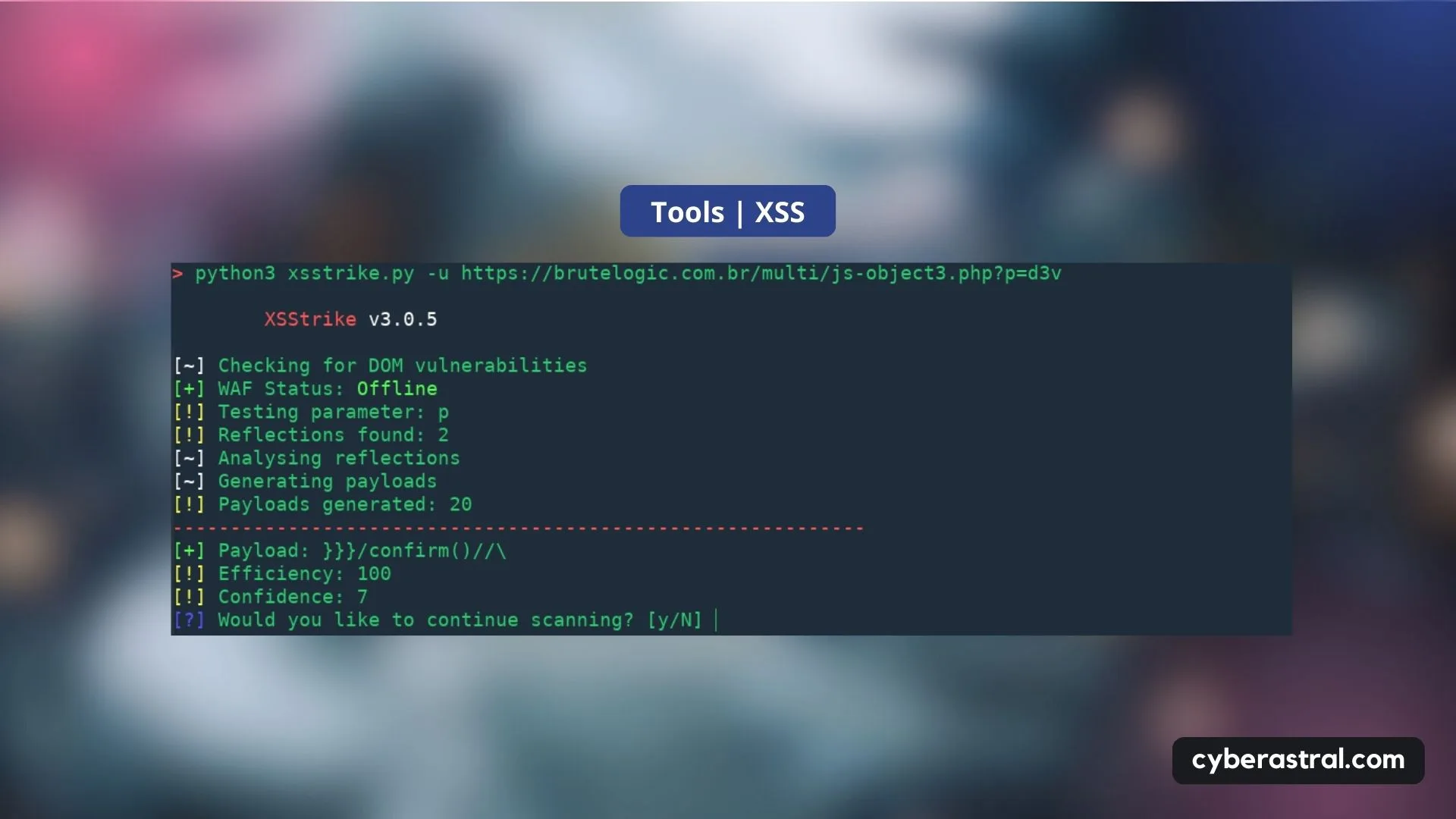
6.4: Exploitation tools (Pt 1)
Por um escritor misterioso
Descrição

6.4L: Long List of Failures - Diesel World

Computer security - Wikipedia
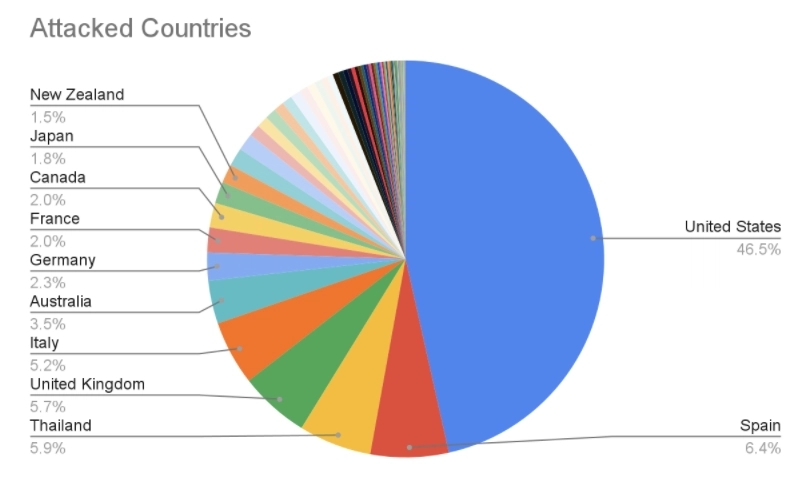
The most exploited vulnerabilities in 2022

Prevalence of anxiety and post-traumatic stress (PTS) among the parents of babies admitted to neonatal units: A systematic review and meta-analysis - eClinicalMedicine

Human Rights Crisis: Abortion in the United States After Dobbs

Unboxing BusyBox - 14 new vulnerabilities uncovered by Claroty and JFrog
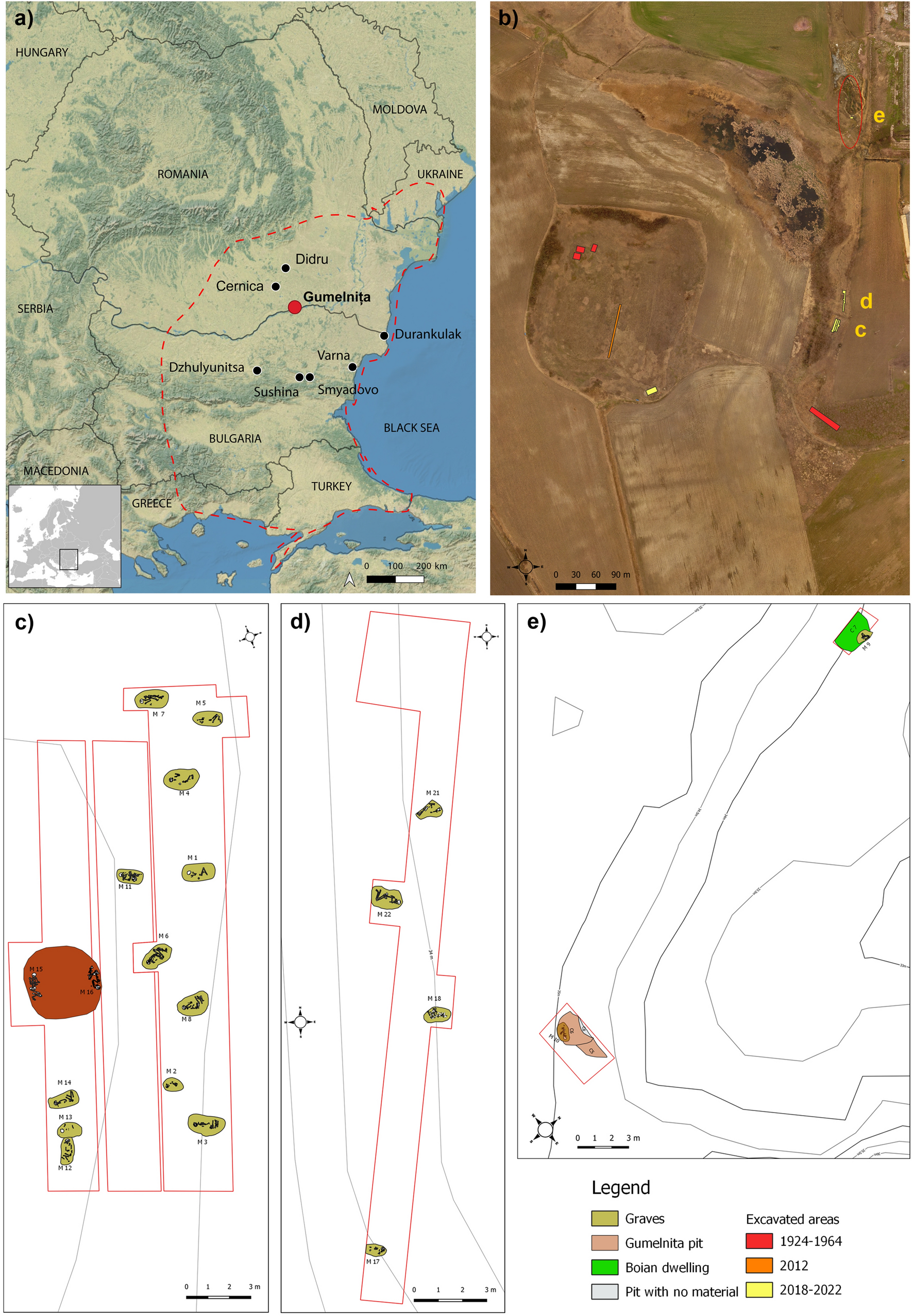
Unravelling the resilience of the KGK VI population from the Gumelnița site (Romania) through stable isotopes
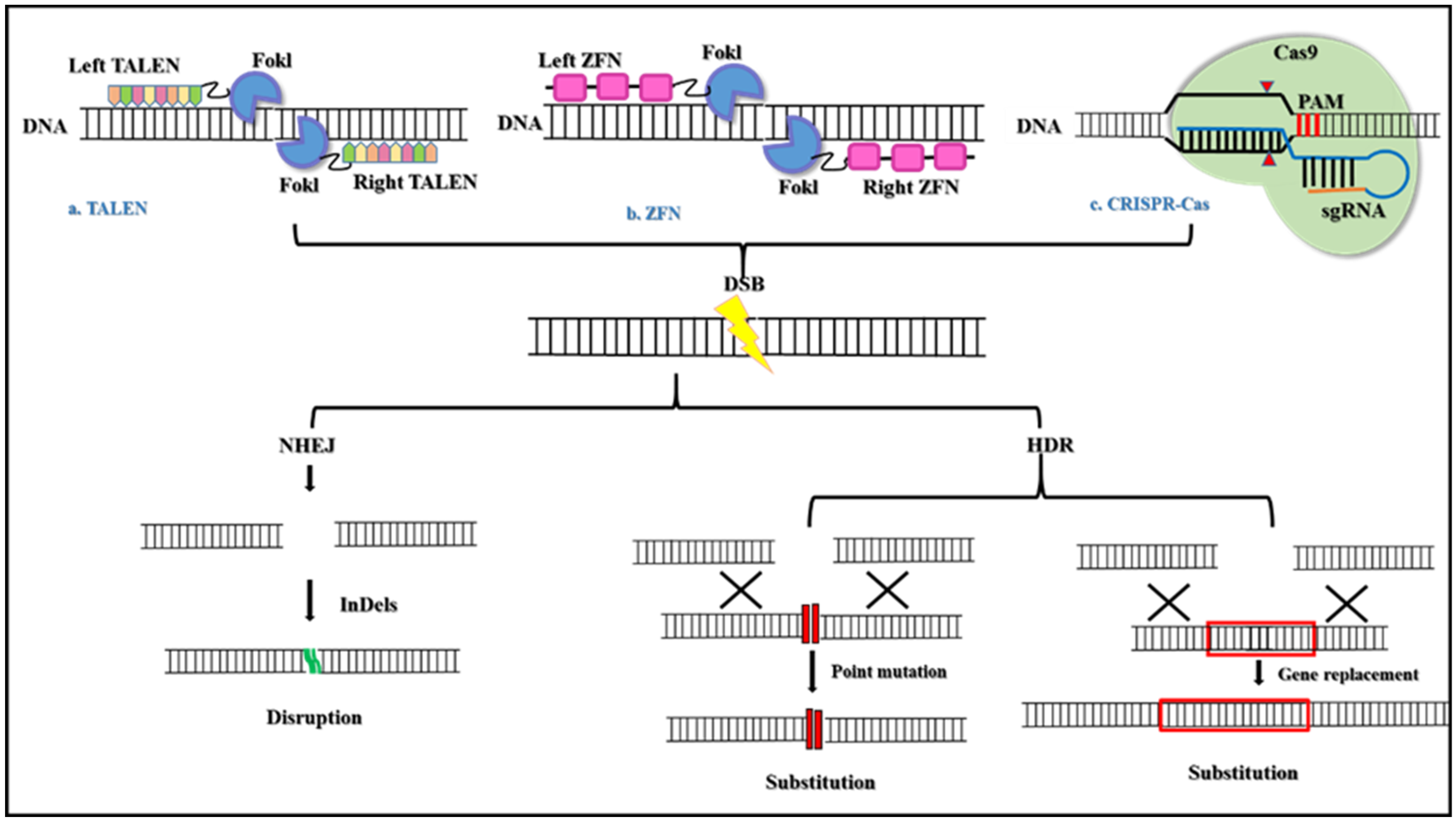
Pharmaceuticals, Free Full-Text

Experts released PoC exploit for MOVEit Transfer CVE-2023-34362
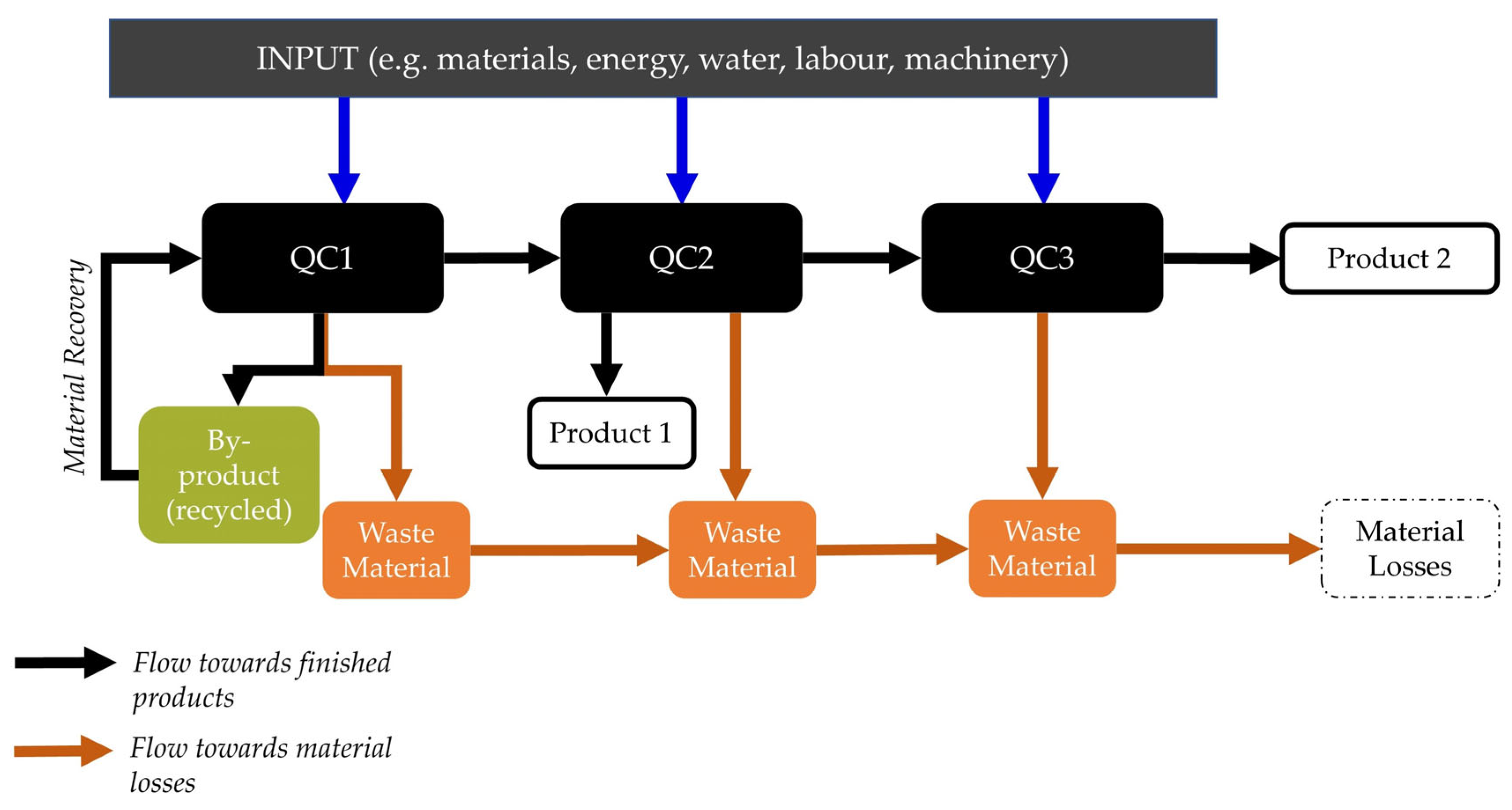
Clean Technol., Free Full-Text
KC has over 100 crypto ATMs, mostly in low-income neighborhoods

5Ghoul flaws impact hundreds of 5G devices with Qualcomm, MediaTek chips

HHP Racing & BES 7.2L 440ci (6.4L Based) Stroker Hemi Short Block
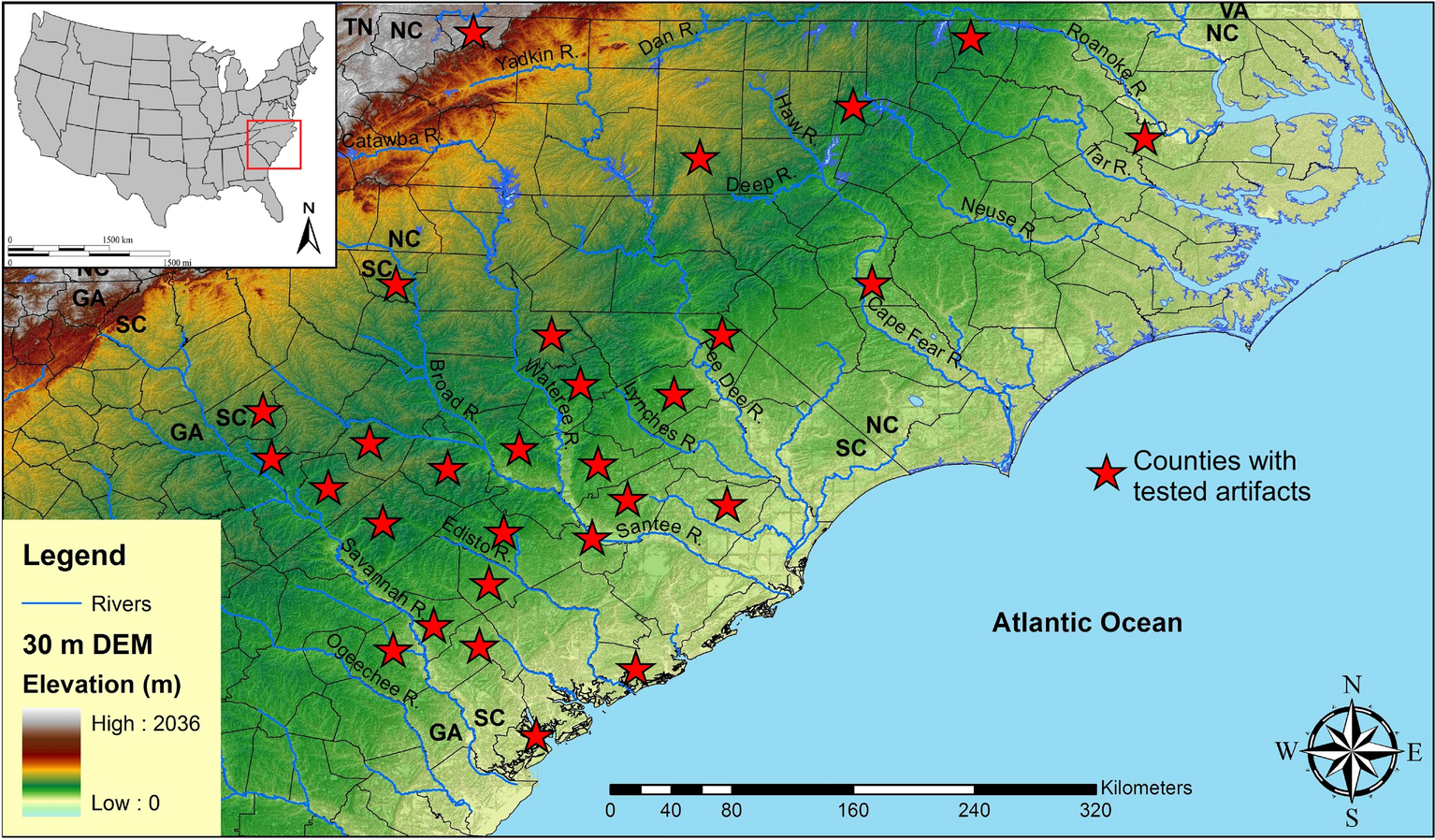
Paleoamerican exploitation of extinct megafauna revealed through immunological blood residue and microwear analysis, North and South Carolina, USA
de
por adulto (o preço varia de acordo com o tamanho do grupo)