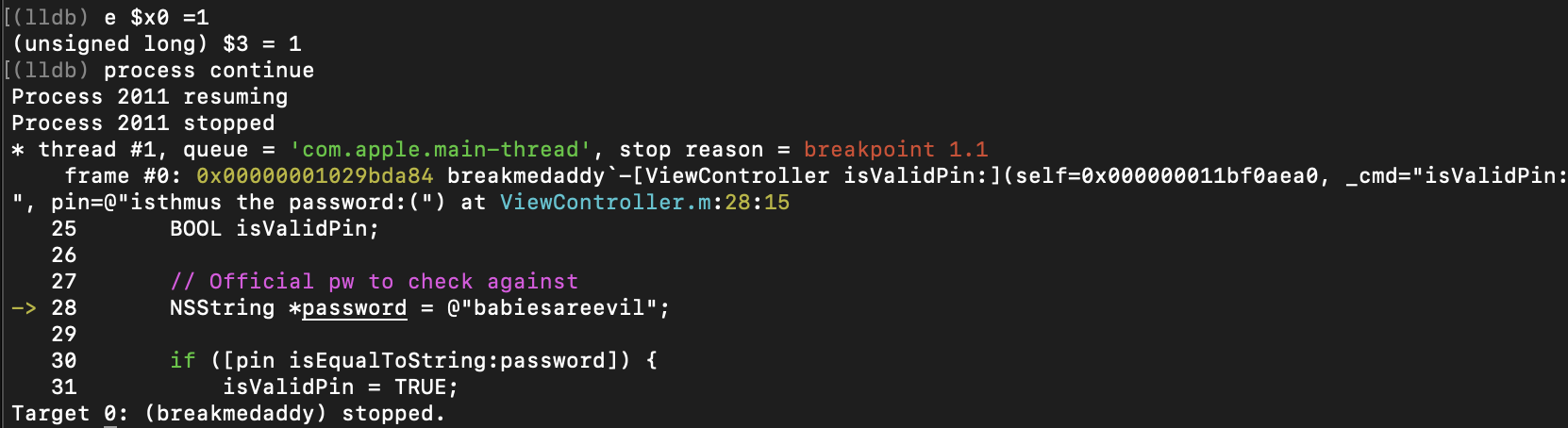
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I
de
por adulto (o preço varia de acordo com o tamanho do grupo)







